Ransomware Report
You can check the latest ransomware information.
- title
- Nnice ransomware
- Registration date
- 2025-06-27
- views
- 197
[ Nnice Ransomware ]
[Virus/malicious code activity reported: Nnice ransomware]
A security breach suspected to be in the form of Nnice ransomware has occurred.
We would like to provide the following information and warning regarding the situation.
Nnice ransomware
The ransomware is called Nnice and it appears to be changing the filename.extension.xdddd of all files.
How it works
File version
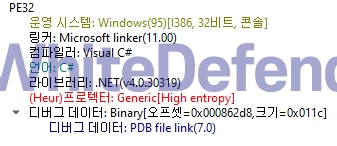
[Figure 1 Ransomware executable file compiler information]
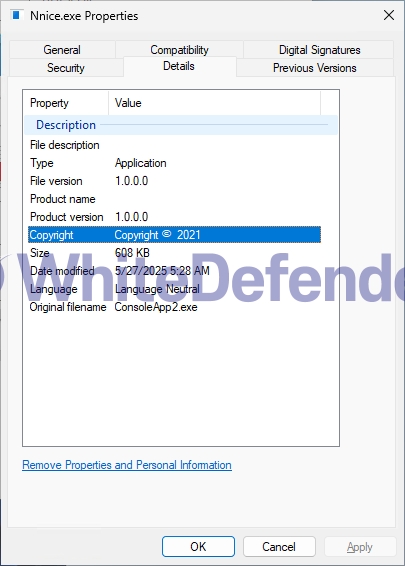
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
Nnice ransomware is a malware developed on a C#-based .NET platform, and has the characteristic of disabling the user system’s recovery function when infected. When encryption is complete, it deletes the system’s Volume Shadow Copy and Windows Backup Catalog, while also disabling the System Restore function and warning notifications displayed when an error occurs, significantly limiting the user’s ability to respond.
After encryption is complete, it copies its own executable file to the %LocalAppData% path with the name discord.exe and registers it in the startup program registry (HKCUSoftwareMicrosoftWindowsCurrentVersionRun) so that the ransomware can continue to run even after a system reboot.
In addition, through decompilation, it was confirmed that the ransomware had conditional logic or function names that determine whether to activate specific functions within the function control logic written in Spanish. This suggests that the attacker may have created it based on a Spanish-speaking development environment or builder, and it was analyzed as the creator's regional background or the use of a language-based builder tool.
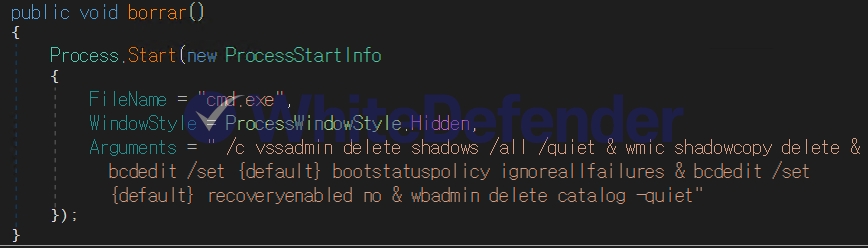
[Figure 3 Using specific cmd commands to make user data difficult]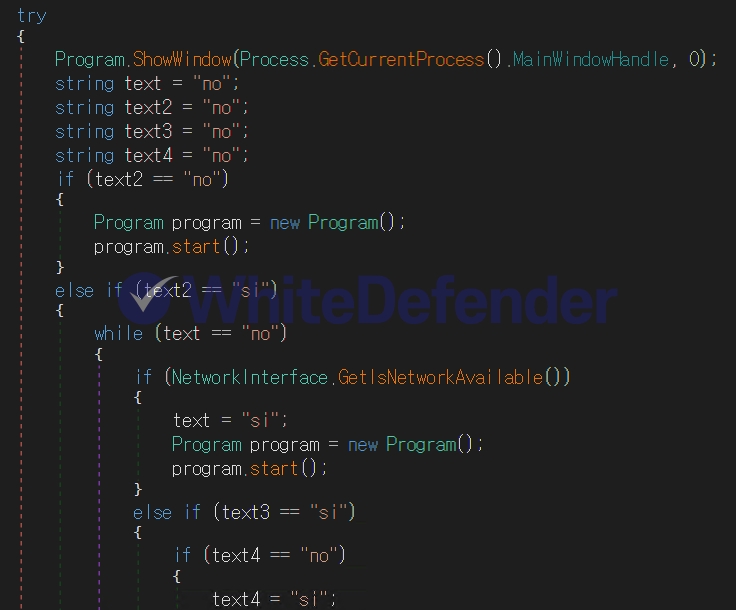
[Figure 4 Internal if branch instruction si (Spanish)]
Infection results
After encryption is complete, the guide file is created with the name README.txt, and each encrypted file is changed to < file name. extension. xdddd >.
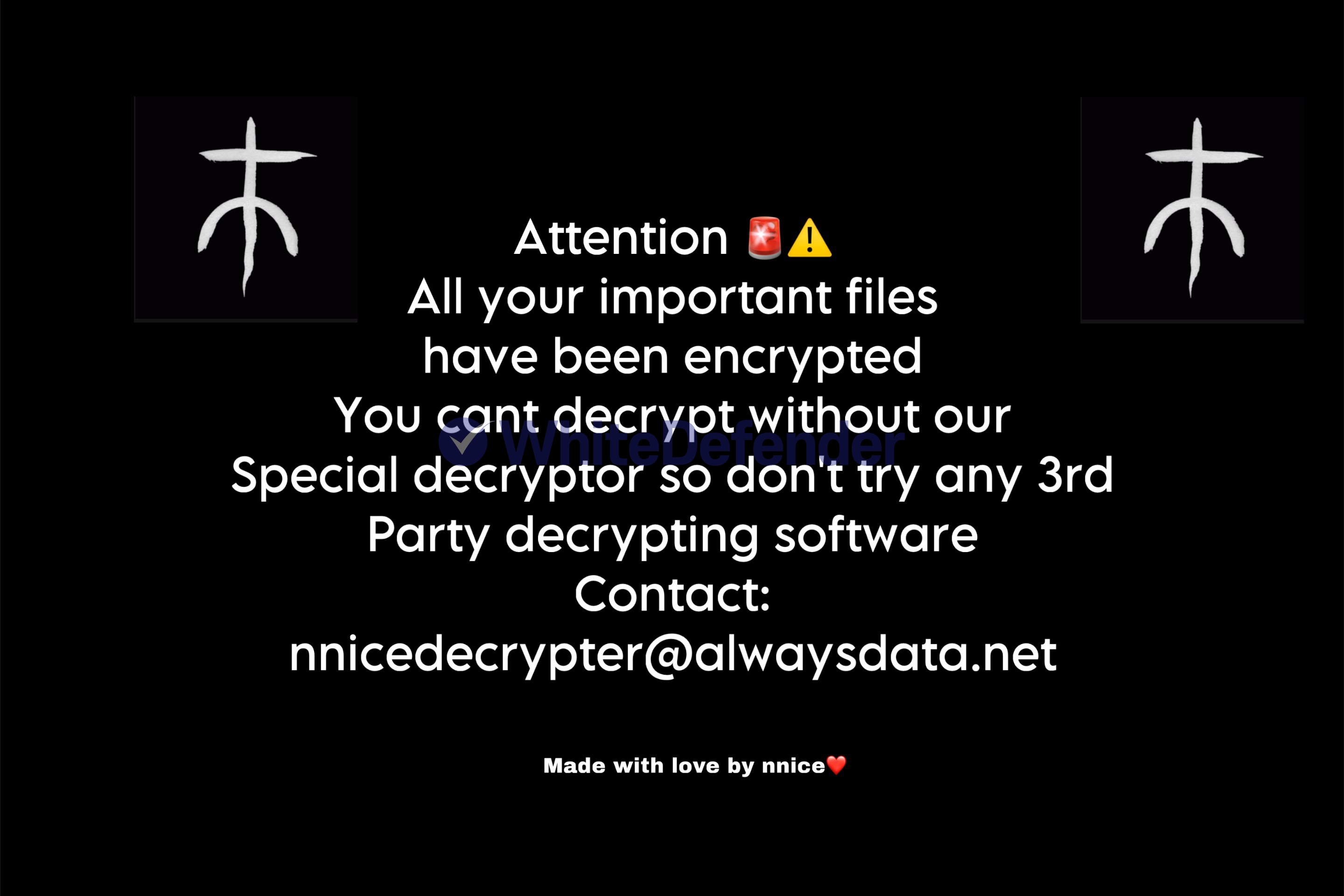
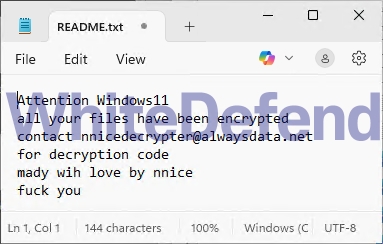
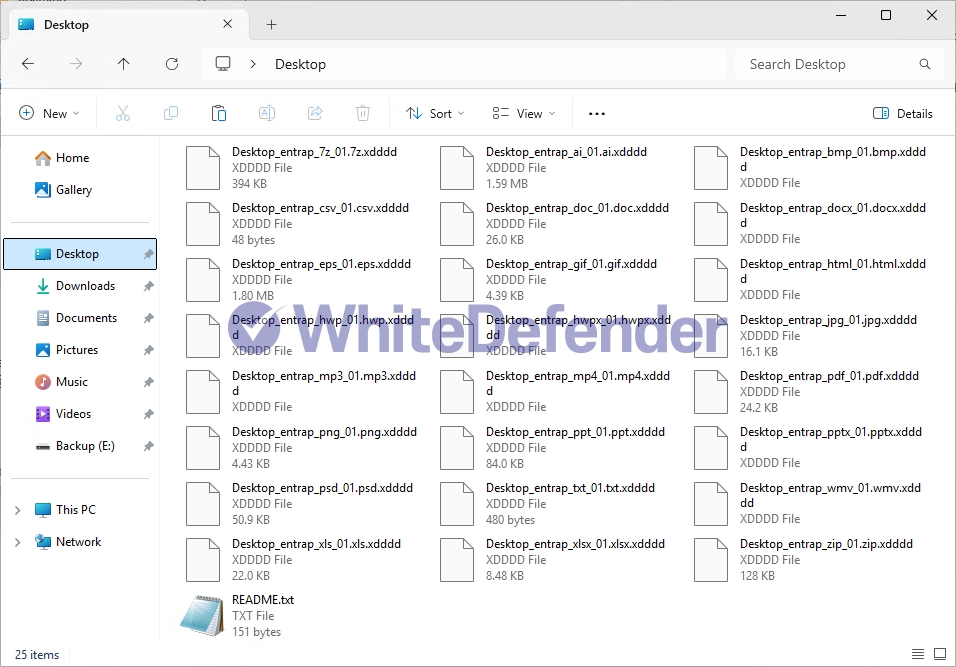
[Figure 5 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
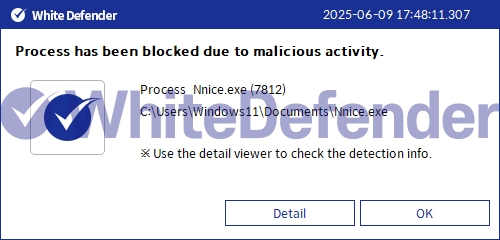
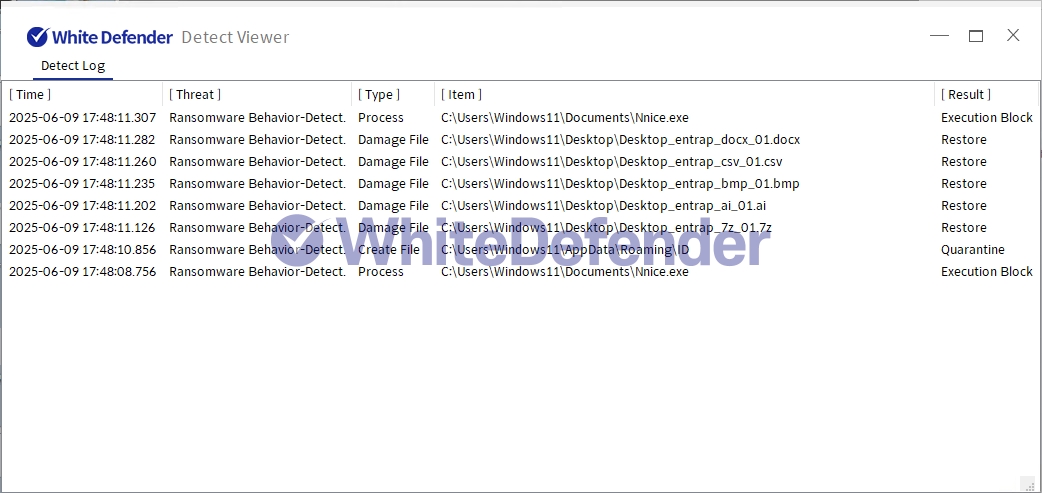
[Figure 6 Blocking Message]

- Previous post
- No previous posts
- next post
- Clone ransomware

