Ransomware Report
You can check the latest ransomware information.
- title
- Rdp ransomware
- Registration date
- 2025-05-19
- views
- 154
[ Rdp Ransomware ]
[Virus/malicious code activity report: Rdp ransomware]
A security breach suspected to be RDP ransomware has occurred.
We would like to provide the following information and warning regarding the situation.
Rdp ransomware
The ransomware is called Rdp and it appears to be changing all files with the filename extension .rdplocked.
How it works
File version
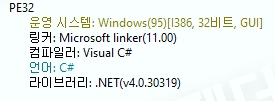
[Figure 1 Ransomware executable file compiler information]
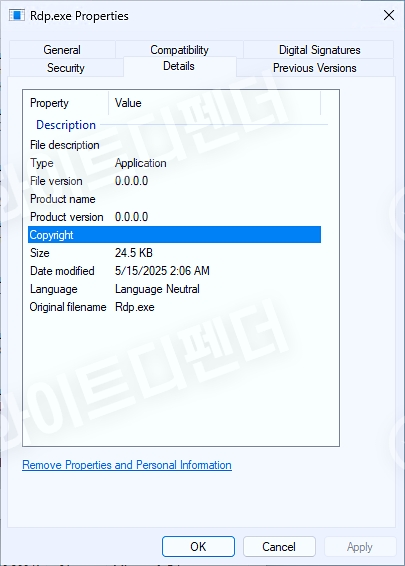
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This ransomware was developed based on C#.NET, and to prevent duplicate encryption, it checks for previous infections by checking specific key values in the registry before execution. Before performing encryption, it forcibly terminates security solutions and major data-related processes to maximize damage, and then proceeds with file encryption within the system. In addition, it includes a function to intercept cryptocurrency payment addresses through the clipboard hijacking function. When the victim copies the wallet address to pay or send cryptocurrency, the contents of the clipboard are automatically replaced with the attacker's wallet address, which can cause financial loss.
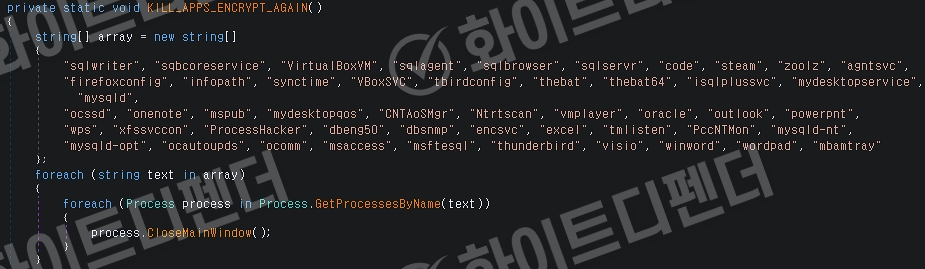
[Figure 3 Internal code of process name being forcibly terminated]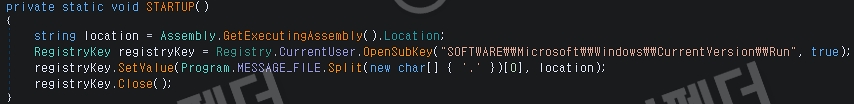
[Figure 4 Registering RAMSunware in the startup program registry]
Infection results
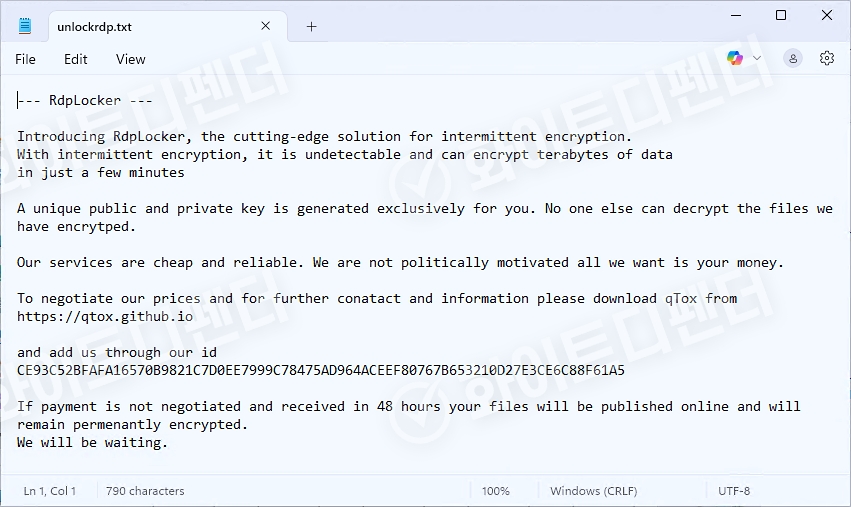
After encryption is complete, the guide file is created in each folder with the name unlockrdp.txt, and each encrypted file is changed to < file name. extension. rdplocked >.
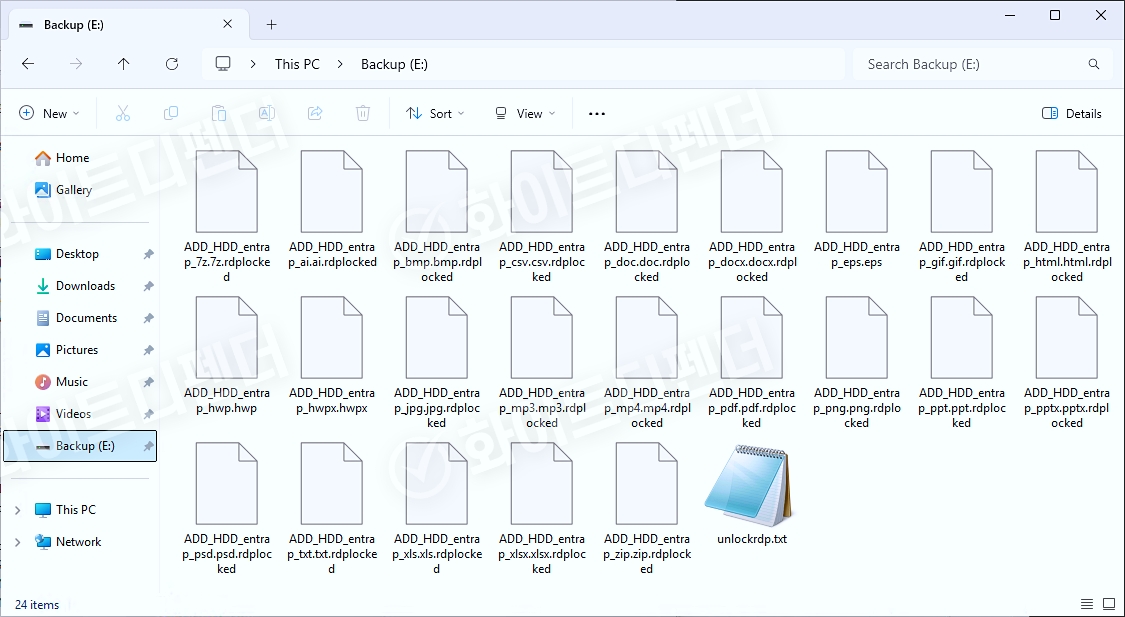
[Figure 5 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
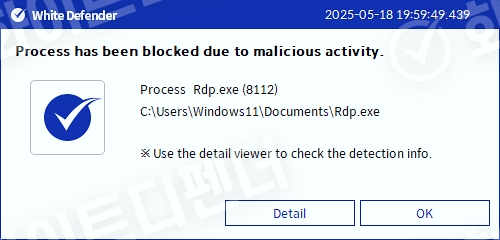
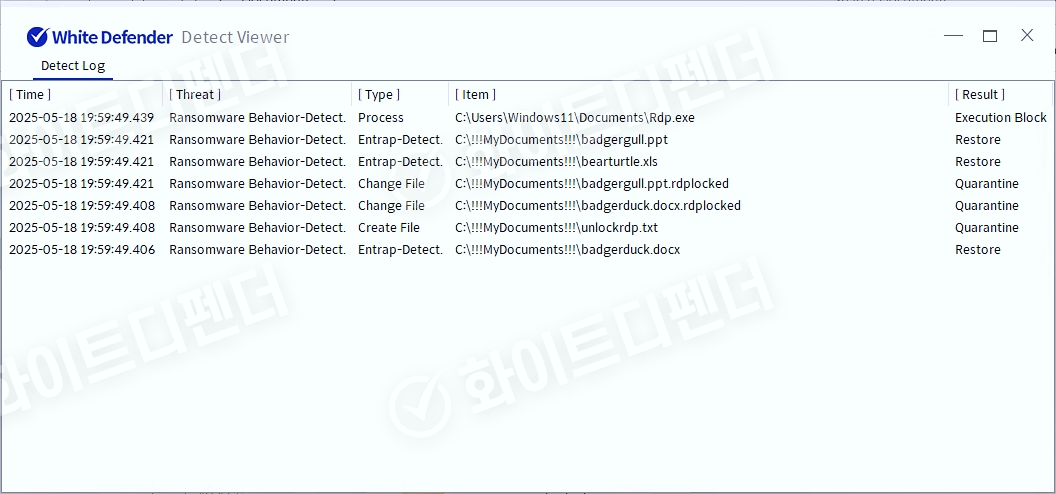
[Figure 6 Blocking Message]
Go watch the RDP blocking video

- Previous post
- JackSparrow ransomware
- next post
- Maga ransomware

