Ransomware Report
You can check the latest ransomware information.
- title
- NoCry ransomware
- Registration date
- 2025-09-12
- views
- 53
[ NoCry ransomware ]
[Virus/Malware Activity Reported: NoCry Ransomware]
We are aware of a security breach suspected to be a NoCry ransomware attack.
We would like to provide the following information and warning regarding the situation.
NoCry ransomware
The ransomware is called NoCry and appears to be changing the filename and extension of all files to .NoCry.
How it works
File version
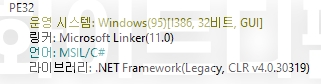
[Figure 1 Ransomware executable file compiler information]
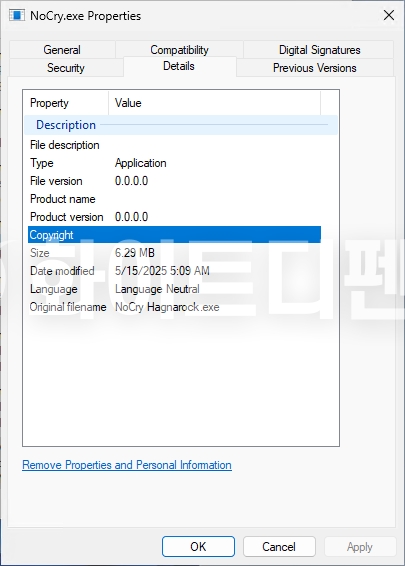
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
NoCry ransomware is a .NET malware based on the Chaos family. The initial executable file is svchost.exe, which is re-executed from the Roaming folder. If the PCs Windows default language is a specific language (Turkish), it will not be executed. It uses technology to prevent multiple program executions before processing and to prevent re-encryption when encryption is complete. To make recovery difficult during encryption, it deletes shadow copies and backup catalogs, and disables Windows Restore and error notification functions. It checks the names of the data recovery-related processes owned by the ransomware, stops the service, and disables the task manager. This ransomware follows the typical characteristics of the Chaos family, focusing on blocking recovery and interfering with user response in addition to simple encryption.
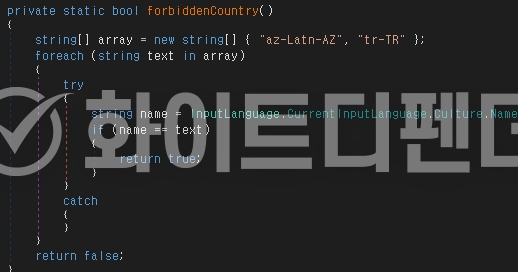
[Figure 3 Static internal code that does not work in a specific national language (Turkish)]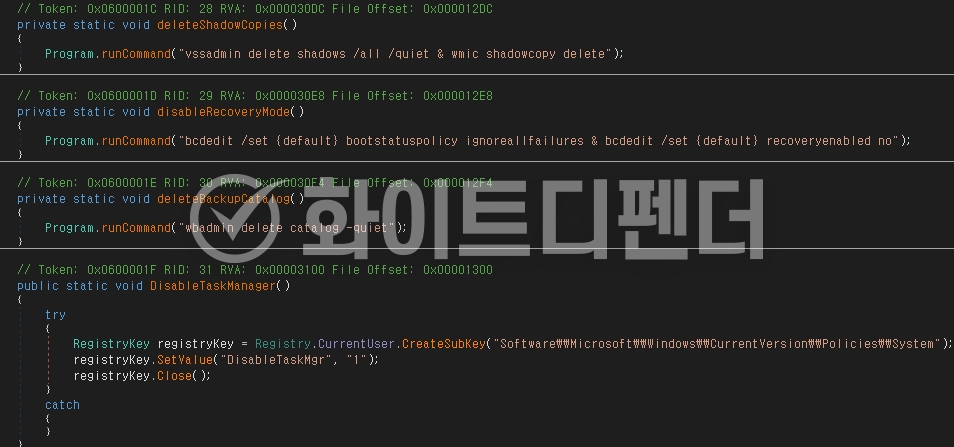
[Figure 4 Commands used in static internal code]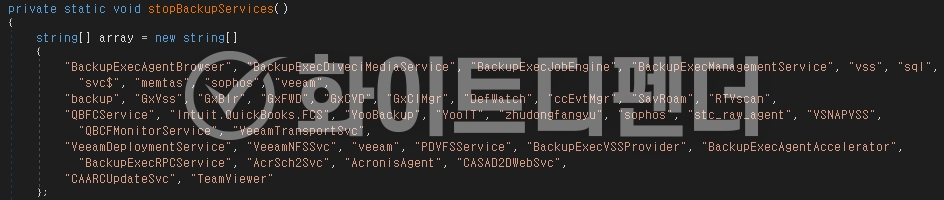
[Figure 5: Data-related program name string identified by ransomware]
Infection results
After encryption is complete, a guide file is created in each folder with the name read_it.txt, and each encrypted file is changed to <file name.extension.NoCry>.
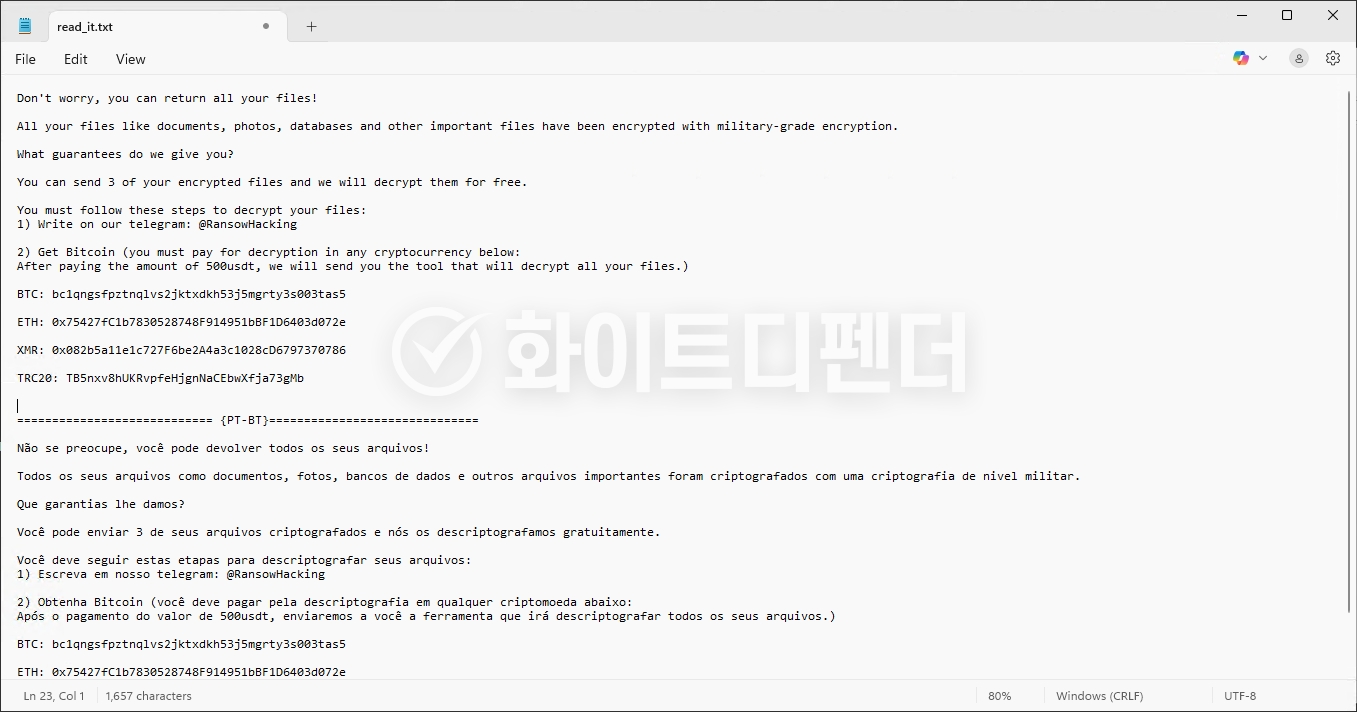
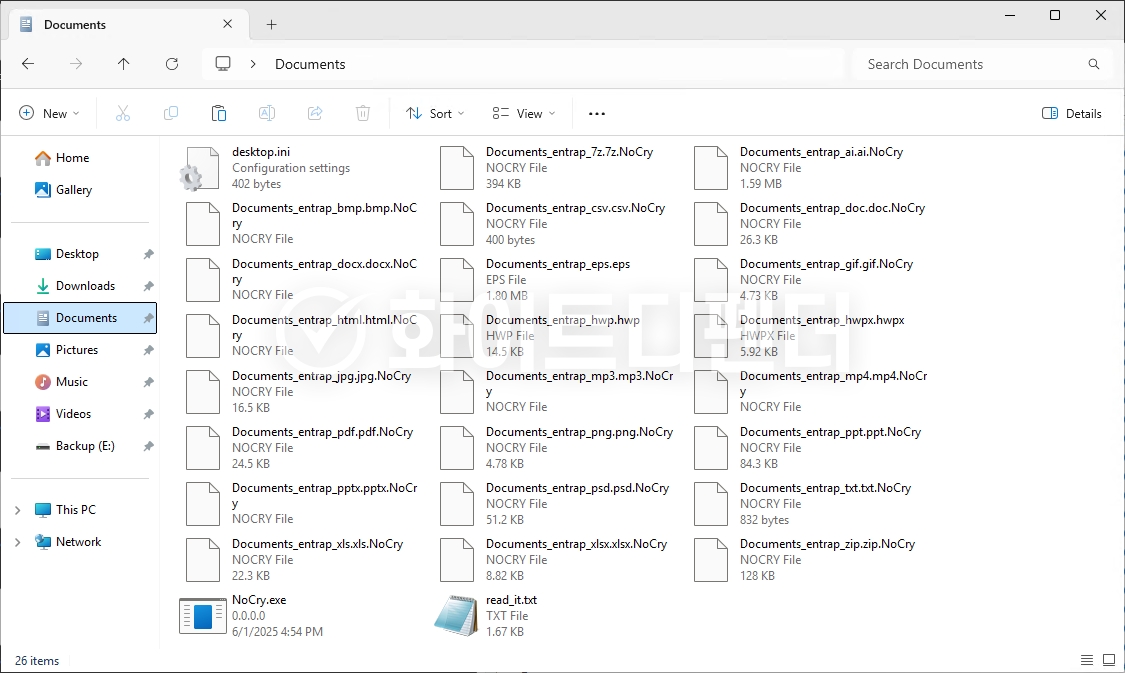
[Figure 6 Infection Results]
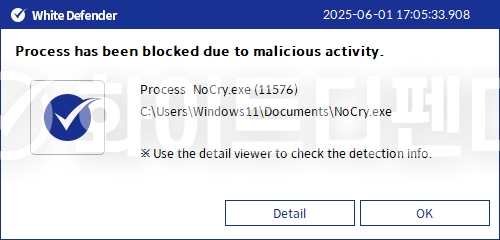
White Defender response
It also supports real-time automatic restoration of files that were encrypted before WhiteDefender ransomware malicious actions and blocking.
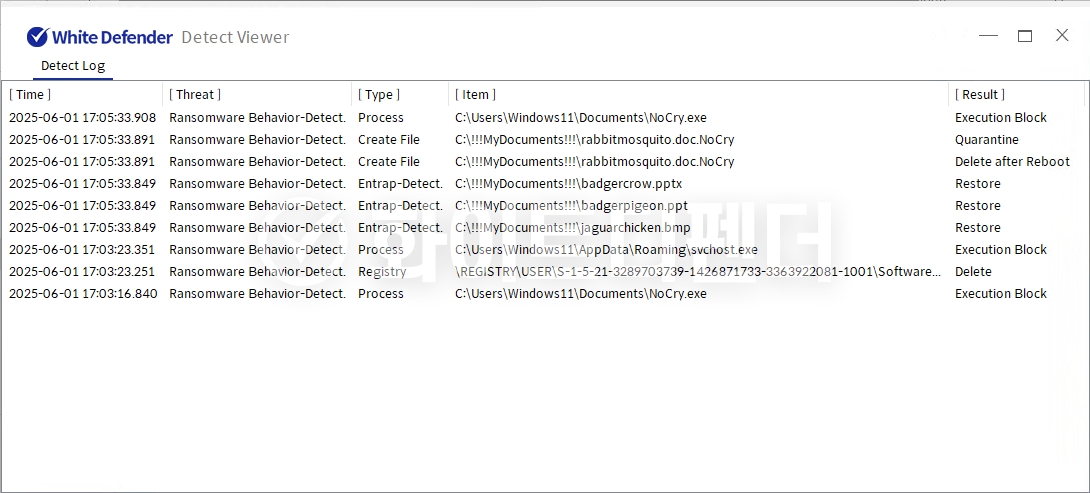

[Figure 7 Blocking Message]
Watch the NoCry blocking video

- Previous post
- No previous posts
- next post
- Nqix ransomware

