Ransomware Report
You can check the latest ransomware information.
- title
- Kasper(Biobio) ransomware
- Registration date
- 2024-12-24
- views
- 1468
[ Kasper (Biobio) ransomware ]
[Virus/malicious code activity report: Kasper (Biobio) ransomware]
We are aware of a security breach that is believed to be in the form of Kasper (Biobio) ransomware
. We would like to provide the following information and warnings regarding the situation.
Kasper(Biobio) ransomware
The ransomware is called Kasper and it appears to be changing the filename.extension.Biobio of all files.
How it works
File version
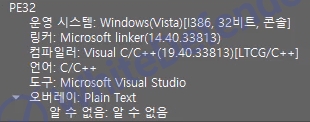
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This ransomware, written in C++, is designed to operate flexibly in various environments through multi-mode support. It receives additional parameters when running and activates an operation mode suitable for a specific situation. It prevents inefficient use of resources by preventing duplicate executions within the same system using mutexes, and the attack target is not limited to the PC's general drives but also extends to removable storage devices and network paths, which can cause particularly greater damage in network-based environments.
After the encryption task is completed, shadow copies are deleted through a command via cmd, and the system's Recycle Bin data is completely deleted, preventing the user from attempting to recover data. This seems to be an attempt to disable existing backup or data recovery tools. Finally, the ransomware completely deletes itself from the system, making forensic analysis and sample acquisition difficult. This self-deleting mechanism lowers the possibility of detection by leaving no traces, and serves to delay analysis.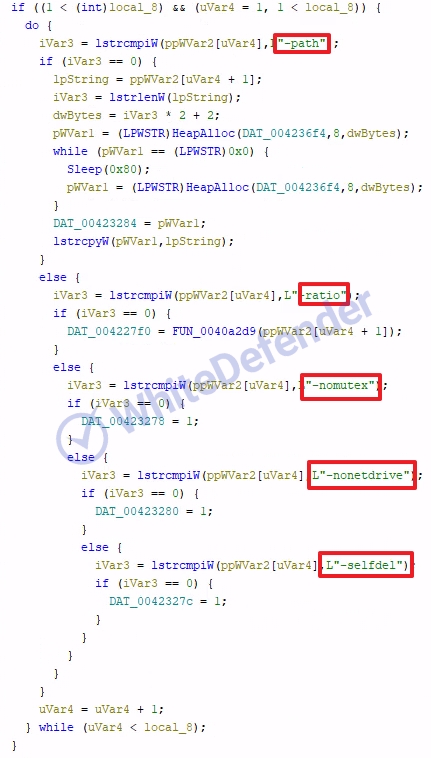
[Figure 3 Multi-mode support through parameters according to situation]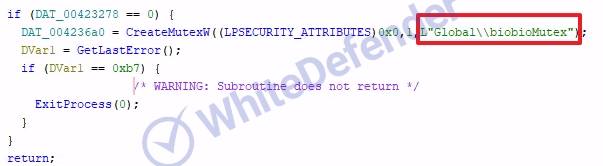
[Figure 4 Duplication Prevention Mutex]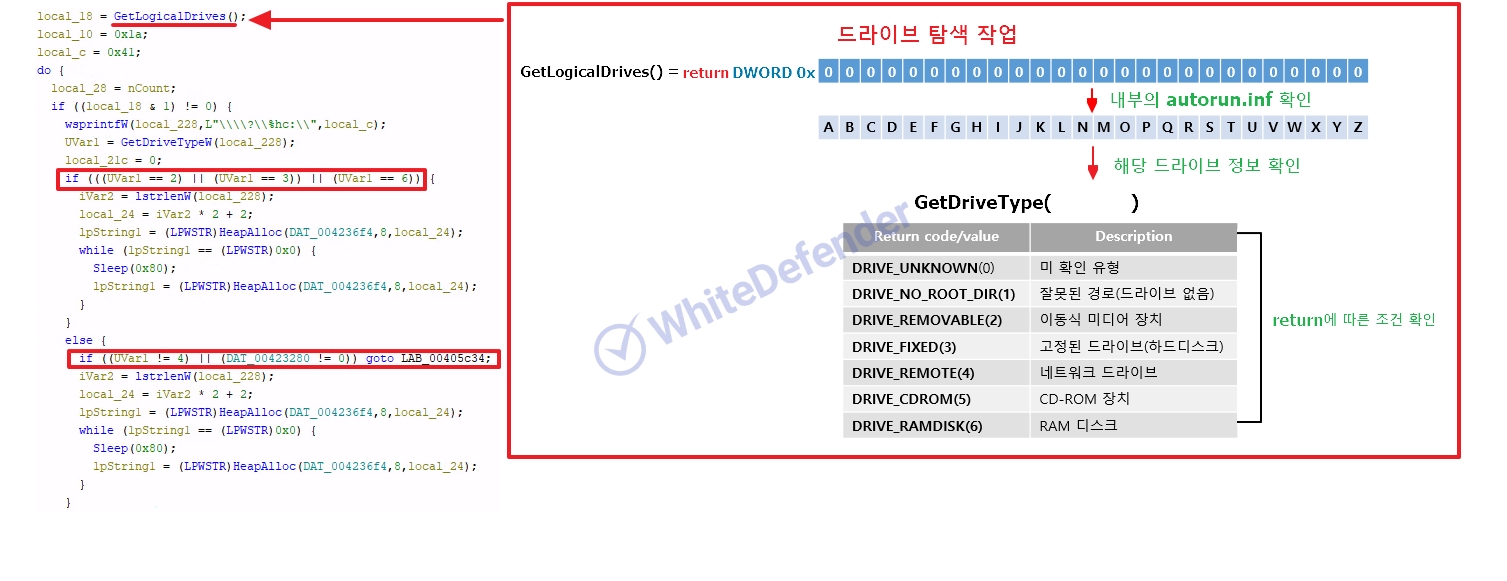
[Figure 5 Drive attack on all paths]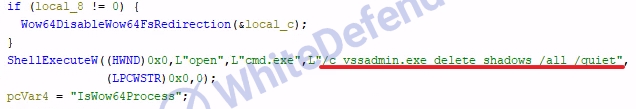
[Figure 6 Deleting Shadow Copy]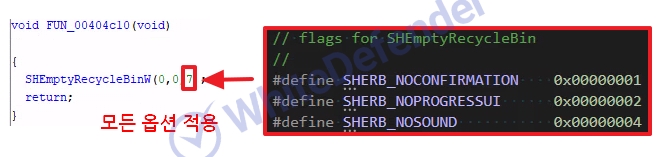
[Figure 7 Emptying the entire trash]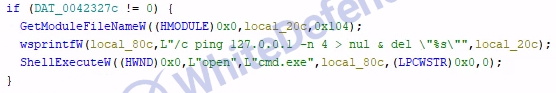
[Figure 8 Deleting ransomware executable file]
Infection results
The guide file is created in each folder location with the name < biobio ransomware.txt >, and each encrypted file is changed to < file name. extension. Biobio >. After encryption is complete, run the txt note.
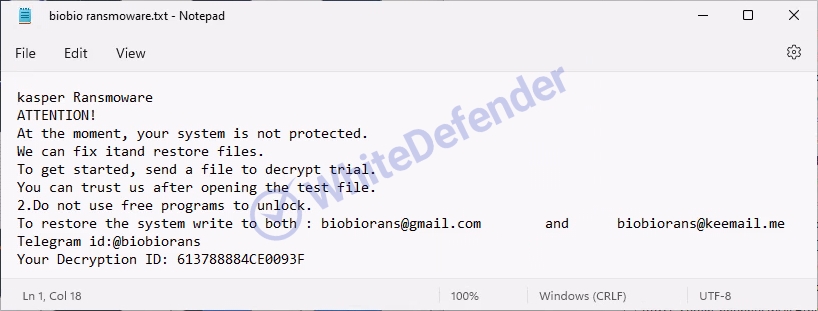
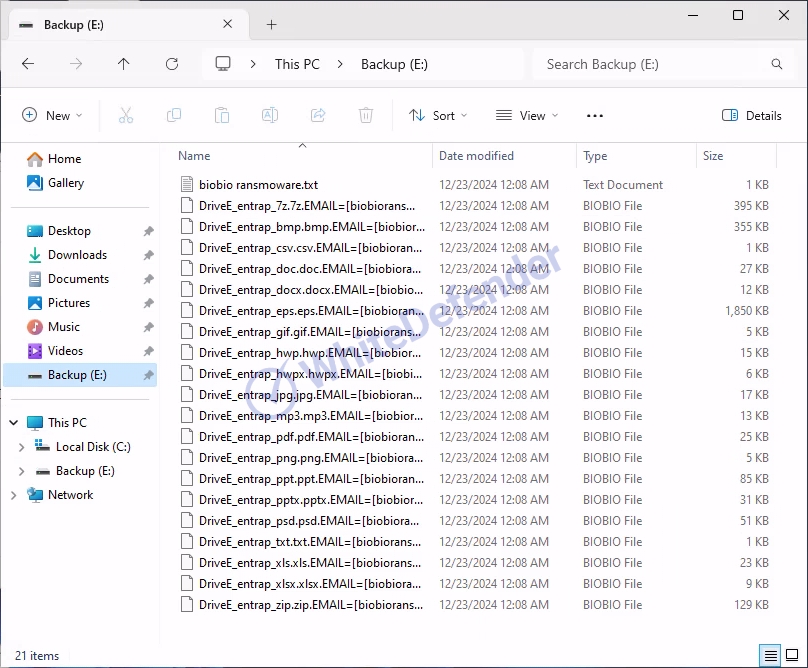
[Figure 9 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
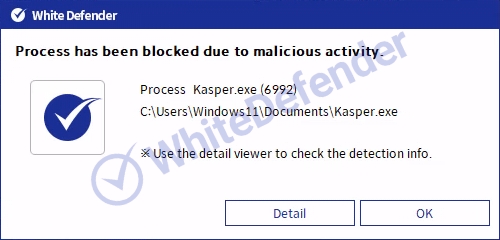
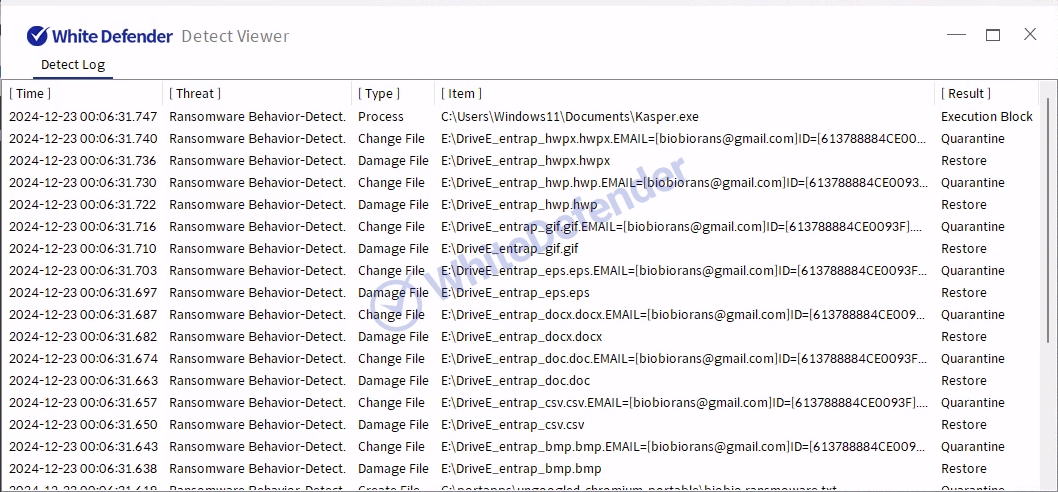
[Figure 10 Blocking Message]
Go to the Kasper(Biobio) blocking video

- Previous post
- Encp ransomware
- next post
- TX Ransomware

