Ransomware Report
You can check the latest ransomware information.
- title
- Aoki ransomware
- Registration date
- 2025-08-10
- views
- 362
[ Aoki ransomware ]
[Virus/Malware Activity Report: Aoki Ransomware]
We are aware of a security breach suspected to be Aoki ransomware and
would like to provide the following information and warning regarding the situation.
Aoki ransomware
The ransomware is called Aoki and appears to be changing all files with the filename.extension.crypted_aoki@airmail_cc.
How it works
File version
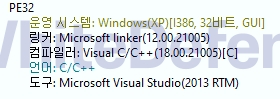
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
Aoki is a C++-based ransomware identified as a Globeimposter-related trope. The initially executed executable file is deleted, copied to the AppdataLocal location, and then re-executed. Because the ransomware registers itself in the current user's startup registry (RunOnce) before encryption, it will re-execute upon Windows login, even if it fails to execute immediately.
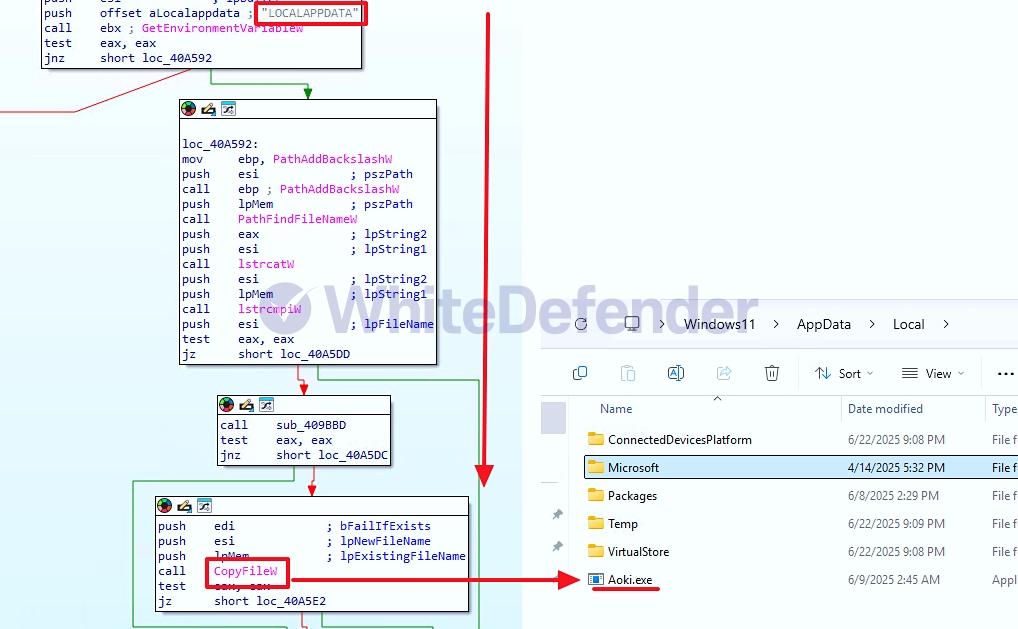
[Figure 3 Copy to LocalAppdata location and re-run]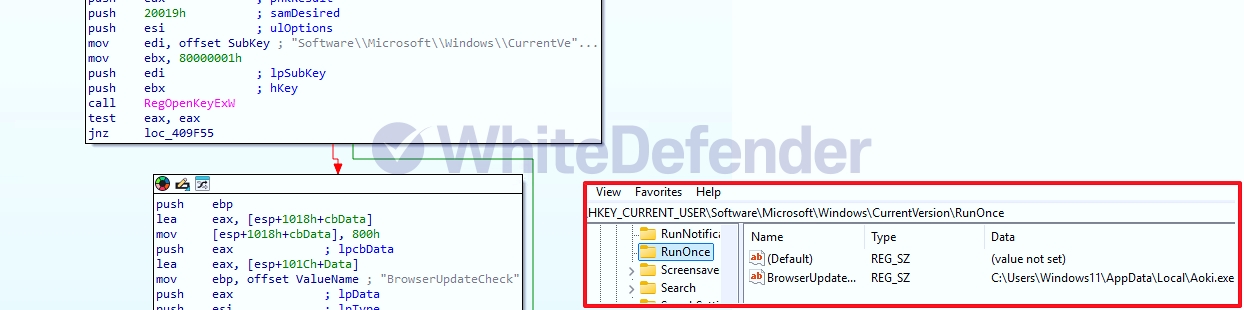
[Figure 4 2. Ransomware Information 2 - Registered in Startup Program]
Infection results
After encryption is complete, a guide file named how_to_back_files.html is created in each folder location, and each encrypted file is changed to < file name. extension. encrypted_aoki@airmail_cc >.
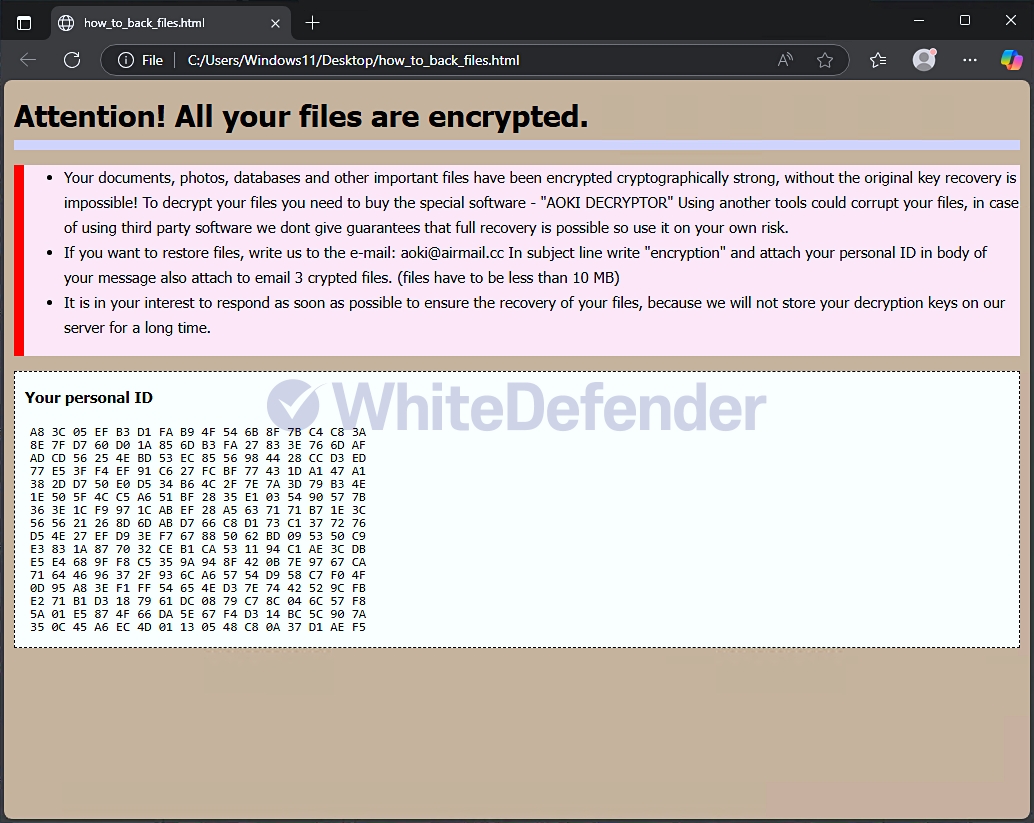
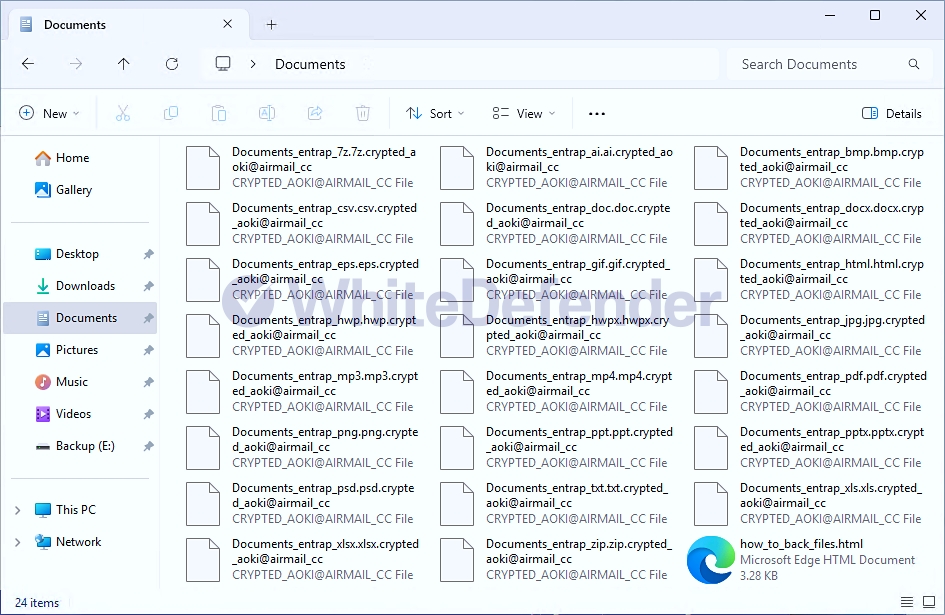
[Figure 5 Infection Results]
White Defender response
It also supports real-time automatic restoration of files that were encrypted before WhiteDefender ransomware's malicious actions and blocking.
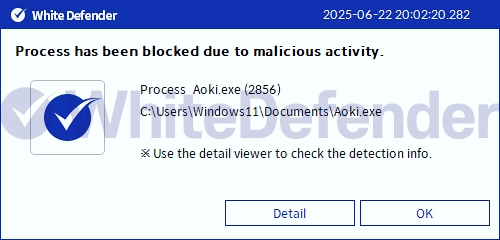
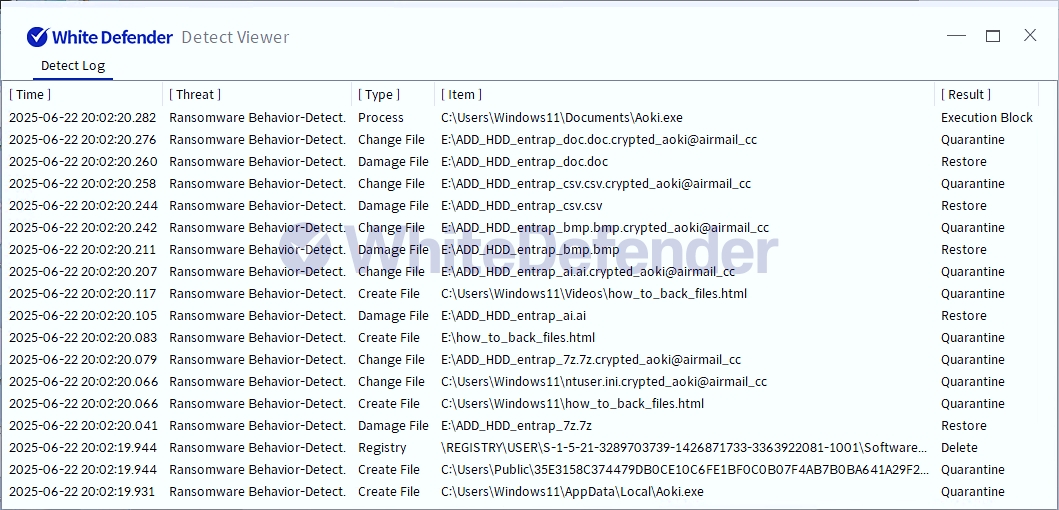
[Figure 6 Blocking Message]

- Previous post
- Wannadie ransomware
- next post
- Nnice ransomware

