Ransomware Report
You can check the latest ransomware information.
- title
- Stop key processes/force termination of processes Shinki is LIKEAHORSE ransomware
- Registration date
- 2022-08-16
- views
- 38381
[ LIKEAHORSE ransomware ]
[Virus/malware activity reported: LIKEAHORSE ransomware]
A security breach believed to be in the form of LIKEAHORSE ransomware has occurred,
so we would like to confirm the situation and provide a warning as follows.
How it works
file version
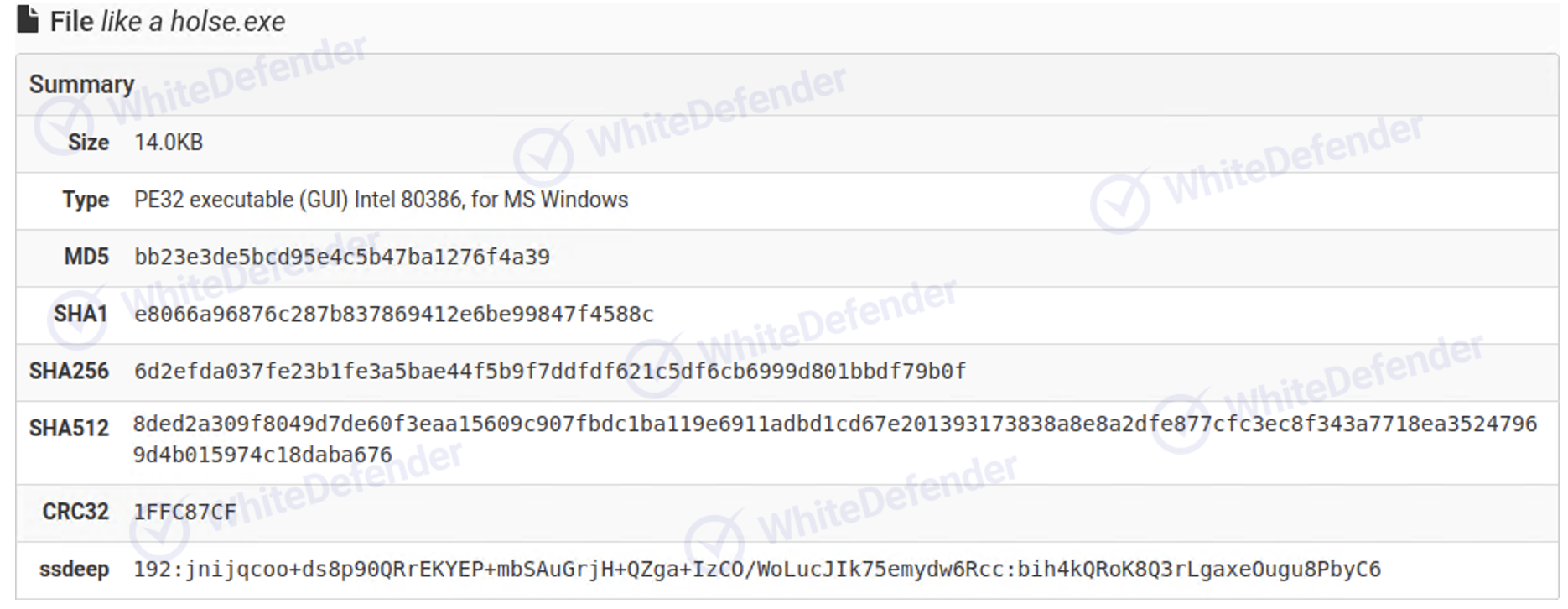
[Image 0 file version]
behavioral process
Deleting shadow copies
Delete shadow copies to make recovery of encrypted data difficult.

[Figure 1 Deleting shadow copies]Disable Windows recovery function
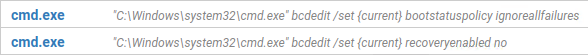
[Figure 2 Disable Windows recovery function]Disable Windows Firewall

[Figure 3 Disabling Windows Firewall]work goal
It works by targeting all available drives that are connected using GetLogicalDrives.
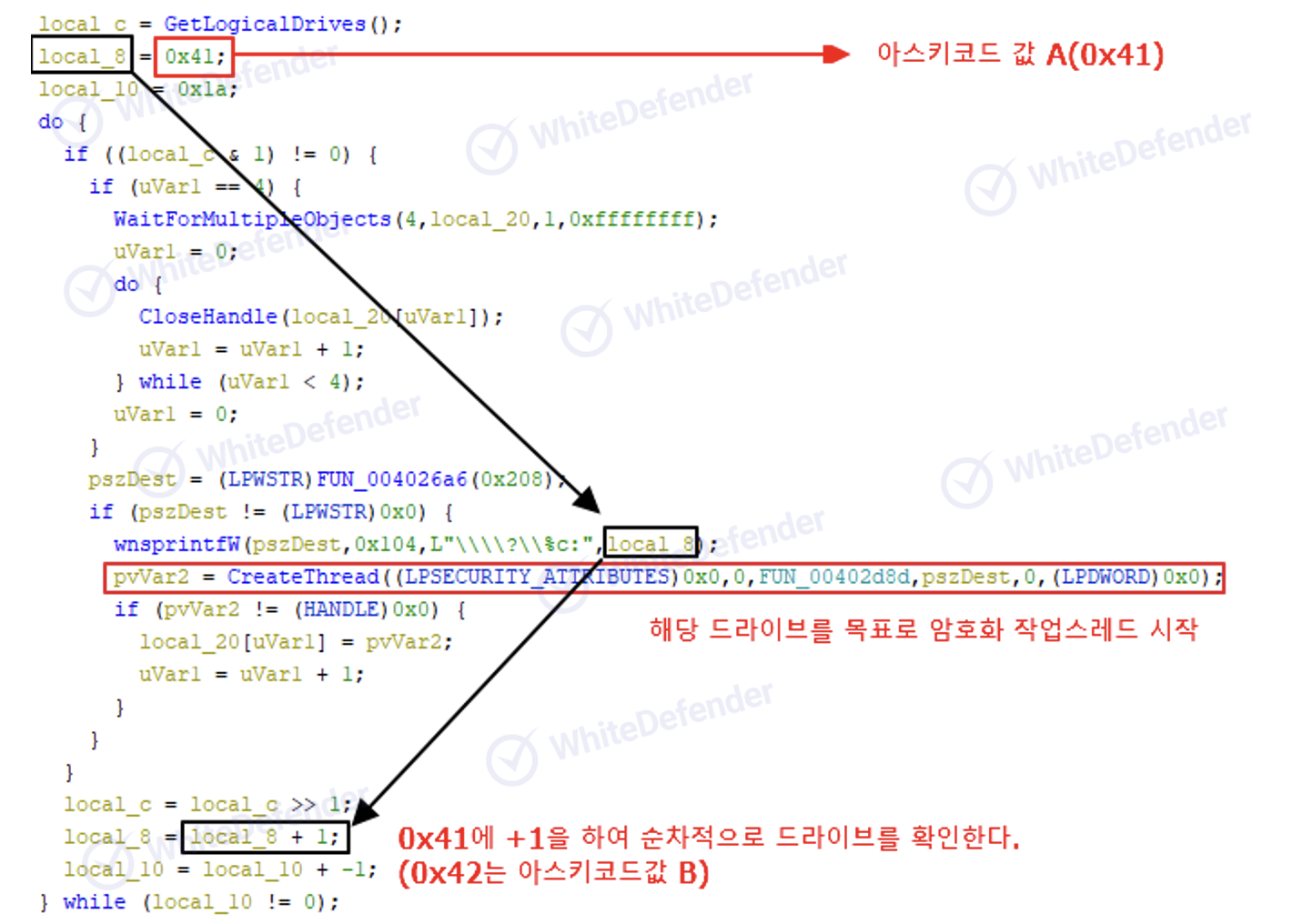
[Figure 4 Ransomware internal code]
Infection results
The information file is created in each folder with the name #RECOVERY#.txt, and when encryption is performed, the files are changed to <encrypted file name.LIKEAHORSE>.
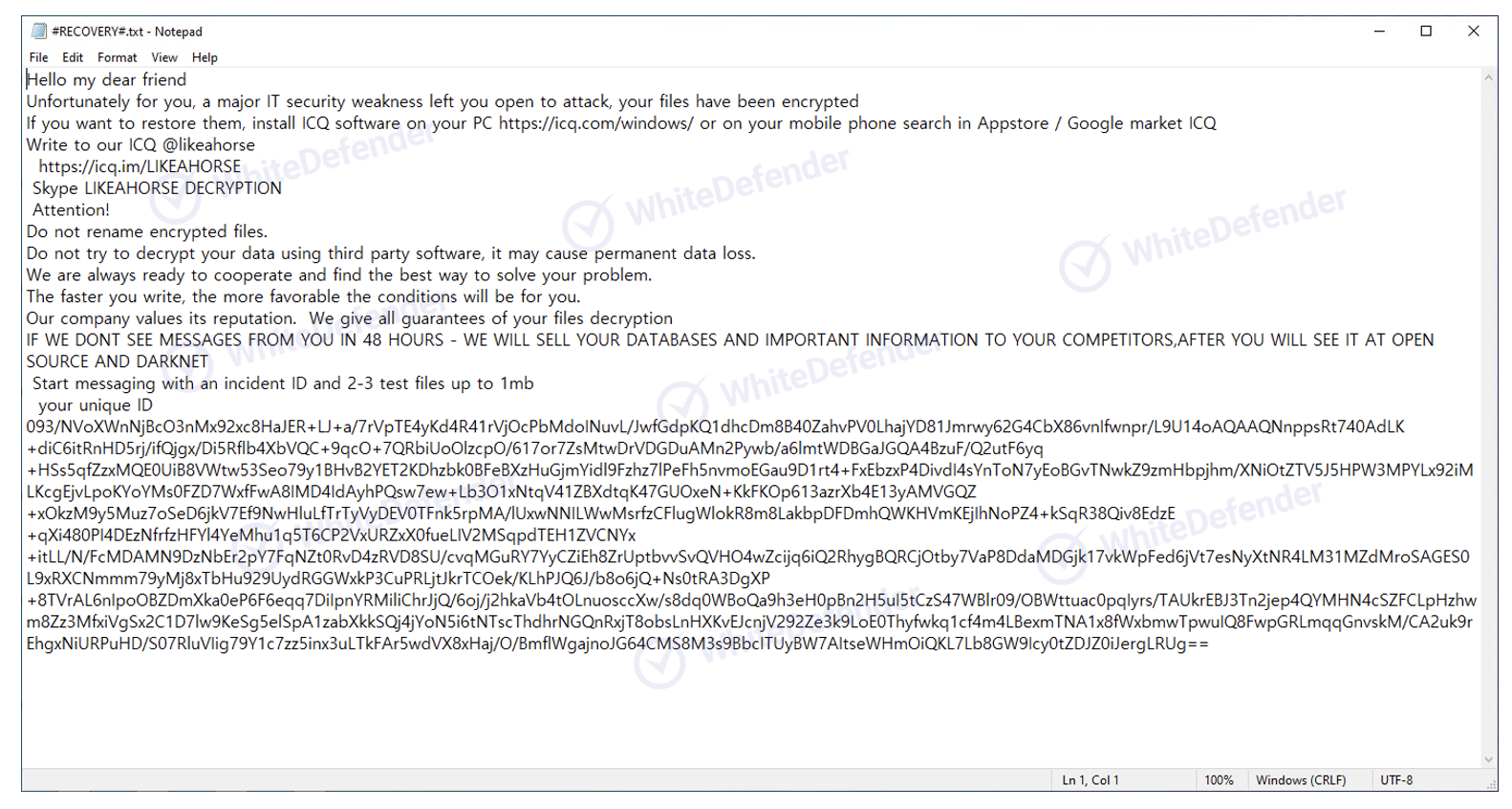
[Figure 5 Ransom note]
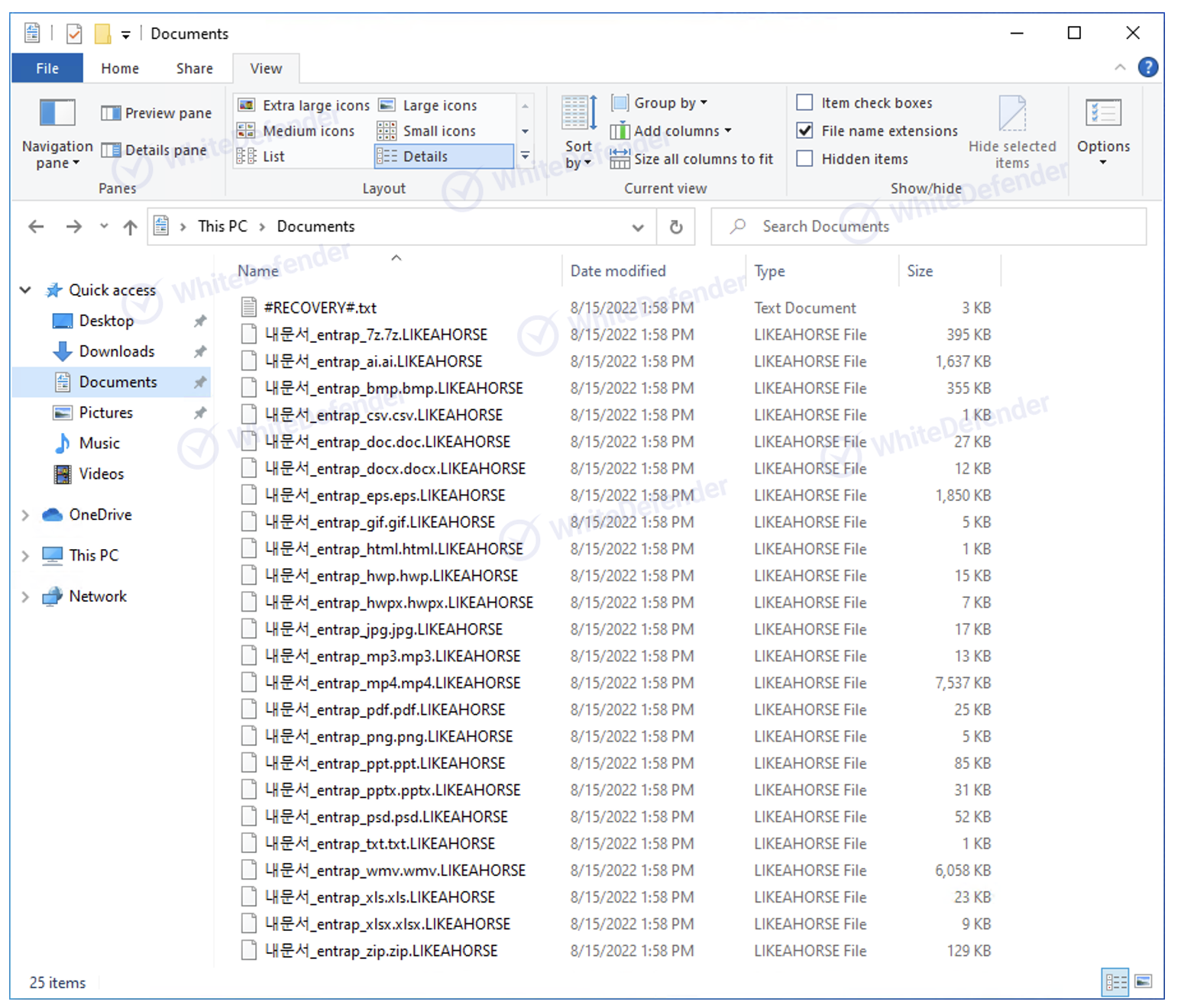
[Figure 6 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
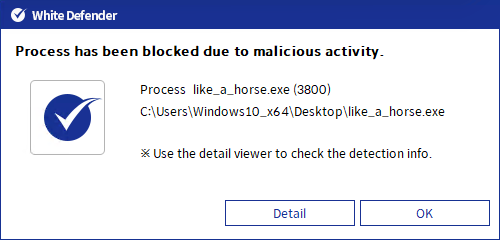
[Figure 7 Block message]
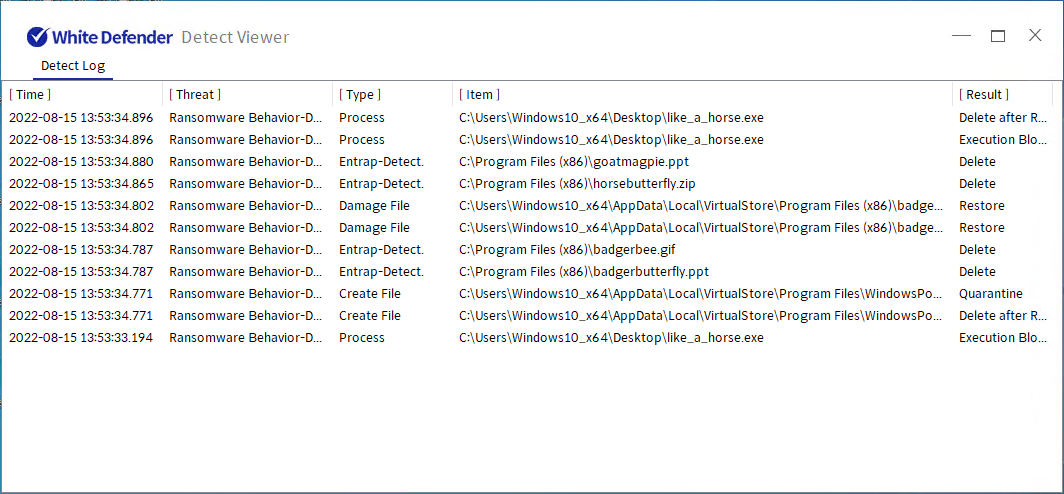
[Figure 8 Blocking details]
Watch LIKEAHORSE blocked video


