Ransomware Report
You can check the latest ransomware information.
- title
- Cyborg ransomware
- Registration date
- 2025-08-16
- views
- 1684
[ Cyborg ransomware ]
[Virus/Malware Activity Reported: Cyborg Ransomware]
We are aware of a security breach suspected to be a form of Cyborg ransomware and
would like to provide the following information and warning regarding the situation.
Cyborg ransomware
The ransomware is called Cyborg and appears to be changing all files to the file name .Cyborg1.
How it works
File version
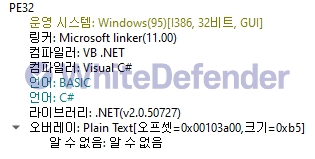
[Figure 1 Ransomware executable file compiler information]
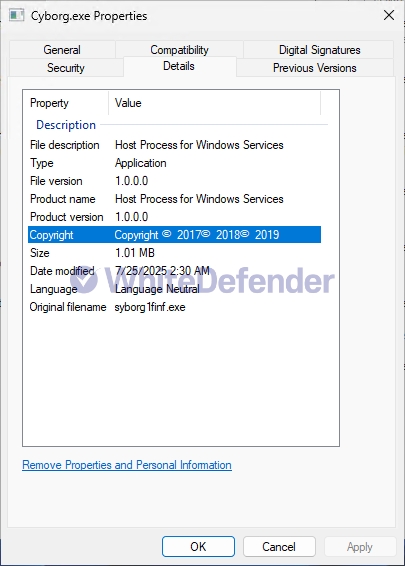
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This ransomware was developed in the .NET-based VB language and employs various obfuscation techniques to complicate analysis. Key logic and strings within the code are encrypted in a static state, decrypted and executed only at runtime. This structure is a typical technique used to hinder static analysis and evade detection.
Furthermore, while some variants of the same family have been found to change the user's desktop after infection, this feature was disabled in the sample analyzed this time. This is likely due to differences in build options, the test version, or functional limitations resulting from distribution purposes.
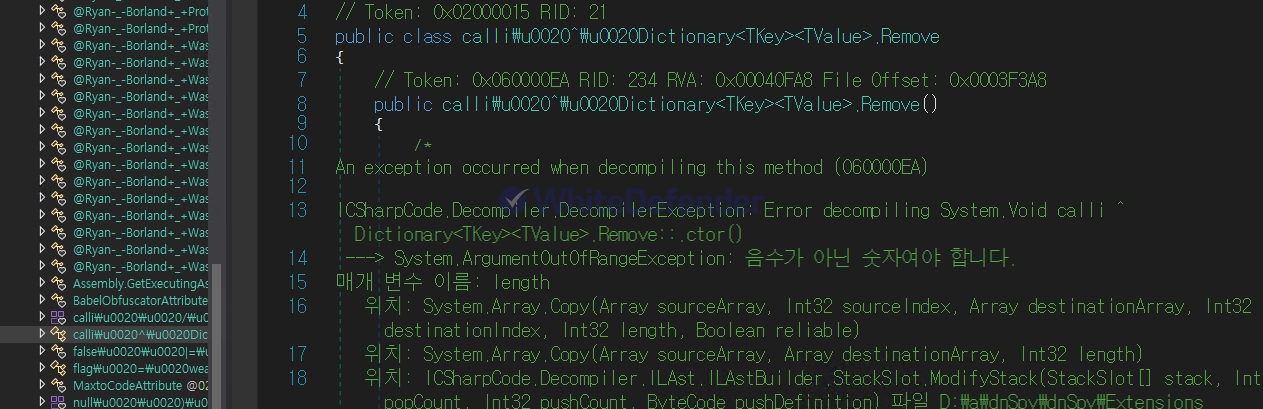
[Figure 3 Obfuscated internal static code]
Infection results
After encryption is complete, a guide file is created in each folder location with the name Cyborg_DECRYPT.txt, and each encrypted file is changed to < file name. extension. Cyborg1 >.
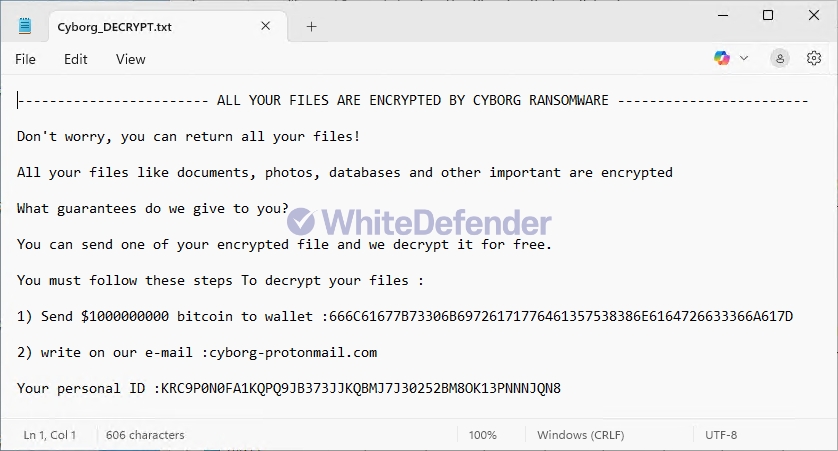
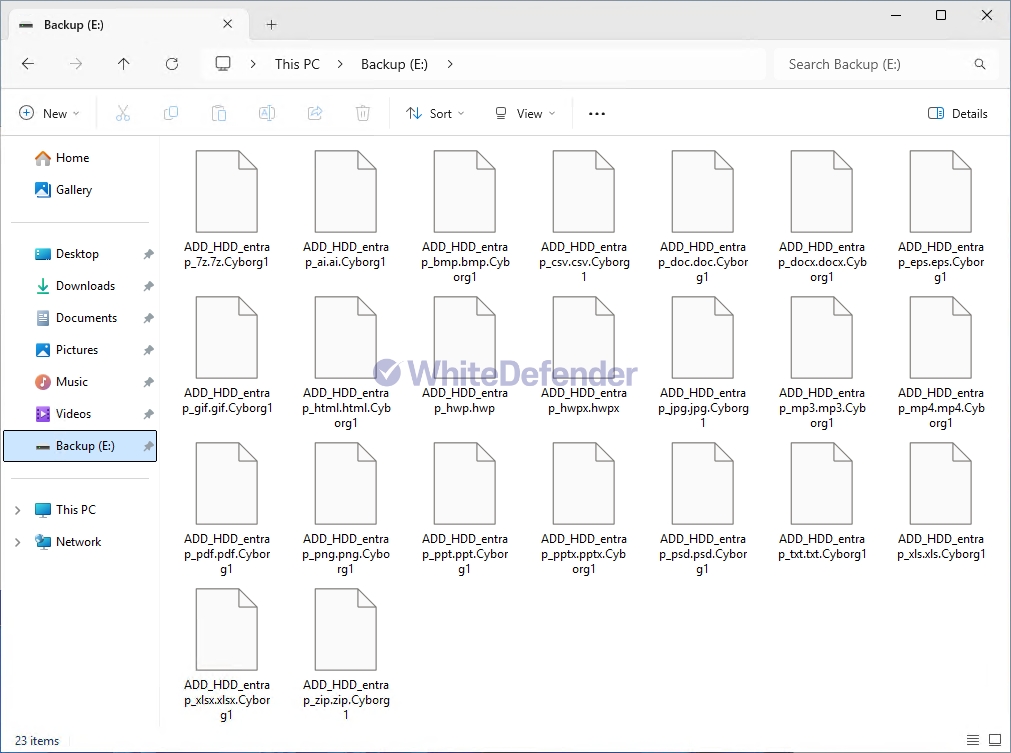
[Figure 4 Infection Results]
White Defender response
It also supports real-time automatic restoration of files that were encrypted before WhiteDefender ransomware's malicious actions and blocking.
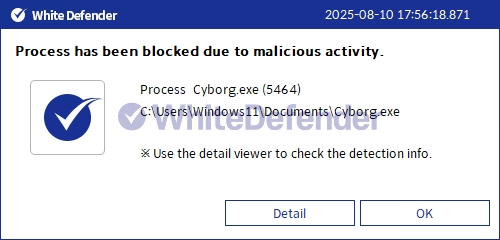
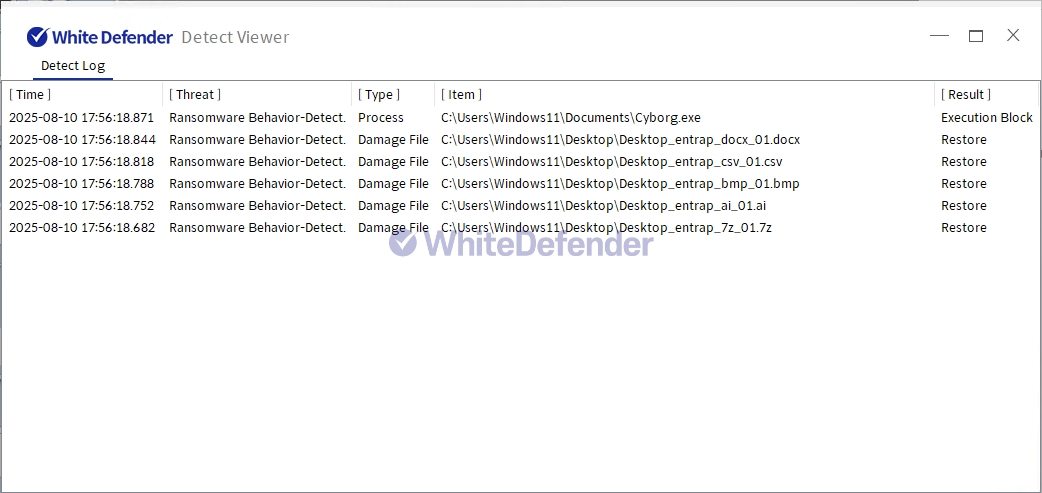
[Figure 5 Blocking Message]
Watch the Cyborg blocking video

- Previous post
- Nqix ransomware
- next post
- Ezdz ransomware

