Ransomware Report
You can check the latest ransomware information.
- title
- Ezdz ransomware
- Registration date
- 2025-08-10
- views
- 346
[ Ezdz ransomware ]
[Virus/Malware Activity Report: Ezdz Ransomware]
We are aware of a security breach suspected to be Ezdz ransomware and
would like to provide the following information and warning regarding the situation.
Ezdz ransomware
The ransomware is called Ezdz and appears to be changing all files to the file name .EZDZ.
How it works
File version
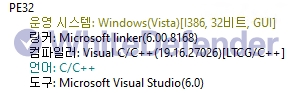
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This ransomware is a malware developed in C++. It utilizes various techniques to gain advanced system privileges and evade detection upon infection. First, during the execution phase, it utilizes a COM-based privilege escalation technique vulnerable to UAC (User Account Control) bypass to gain administrative privileges. This allows it to bypass tasks that may be restricted by security solutions or system policies. At the same time, it interprets strings used within the malware (e.g., commands, paths, file names, etc.) to dynamically adjust encryption targets and operating conditions.
After infection, the ransomware injects malicious code into the Windows system process svchost.exe. This technique evades detection by security products and disguises itself as a legitimate process, allowing it to perform encryption tasks without being detected by the system. Process injection is known to be a highly effective tactic, particularly in terms of endpoint detection and response (EDR) evasion, allowing attackers to remain stealthy within the system for extended periods of time.
Once the actual encryption process begins, this ransomware deletes all volume shadow copies, completely blocking any possibility of recovery. This prevents users or administrators from using the System Restore feature to restore data, and even if backup catalogs and recovery points exist, they are inaccessible.
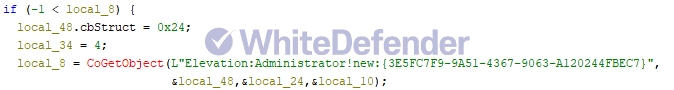
[Figure 3: Part of static code for UAC bypass via COM]
[Figure 4: Internal static code for deleting shadow copies]
Infection results
After encryption is complete, a guidance file named HELP_PC.EZDZ-REMOVE.txt is created in each folder location, and each encrypted file is changed to < file name. extension. EZDZ >.
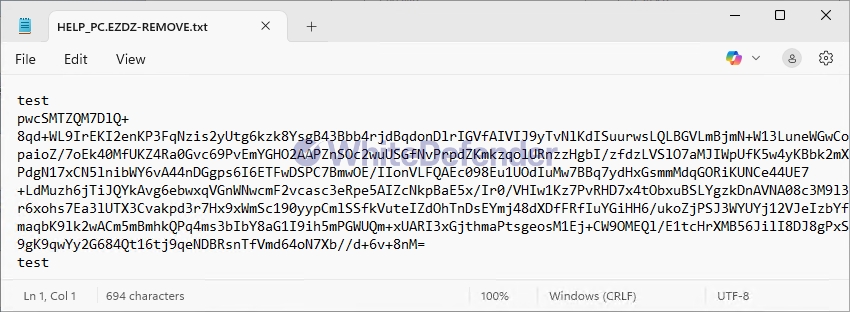
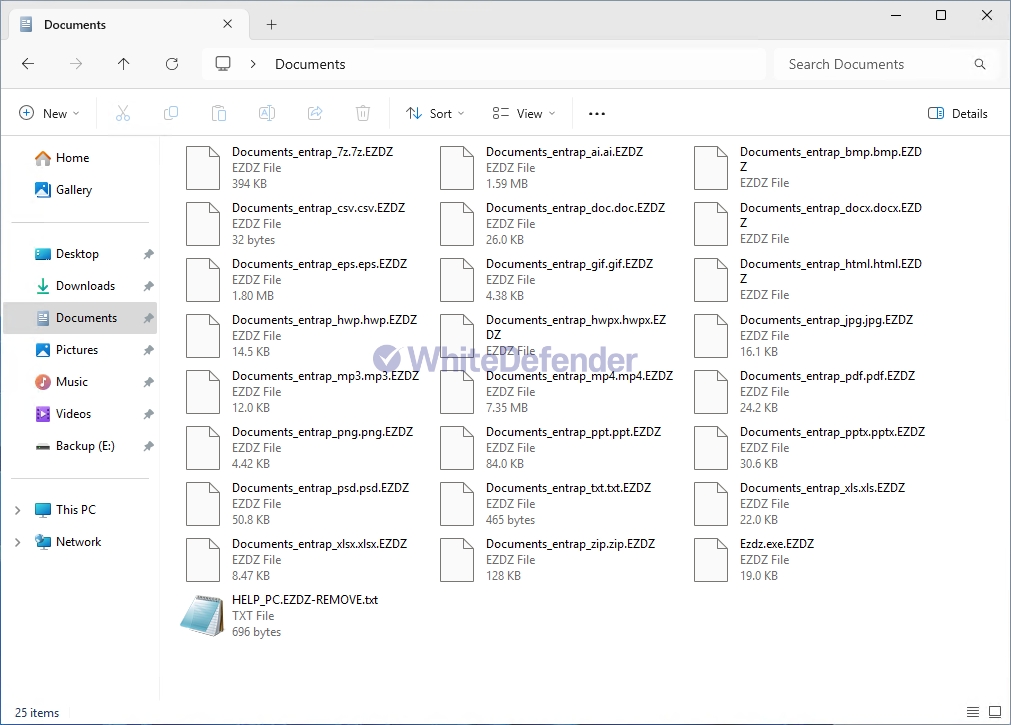
[Figure 5 Infection Results]
White Defender response
It also supports real-time automatic restoration of files that were encrypted before WhiteDefender ransomware's malicious actions and blocking.
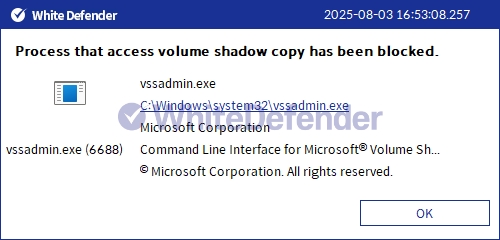
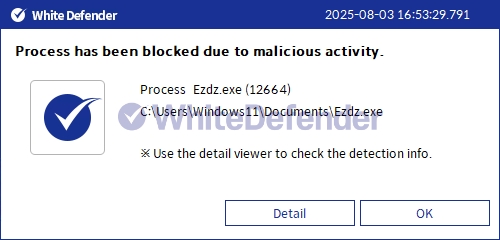
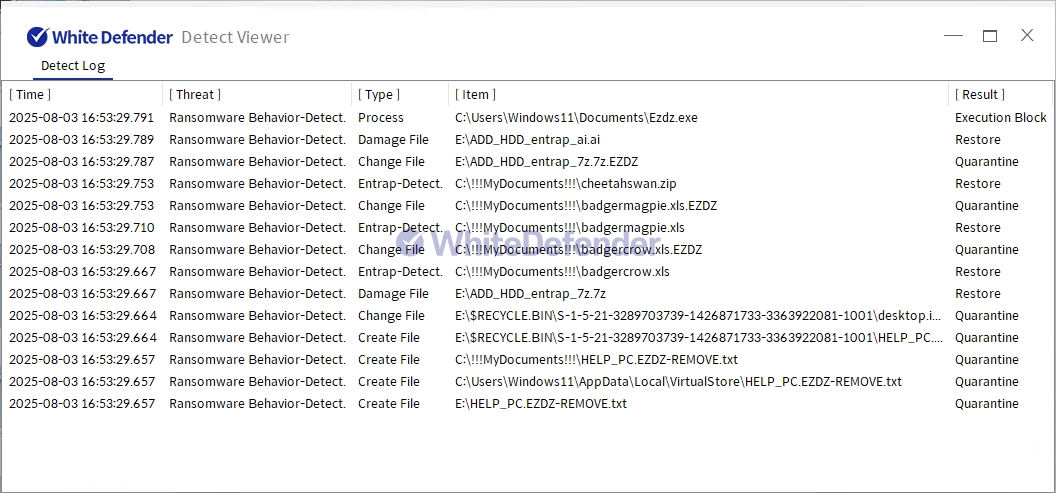
[Figure 6 Blocking Message]

- Previous post
- Cyborg ransomware
- next post
- Wannadie ransomware

