Ransomware Report
You can check the latest ransomware information.
- title
- Clone ransomware
- Registration date
- 2025-06-10
- views
- 124
[ Clone Ransomware ]
[Virus/malicious code activity reported: Clone ransomware]
A security breach suspected to be a Clone ransomware attack has occurred.
We would like to provide the following information and warning regarding the situation.
Clone ransomware
The ransomware is called Clone and it appears to be changing all files to filename.extension.id-personalKey8-digit.[CloneDrive@mailum.com].Clone.
How it works
File version
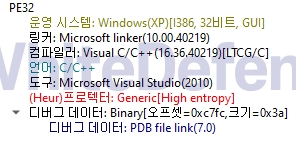
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
Clone ransomware is a C++-based ransomware that is a variant of Dharma ransomware. It has the function of preventing duplicate operations by registering a specific value in the registry when encryption is complete and multiple executions through a mutex when executed. The ransomware checks for specific services and processes related to data immediately after execution and stops and terminates the services. It deletes shadow copies to make it difficult to restore user data during encryption and executes a ransom note in exe format after encryption is complete. It registers the ransomware executable file and ransom note in the location of the startup program.
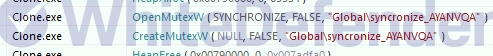
[Figure 3 Dynamic contents of mutex to prevent multiple executions]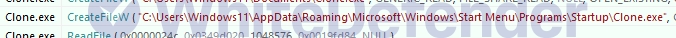
[Figure 4 Ransomware executable file registered in startup program]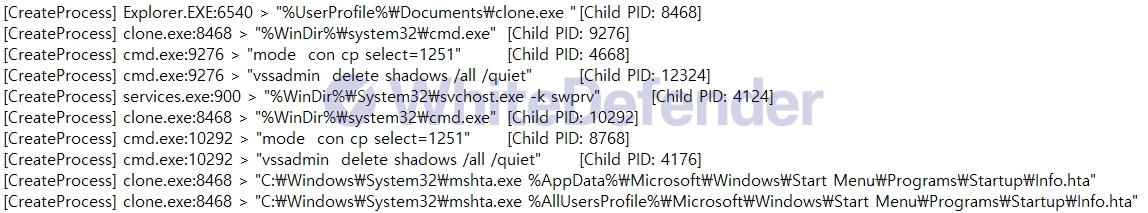
[Figure 5 Additional cmd commands collected with Pocmon]
Infection results
After encryption is complete, a guide file is created with the name clone_info.txt on each root drive and desktop and mshta.exe in the system32 folder. Each encrypted file is changed to < file name. extension. id-8-digit personal key. [CloneDrive@mailum.com]. Clone >.
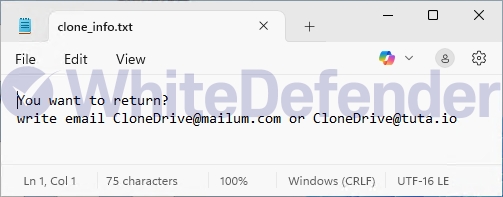
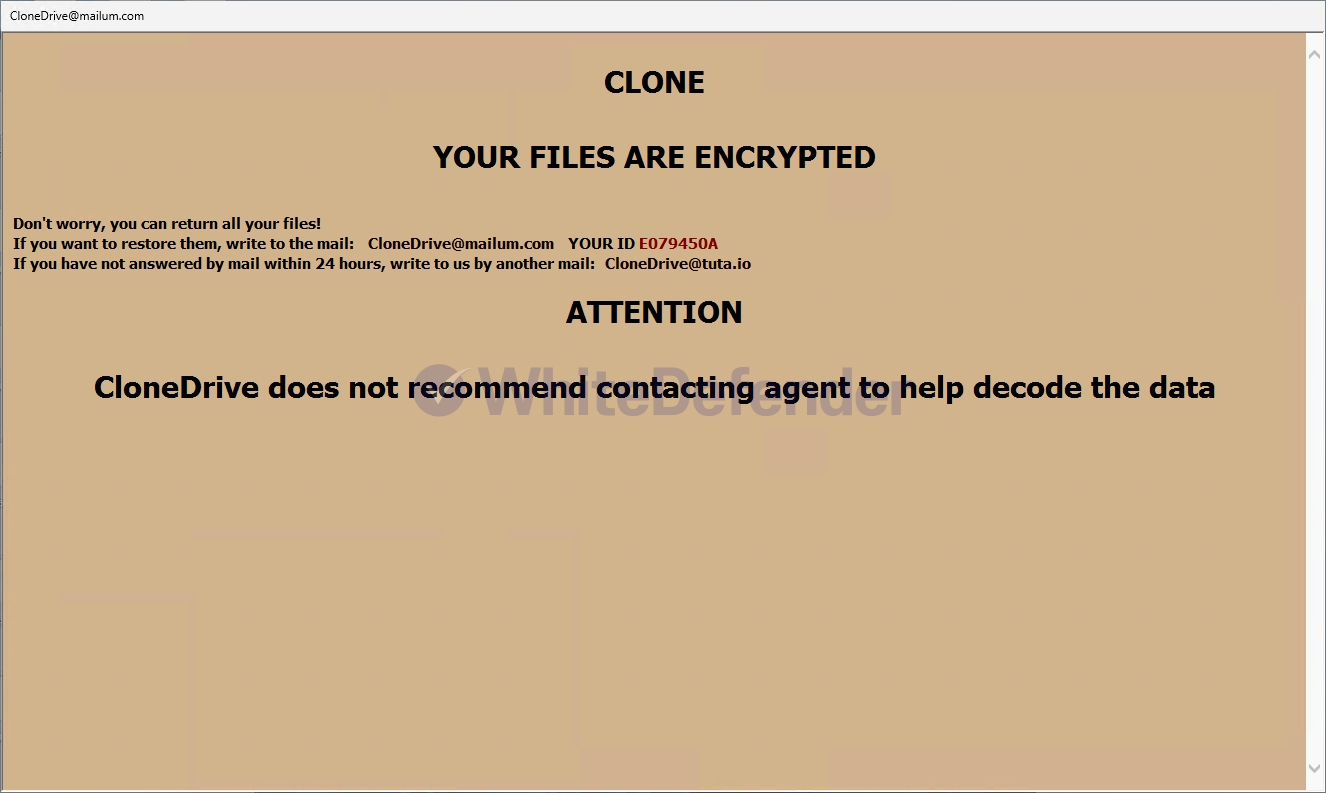
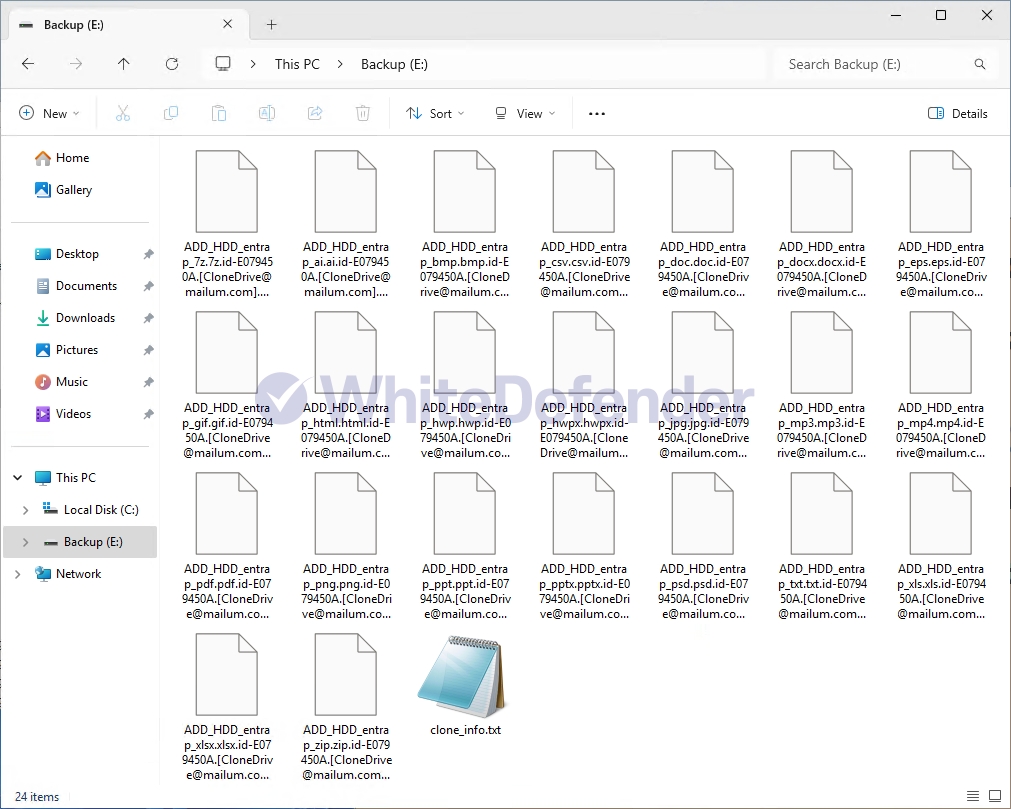
[Figure 6 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
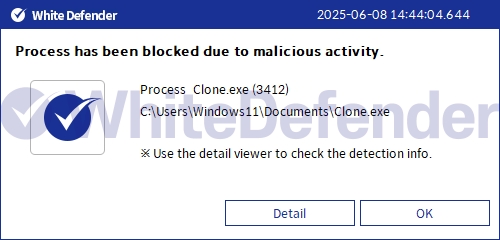
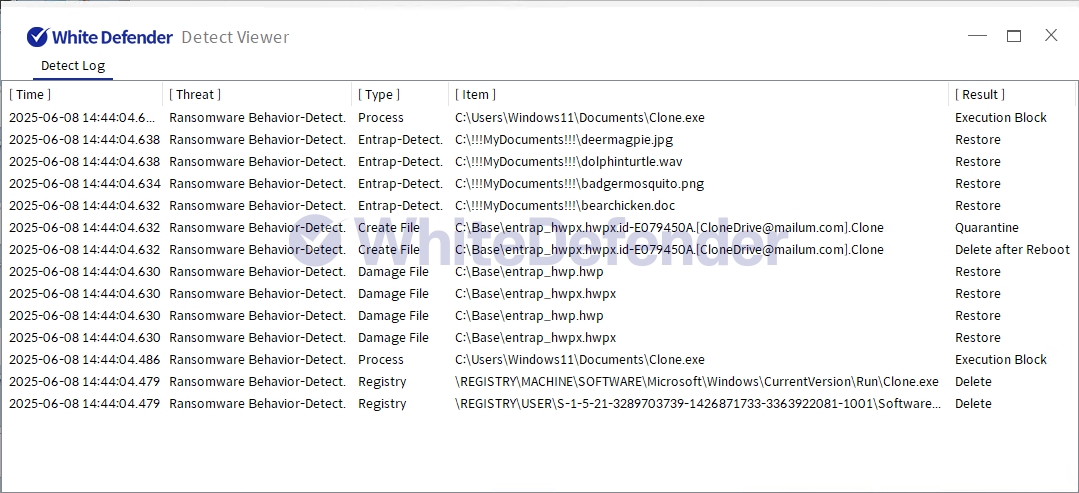
[Figure 7 Blocking Message]

- Previous post
- No previous posts
- next post
- Cs137 ransomware

