Ransomware Report
You can check the latest ransomware information.
- title
- Encp ransomware
- Registration date
- 2025-01-20
- views
- 668
[ Encp Ransomware ]
[Virus/malicious code activity reported: Encp ransomware]
We are aware of a security breach that is believed to be in the form of Encp ransomware
. We would like to provide the following information and warning regarding the situation.
Encp ransomware
The ransomware in question is called Encp and it appears to be changing the filename.extension.encp of all files.
How it works
File version
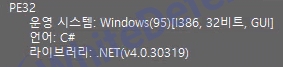
[Figure 1 Ransomware executable file compiler information]
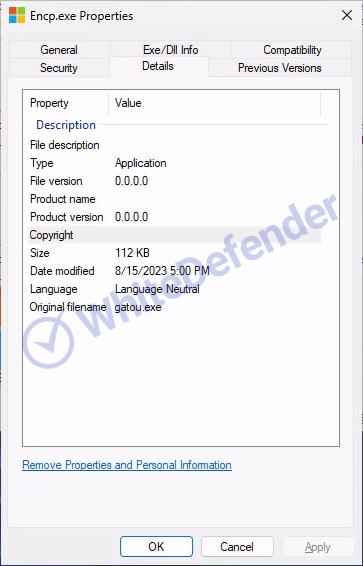
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
The ransomware appears to be a .NET-based chaos series, and after initial execution, it copies itself to save the executable file in the %AppData%Roaming path, and re-executes it by disguising the file name as svchost.exe. This disguises it as a system file so that the user does not become suspicious. It is designed to prevent duplication of execution and encryption tasks, and maintains persistence by manipulating the registry to register itself as a startup program so that it automatically runs even after a reboot if the attack fails. This is a strategy to increase the success rate of the attack and hinder the victim's recovery attempts.
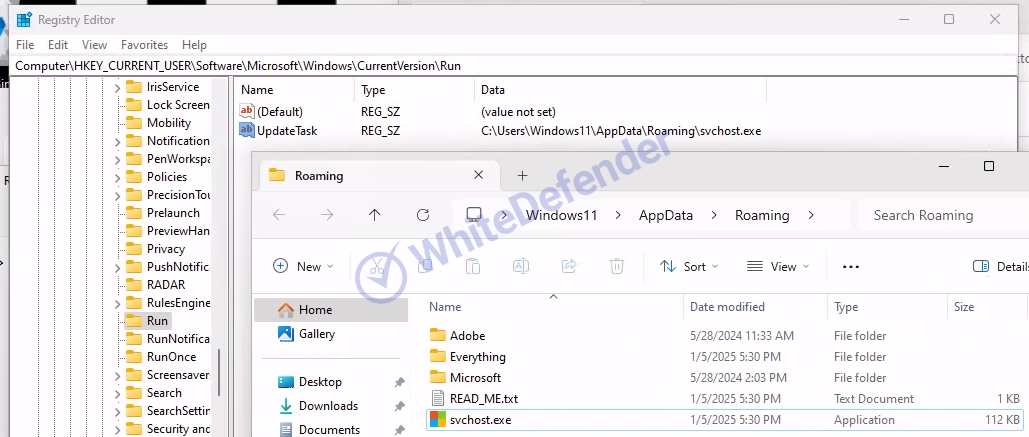
[Figure 3 Rename to svchost and register startup program]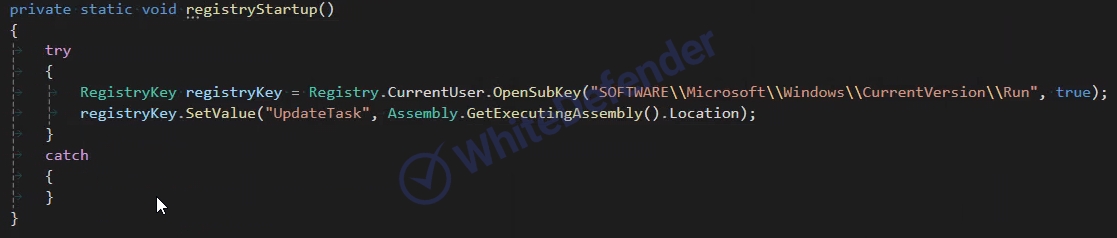
[Figure 4 Internal code for creating a registry entry]It is designed not to run on operating systems set to Azerbaijani (Latin) and Turkish. It deletes shadow copies and backup catalogs, and disables Windows recovery features, making recovery difficult. These actions virtually eliminate the possibility of recovering user data.
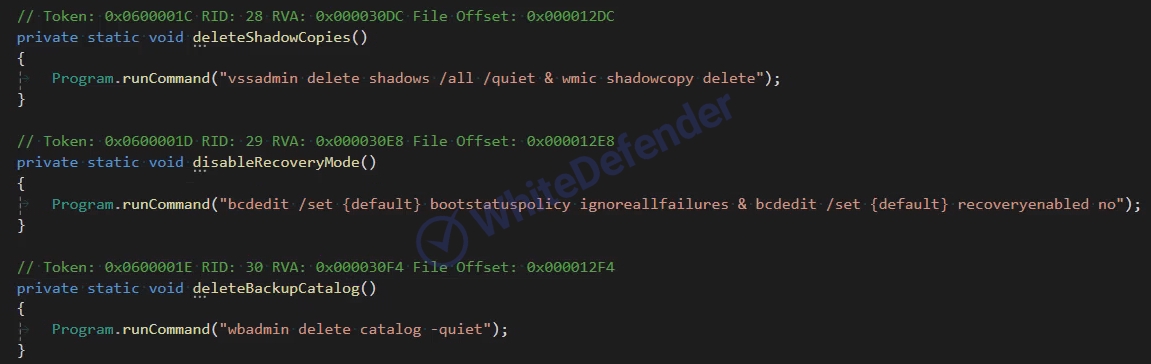
[Figure 5 Multi-mode support through situation-dependent parameters]
Infection results
A guide file is created in each folder location with the name <READ_ME.txt>, and each encrypted file is changed to <file name.extension.encp>. After encryption is complete, run the txt note.
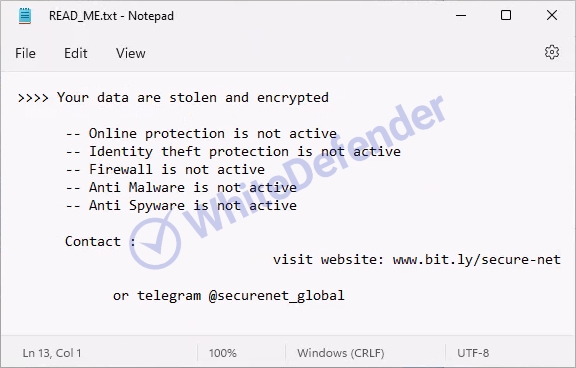
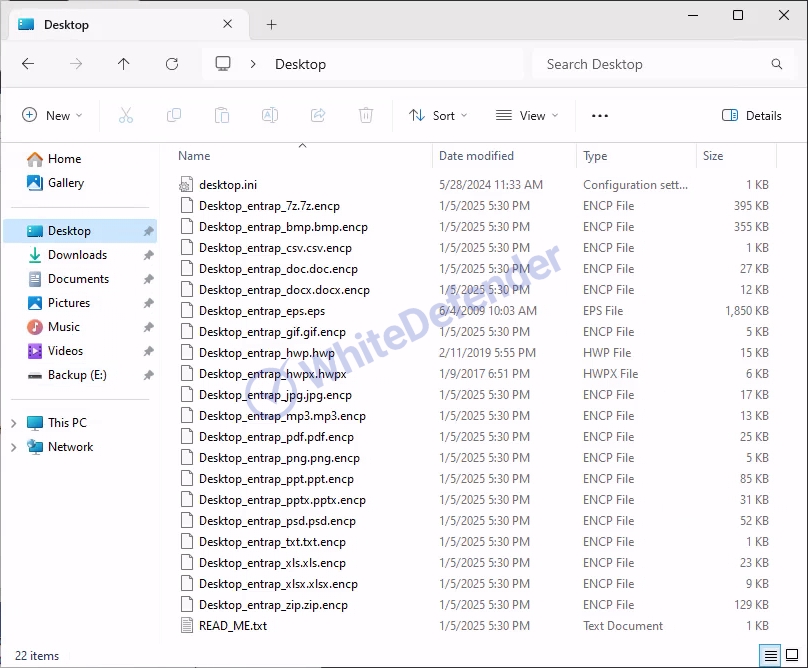
[Figure 6 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
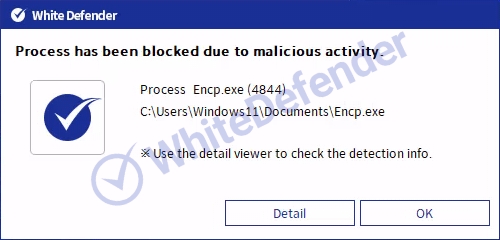
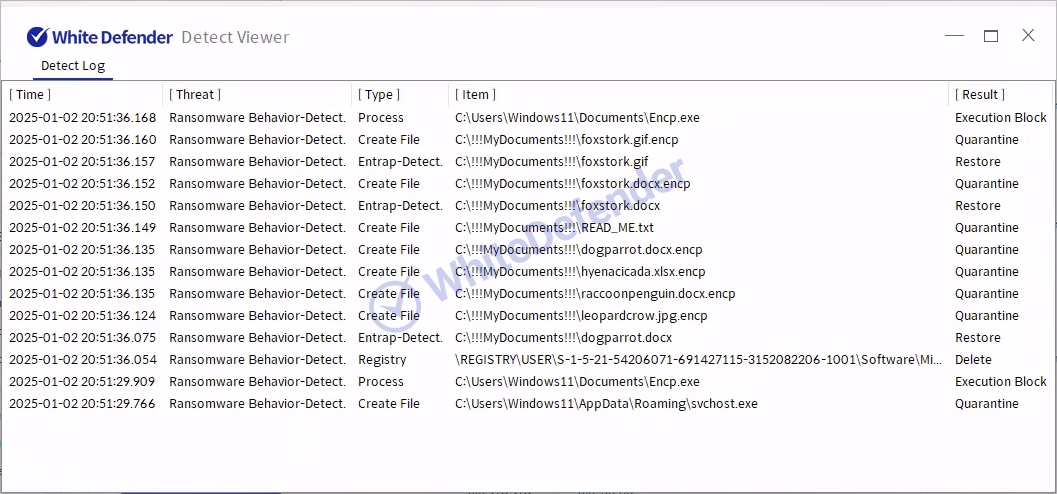
[Figure 7 Blocking Message]

- Previous post
- Maga ransomware
- next post
- Kasper(Biobio) ransomware

