Ransomware Report
You can check the latest ransomware information.
- title
- Phalcon ransomware
- Registration date
- 2024-11-27
- views
- 11003
[ Phalcon Ransomware ]
[ Virus/malicious code activity reported: Phalcon ransomware ]
We are aware of a security breach that is believed to be in the form of Phalcon ransomware
. We would like to provide the following information and warnings regarding the situation.
Phalcon ransomware
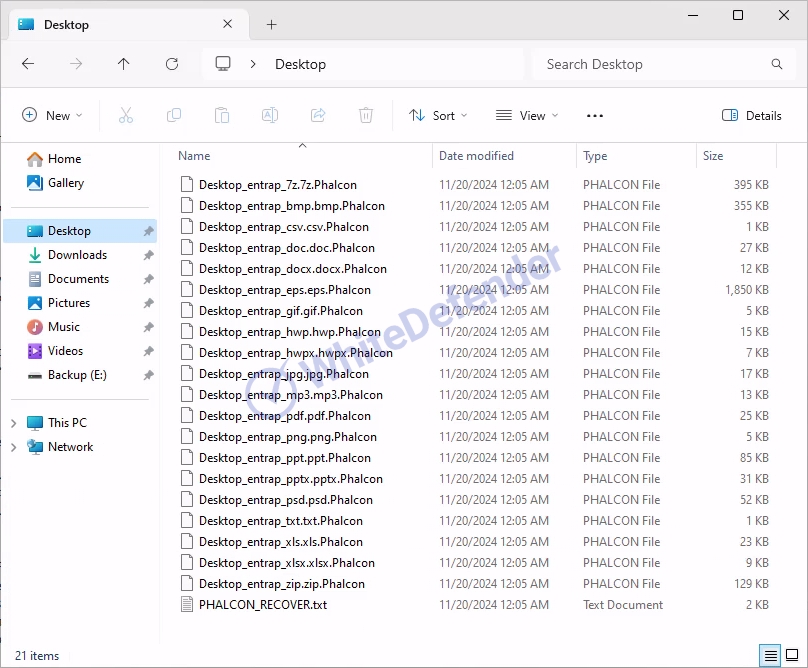
The ransomware is called Phalcon and it appears to be changing the filename.extension.Phalcon of all files.
How it works
File version
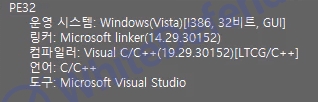
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
Ransomware written in C++ that supports multiple modes depending on the situation through additional parameters. It prevents duplication using mutexes and allows re-execution if encryption is terminated before it is completed through Windows schedule registration. It also supports deletion of ransomware executable files and shadow copies when encryption is completed.
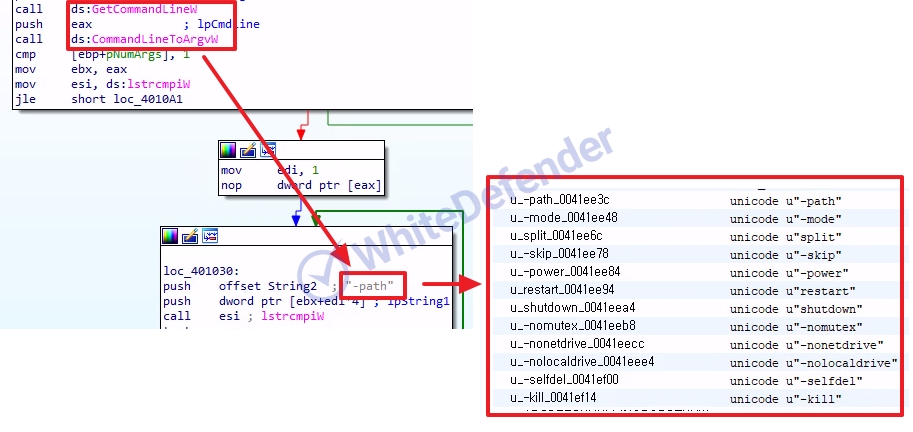
[Figure 3 Source code for receiving commands and internally confirmed command strings]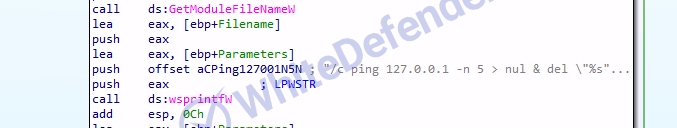
[Internal code to delete itself after completion of Figure 4]
Infection results
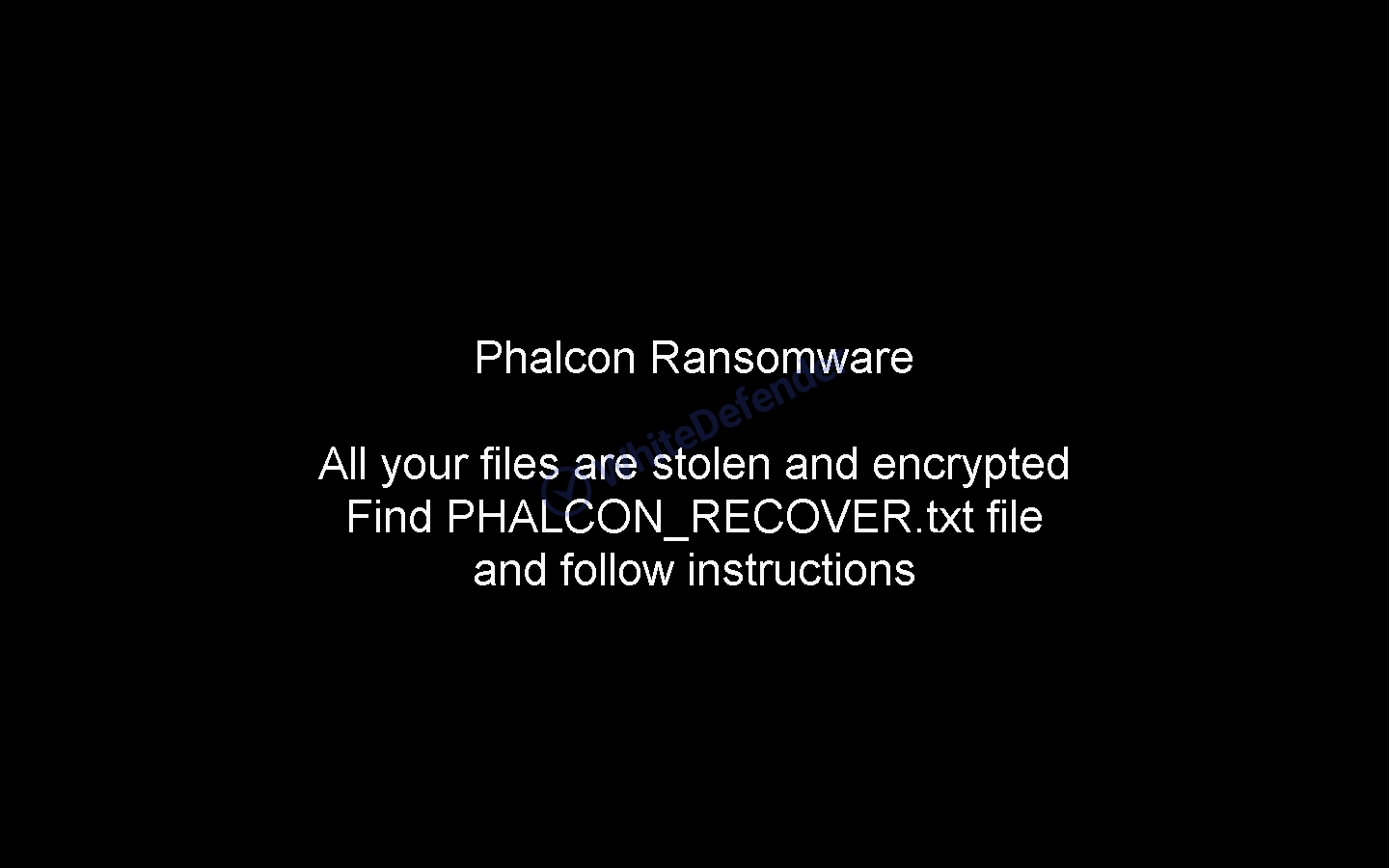
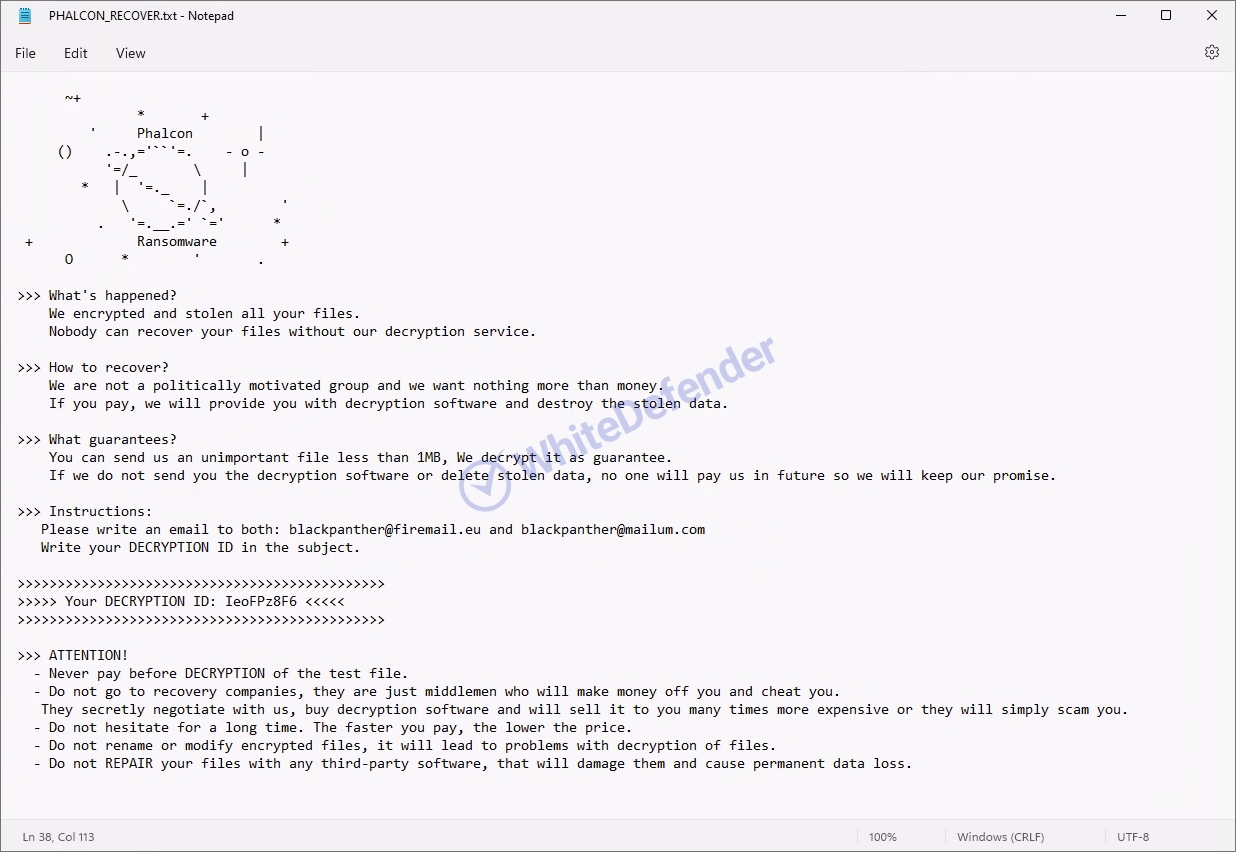
A guide file is created in each folder location with the name < PHALCON_RECOVER.txt >, and each encrypted file is changed to < file name. extension. Phalcon >. After encryption is complete, run the txt note.
[Figure 5 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
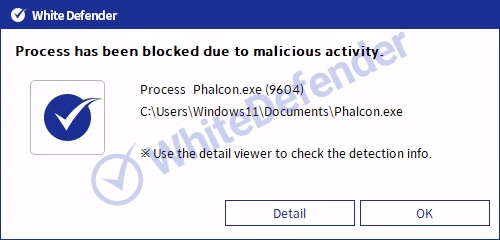
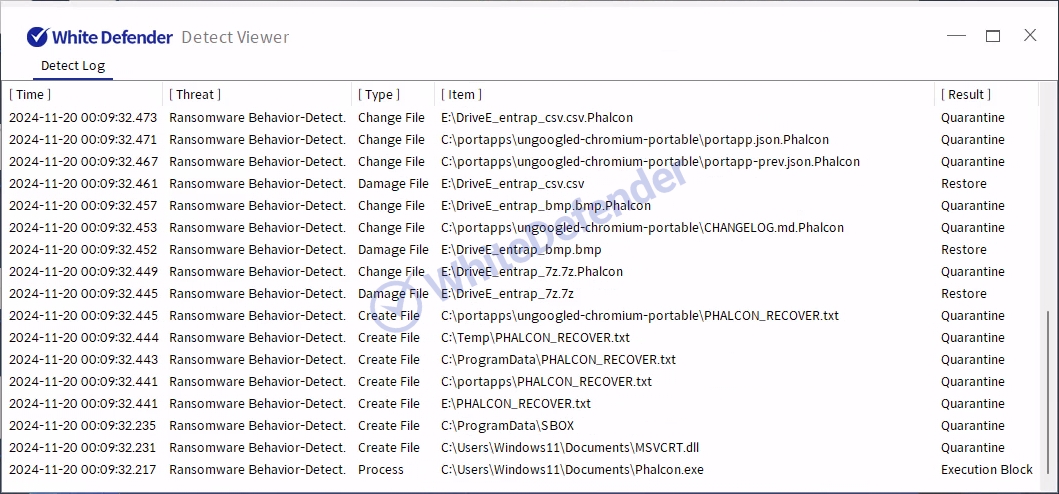
[Figure 5 Blocking Message]
Go watch the Phalcon blocking video

- Previous post
- TX Ransomware
- next post
- Allarich ransomware

