Ransomware Report
You can check the latest ransomware information.
- title
- Pwpdvl ransomware
- Registration date
- 2024-05-13
- views
- 17080
[Pwpdvl ransomware]
[Virus/malware activity reported: Pwpdvl ransomware]
A security breach believed to be in the form of Pwpdvl ransomware has occurred,
so we would like to confirm the situation and provide a warning as follows.
Pwpdvl ransomware
The ransomware is called Pwpdvl and appears to be changing all files with file name.extension.pwpdvl.
How it works
file version
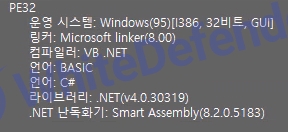
[Figure 1 Ransomware executable file compiler information]
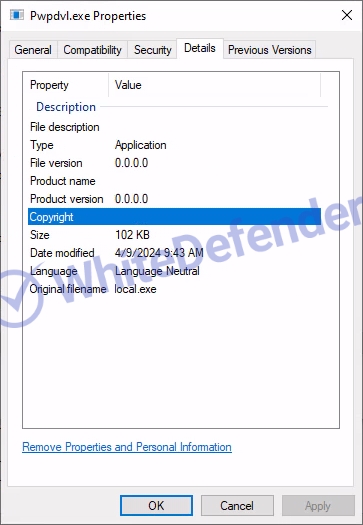
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
Based on VB.Net, the ransomware itself uses a commercial program called Smart Assembly, and the internal code is obfuscated. When activated, known data and security programs are killed using taskkill, and shadow copies are checked and deleted using powershell. The attack targets all drives, and after a successful attack, a txt file is created in each location.
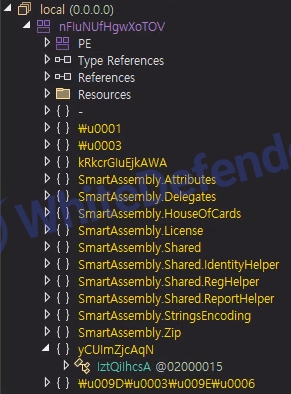
[Figure 3 When decompiling the .NET project, the internal contents are obfuscated]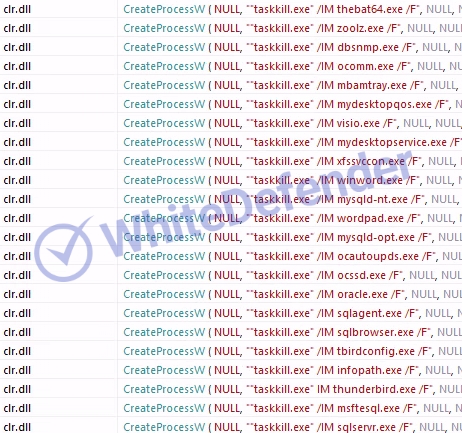
[Figure 4: Force termination of security programs and data-related programs using taskkill during dynamic analysis]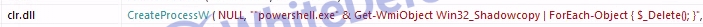
[Figure 5 Search and delete shadow copies using powersell]
Infection results
The information file is created as
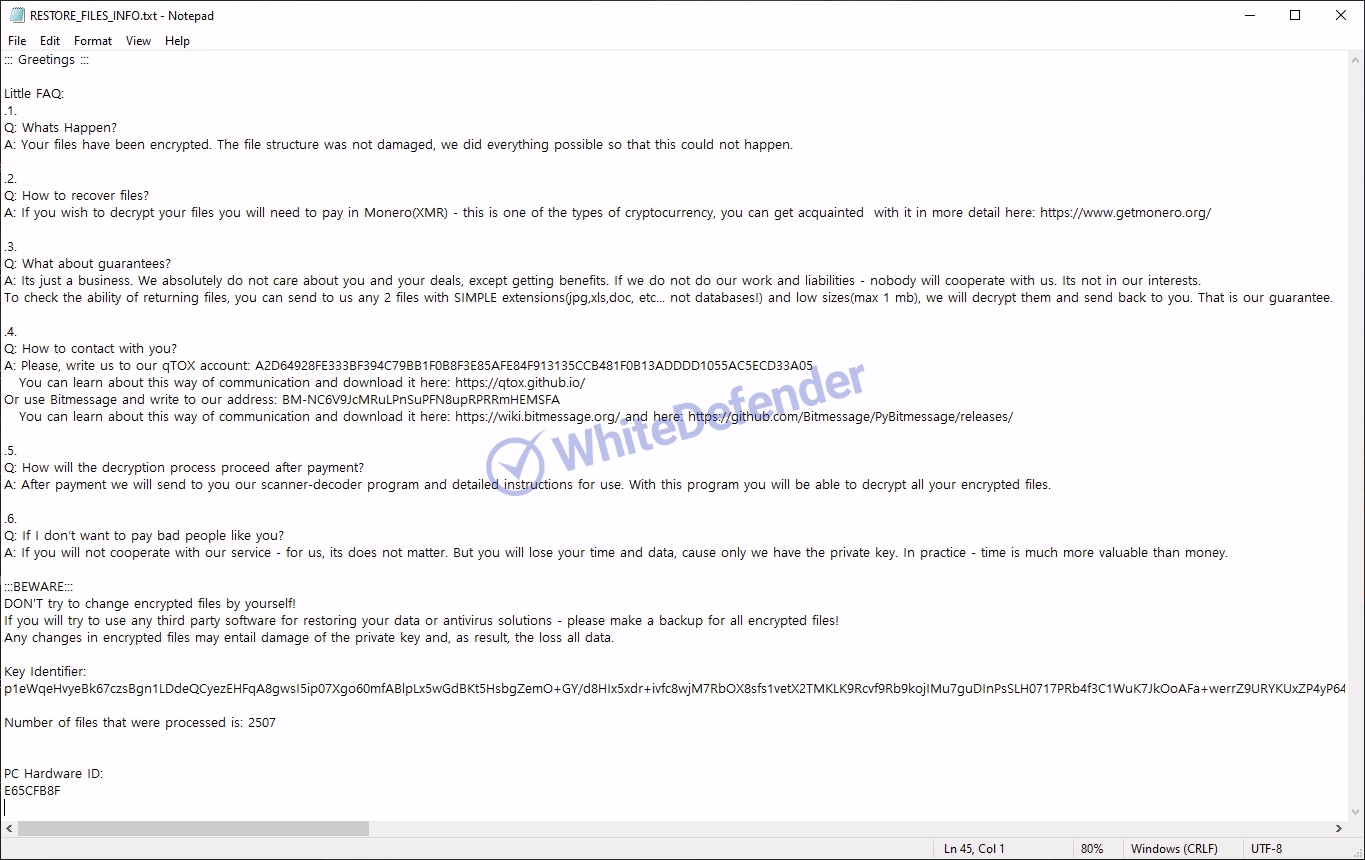
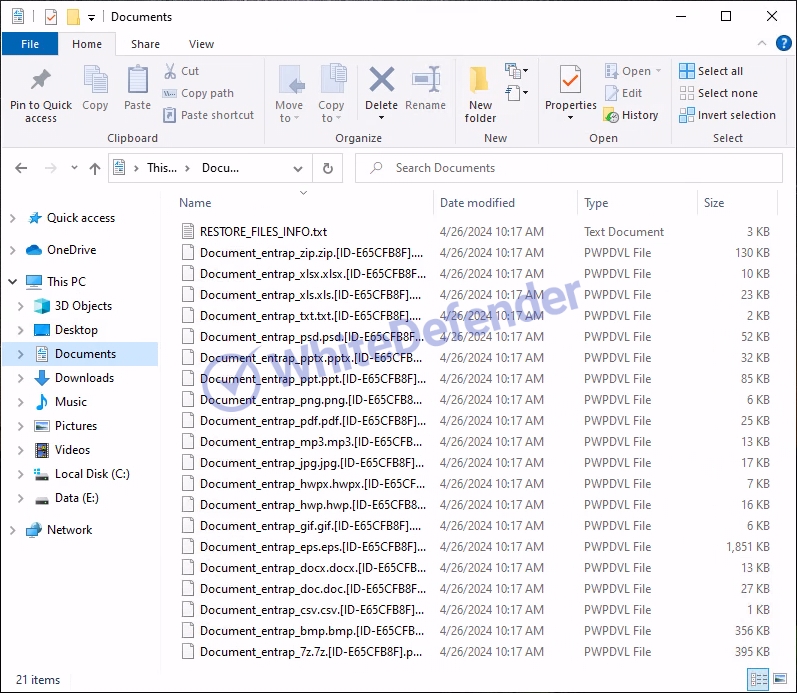
[Figure 6 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
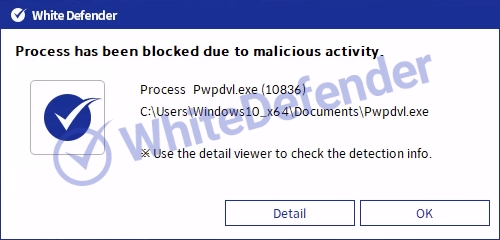
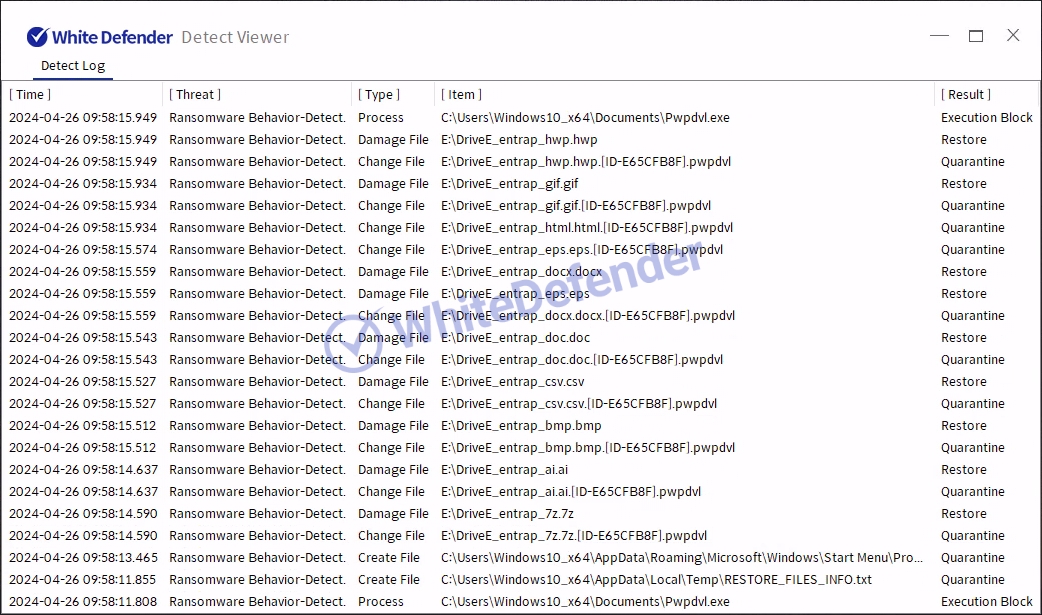
[Figure 7 Block message]
Go to the Pwpdvl blocking video

- Previous post
- Hitobito ransomware
- next post
- Divinity Ransomware

