Ransomware Report
You can check the latest ransomware information.
- title
- JackSparrow ransomware
- Registration date
- 2025-05-21
- views
- 2209
[ JackSparrow Ransomware ]
[ Virus/malicious code activity reported: JackSparrow ransomware ]
We are aware of a security breach that is believed to be JackSparrow ransomware.
We would like to provide the following information and warning regarding the situation.
JackSparrow ransomware
The ransomware is called JackSparrow and it appears to be changing all files to the .encrypted. extension.
How it works
File version
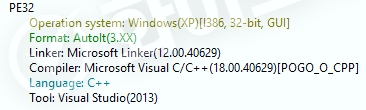
[Figure 1 Ransomware executable file compiler information]
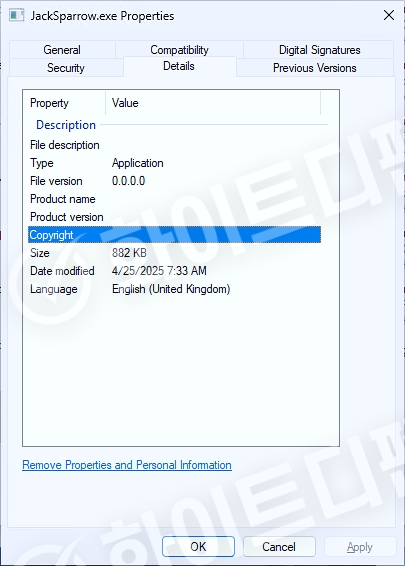
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
JackSparrow ransomware is written in C++ and uses the following automatic properties when executed.
First, it copies its executable file to a specific path within the system (e.g. %APPDATA% or %TEMP%) and then sets it to automatically run when the system logs in by utilizing the Windows Task Scheduler or the Run registry key (e.g. HKCUSoftwareMicrosoftWindowsCurrentVersionRun). This allows it
to remain active even after a reboot.
Disabling System Restore Functions
Before encryption, the following System Restore-related functions are disabled to prevent victims from attempting recovery:
• Delete Volume Shadow Copies: All past snapshots of the local disk are removed using the vssadmin delete shadows /all /quiet command, preventing general users from attempting recovery using the Windows Restore function.
• Disable System Restore and block error reporting: Block Windows’ automatic recovery procedure and error reporting messages using commands such as bcdedit /set {default} recoveryenabled No and bcdedit /set {default} bootstatuspolicy ignoreallfailures. This is done to prevent the system from recognizing the infection or from running the recovery process on its own.
• Delete or block access to Windows Restore Points: Some variants change registry keys related to Restore Points or disable related services (srservice, winmgmt), completely disabling the Restore function.
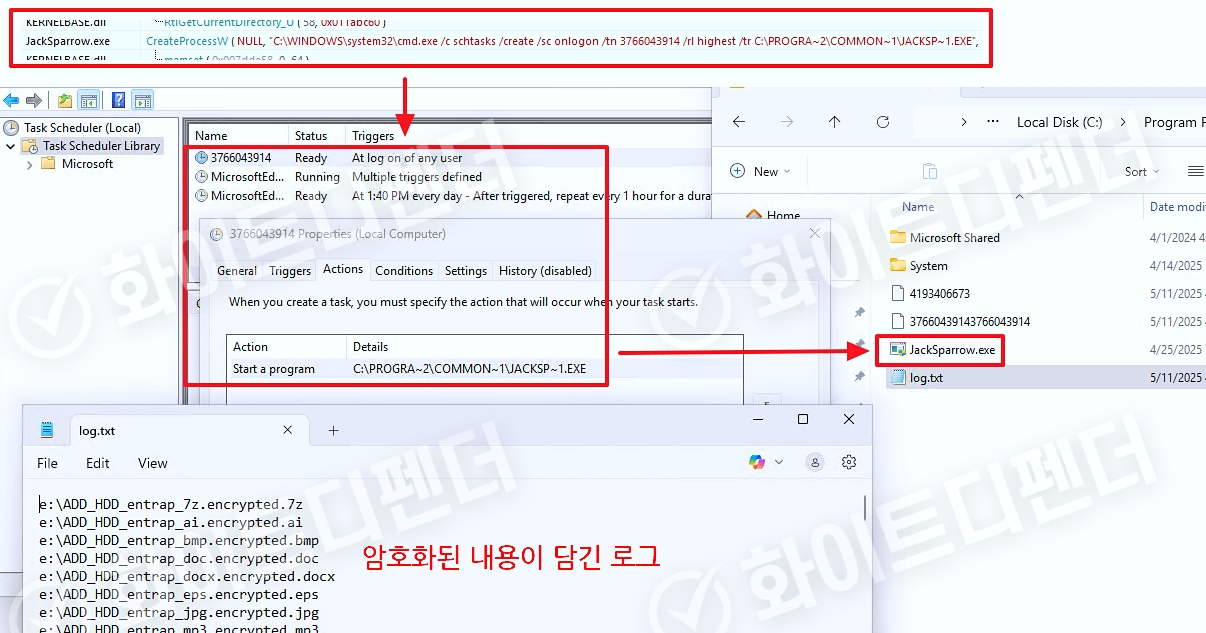
[Figure 3 Create a copy of the executable file and create a schedule to automatically run it when logging in]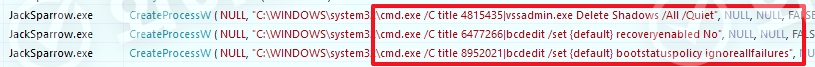
[Figure 4 Deleting shadow copies and restoring the left window and disabling the message function when an error occurs]
Infection results
The guide file is displayed by the ransomware itself after encryption is complete, and each encrypted file is changed to < file name.encrypted.extension >
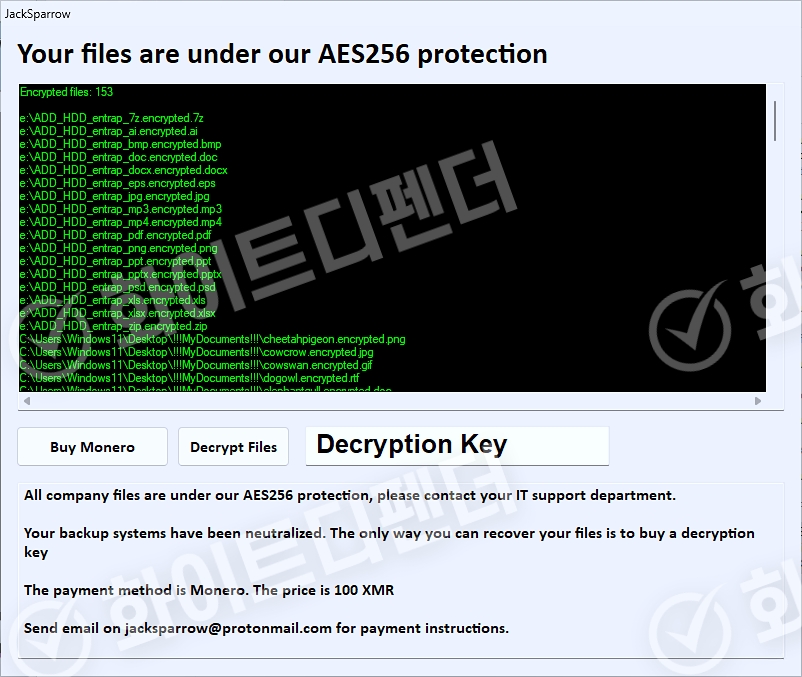
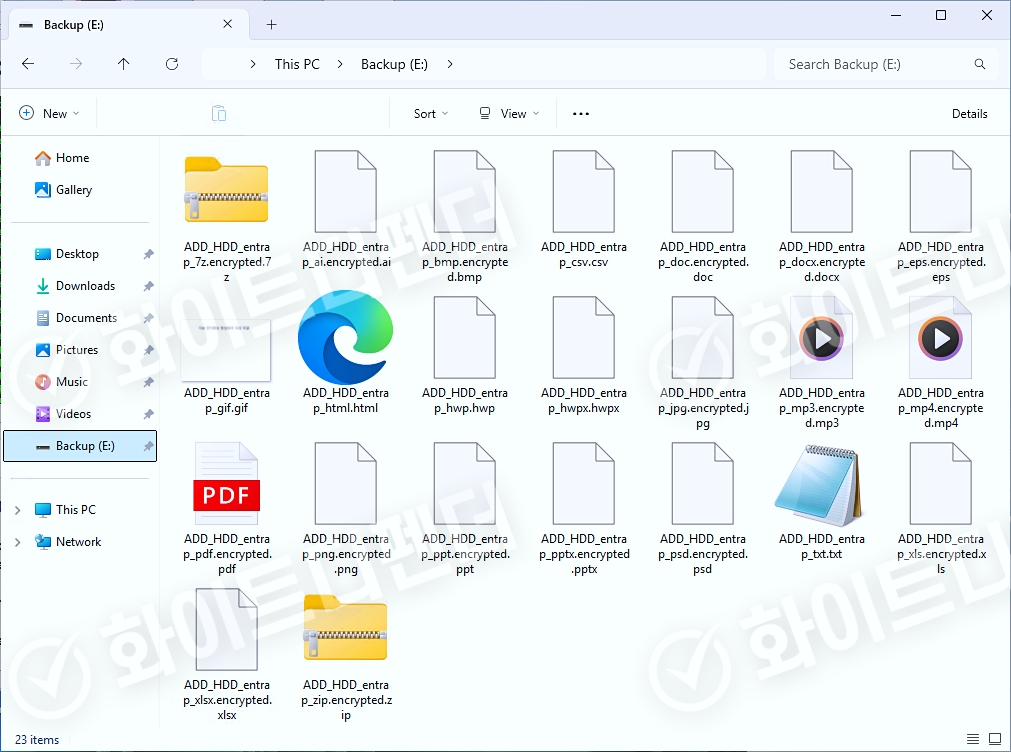
[Figure 5 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
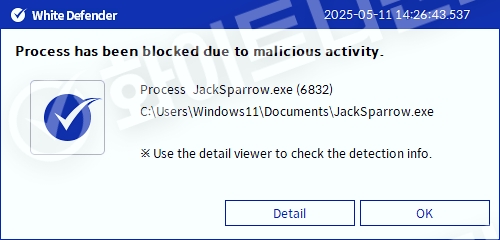
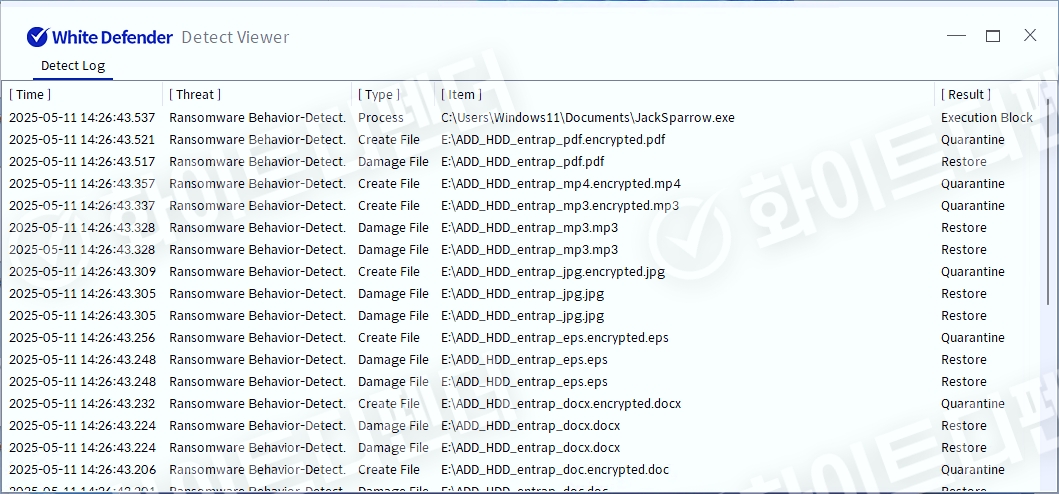
[Figure 6 Blocking Message]
Go watch the JackSparrow blocking video

- Previous post
- Cs137 ransomware
- next post
- Rdp ransomware

