Ransomware Report
You can check the latest ransomware information.
- title
- Cs137 ransomware
- Registration date
- 2025-05-28
- views
- 30
[ Cs137 Ransomware ]
[Virus/malicious code activity report: Cs137 ransomware]
A security breach suspected to be in the form of Cs137 ransomware has occurred.
We would like to provide the following information and warning regarding the situation.
Cs137 ransomware
The ransomware in question is called Cs137, and although the filename and extension are the same, it appears to be encrypting all targets.
How it works
File version
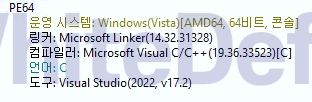
[Figure 1 Ransomware executable file compiler information]
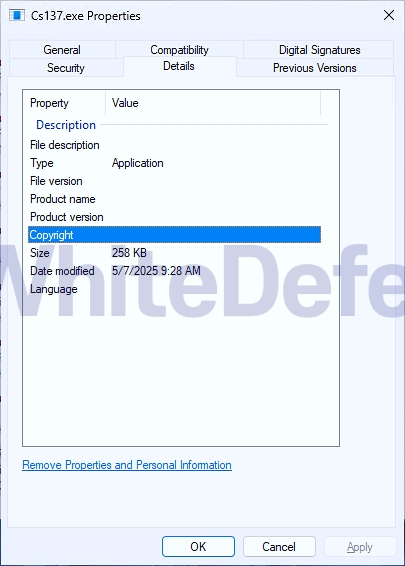
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
CS137 is a ransomware developed in C++, and based on the analysis results so far, it is classified as a threat with atypical characteristics that does not involve actual ransom demands. Its main purpose appears to be testing or delivering warning messages to security research institutes and sandbox analysis environments, rather than data encryption.
Key Features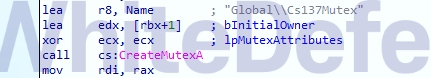
[Figure 3 Global mutex static code to prevent duplicate execution]
Before encryption, the following system recovery-related functions are disabled to prevent the victim from attempting to recover:
• Development language and structure:: CS137 is written in native C++ and creates its own mutex inside the executable file to prevent duplicate execution. This avoids crashes due to duplicate infections in the system and maintains a single-instance environment.
• Encryption function and limited damage:: Unlike typical ransomware, CS137 does not cause any significant system destruction other than encrypting files and changing the desktop image.
In particular, it does not request decryption fees or payment instructions from the user, and the notification file simply contains a message at the level of "an attack has been conducted."
• Possibility of security testing purposes or demonstrations: Samples are continuously being collected from sandboxes and cloud-based detection environments of various security companies, and it appears that "new ransomware release testing" or "warning messages to the security industry" are inserted into the samples.
➤ However, this is an assumption about the attacker's intention, and the exact source or attacker lineage information has not been confirmed at this time.
Infection results
After encryption is complete, a guide file is created in each folder with the name .README.txt with a random 6-digit number. Each encrypted file is encrypted without changing its name.
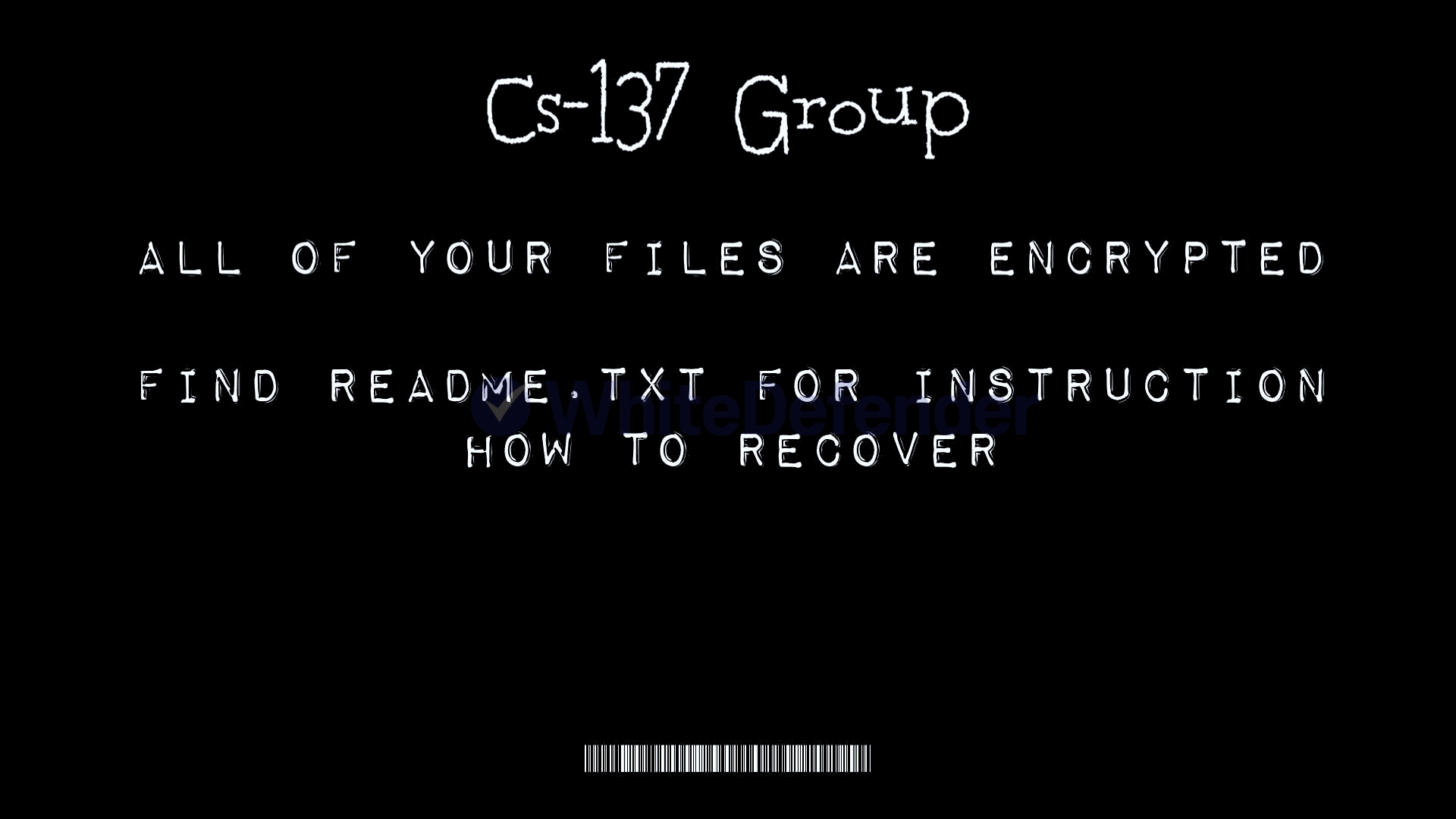
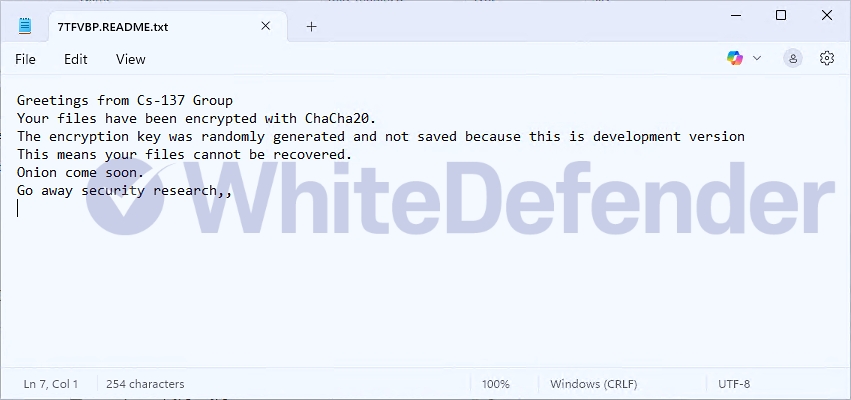
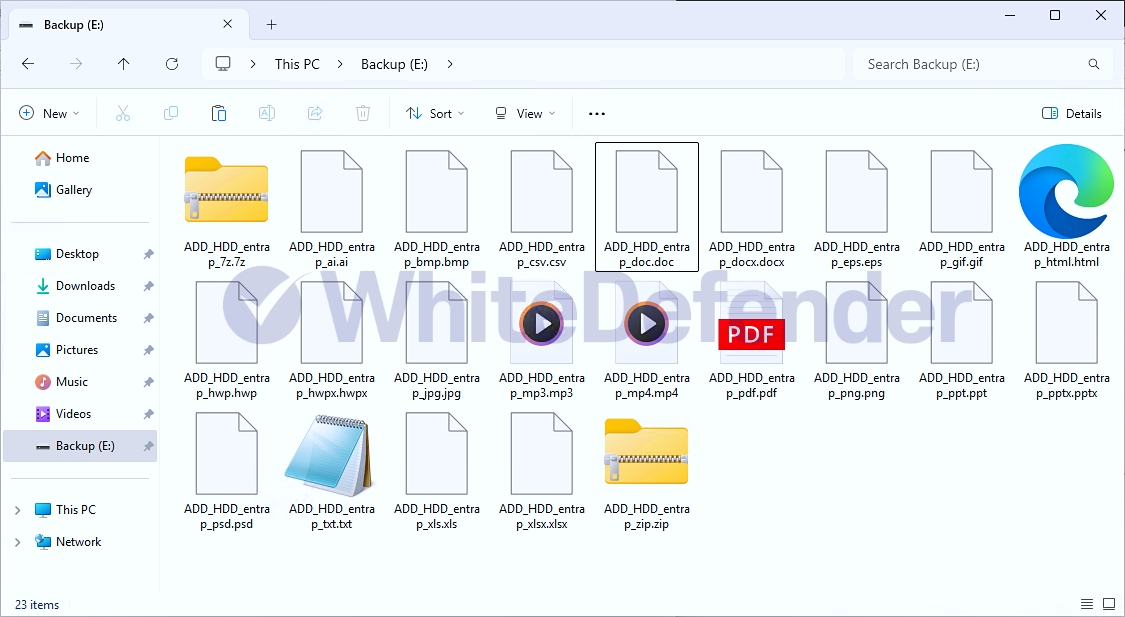
[Figure 4 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
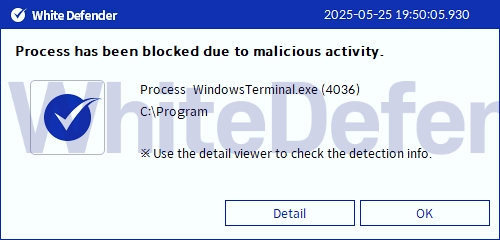
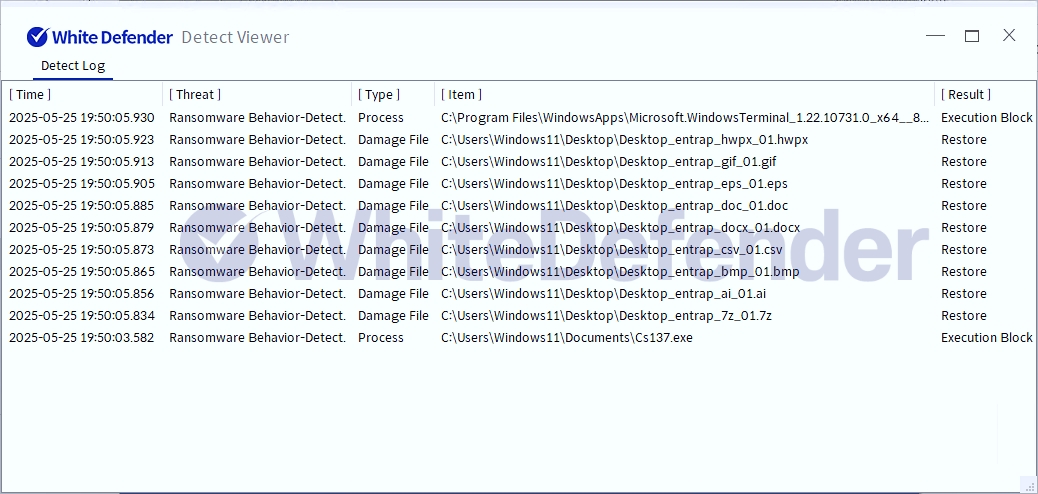
[Figure 5 Blocking Message]
Go watch the Cs137 blocking video

- Previous post
- No previous posts
- next post
- JackSparrow ransomware

