Ransomware Report
You can check the latest ransomware information.
- title
- Analysis of DarkyLock, a ransomware (variant) disguised as an executable file
- Registration date
- 2022-08-01
- views
- 39604
[DarkyLock ransomware]
[Virus/malware activity reported: DarkyLock ransomware]
A security breach believed to be in the form of ransomware DarkyLock ransomware has occurred. We would like to
confirm the situation and provide a warning as follows.
Virus/malware activity target items and information
DarkyLock ransomware is a variant of LockBit Black ransomware that disguises itself as a PuTTY executable file and tricks users into performing malicious actions.
How it works
file version
This ransomware is a variant of LockBit 3.0 (commonly known as LockBit Black) and appears to be changing all files with the extension .darky. This is additional information about the file.
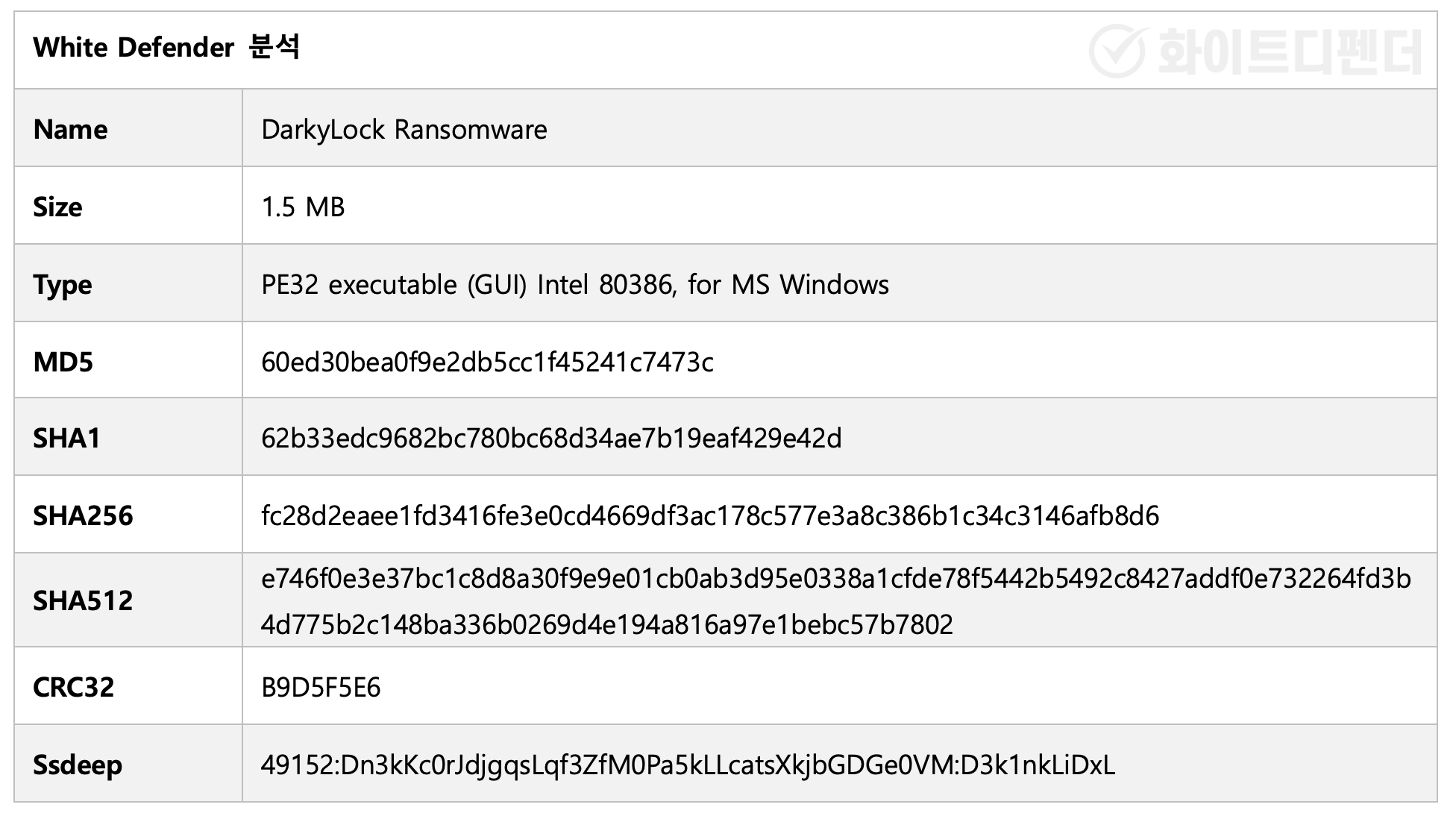
[Figure 1] File information
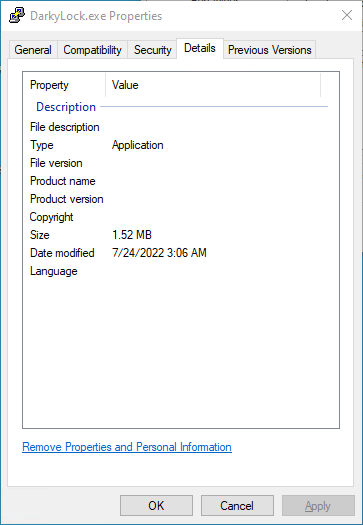
[Figure 2] File properties
behavioral process
- The file of ransomware disguised as a PuTTY file is disguised as a PuTTY executable file, and when executed, it receives and executes the normal PUTTY.EXE executable file in AppDataLoacalTemp and E_WIN.exe that executes malicious actions. The user sees PuTTY's normal execution screen and malicious activity takes place in the background.
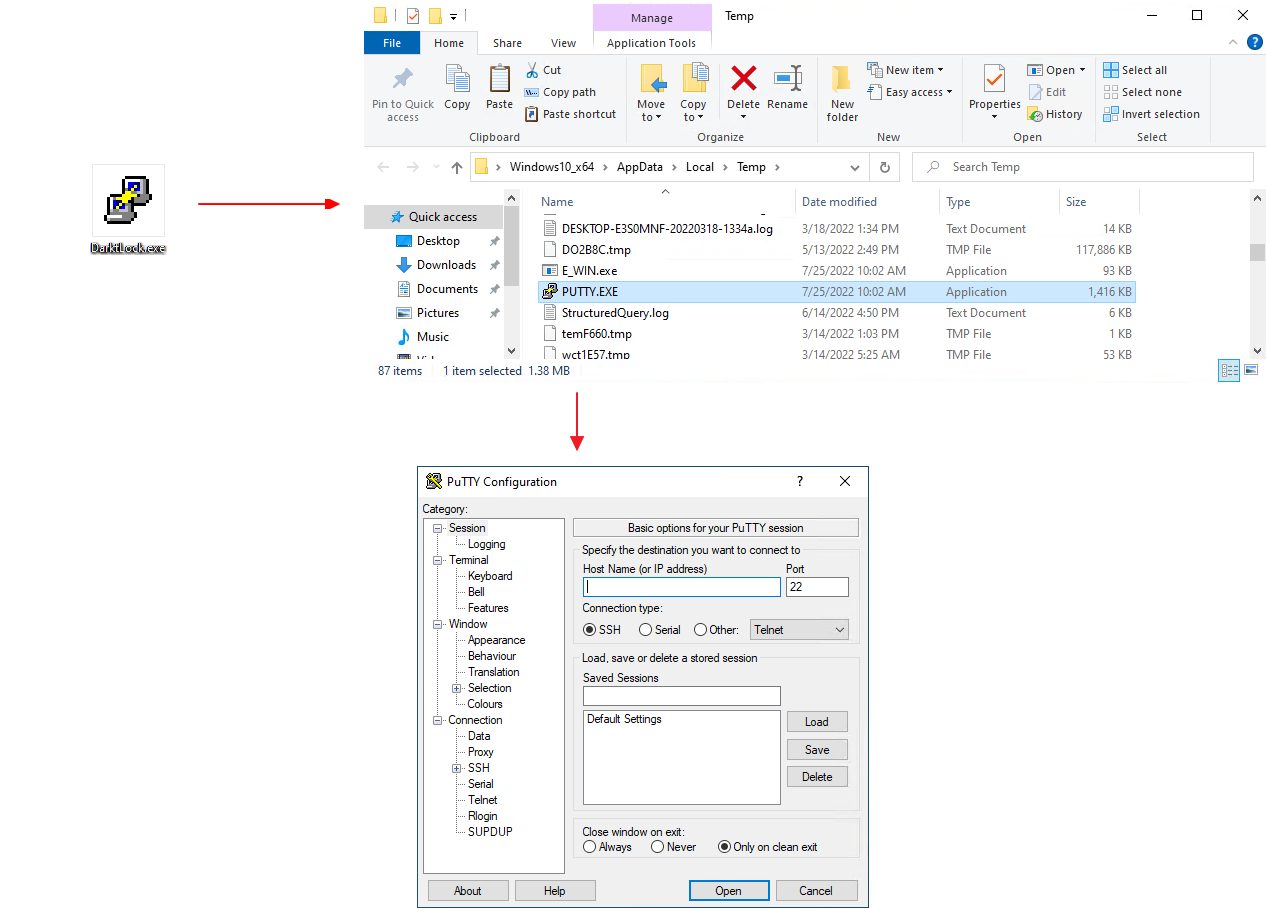
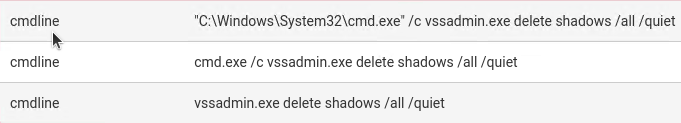
[Figure 2] Camouflage screen during action process - Deleting Shadow Copies Deletes shadow copies to make recovery of encrypted data difficult.
[Figure 3] Startup program registry registration - Target Drives Use GetLogicalDrives to target all drives except A drive (floppy disk), which also includes network drives.
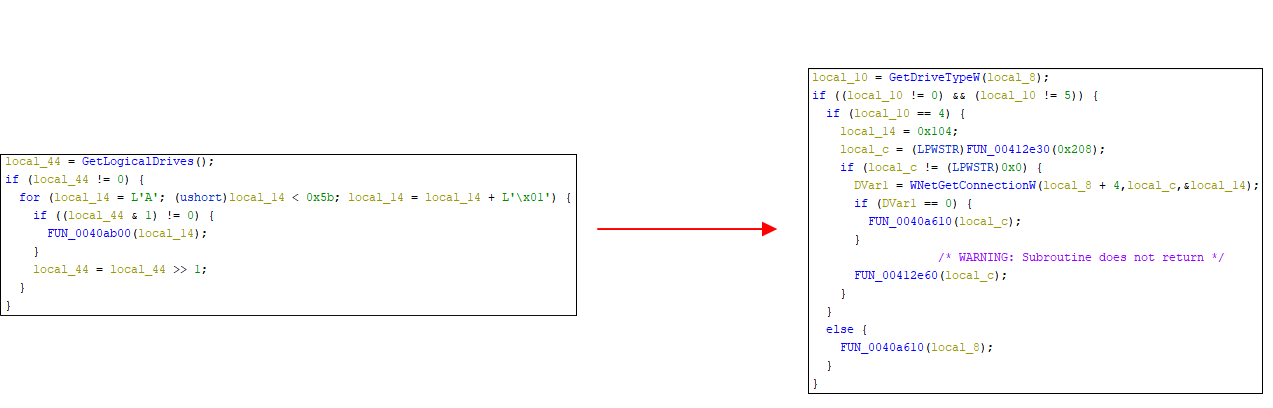
[Figure 4] Ransomware internal code
<Source: https://docs.microsoft.com/en-us/windows/win32/api/fileapi/nf-fileapi-getdrivetypea>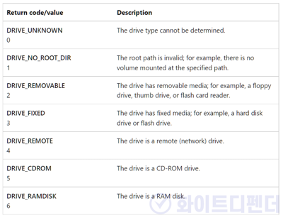
[Figure 5] Reference material - Duplicate execution prevention mutex information
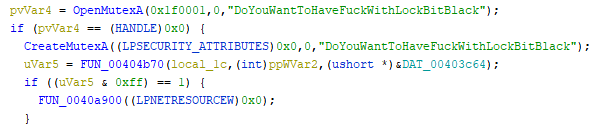
[Figure 6] Mutex information
Appearance and contents after infection (ransom note)
The information file is created in each folder with the name Restore-My-Files.txt, and when encryption is performed, the files are changed to <encrypted file name.darky>.
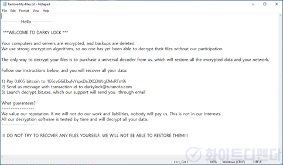
[Figure 7] .txt file ransom note screen
[Figure 8] Ransom note image
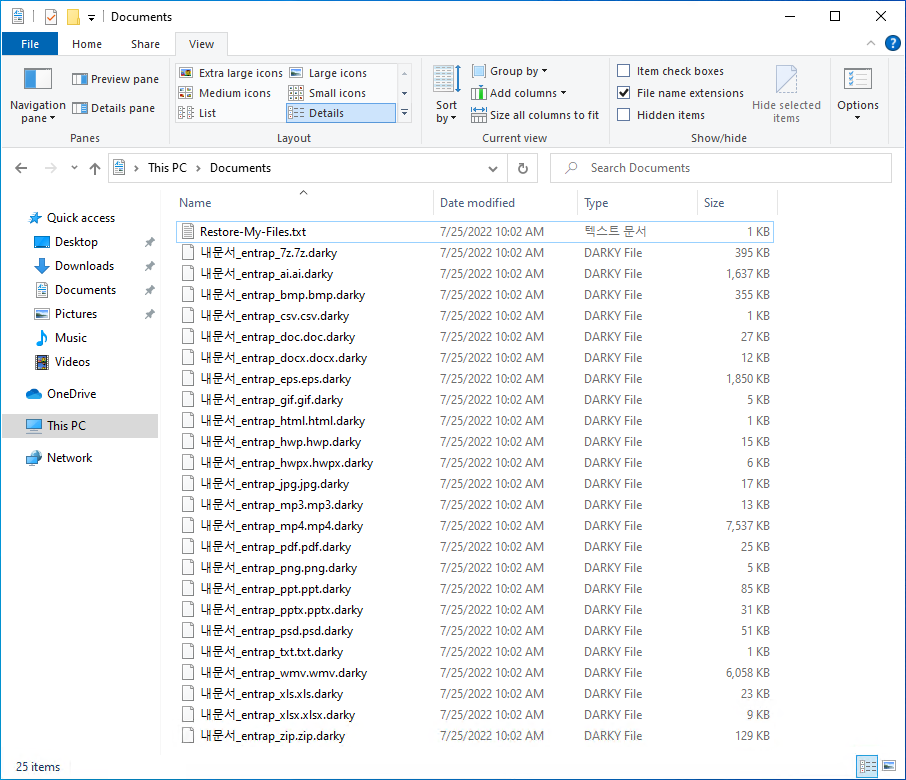
[Figure 9] Extension changed after infection
White Defender compatible
Diagnosis
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
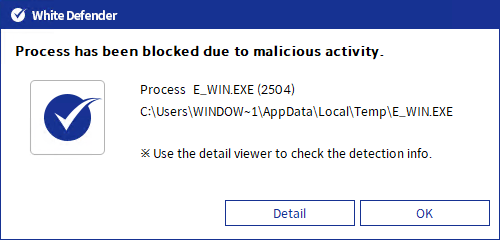
[Figure 10] Malicious activity blocking message
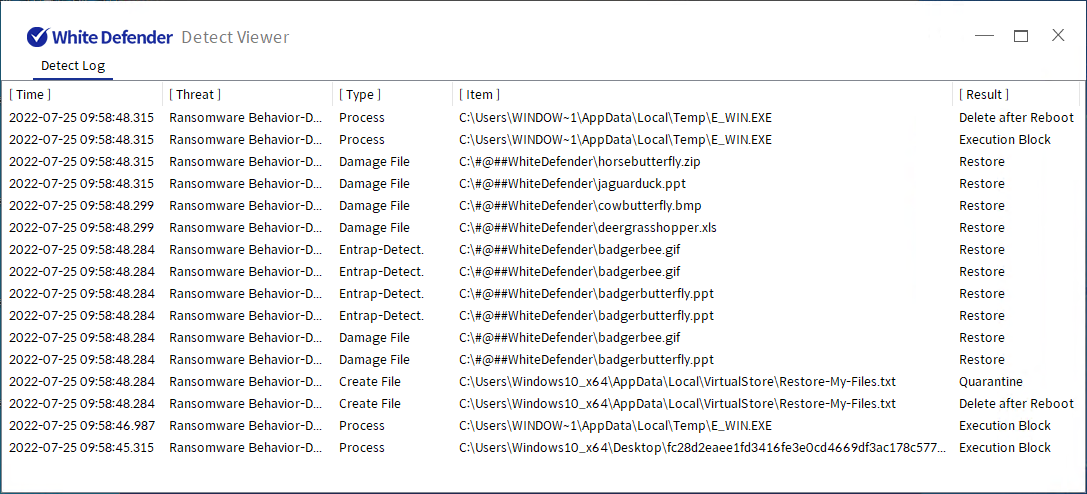
[Figure 11] Blocking log
Watch DarkyLock blocking video


