Ransomware Report
You can check the latest ransomware information.
- title
- MadCat Ransomware
- Registration date
- 2024-04-15
- views
- 3651
[ MadCat ransomware ]
[Virus/Malware Activity Report: MadCat Ransomware]
Due to a breach believed to be in the form of MadCat ransomware,
we would like to confirm the situation and provide a warning as follows.
MadCat Ransomware
The ransomware in question is called MadCat, and it appears to be changing all files by file name, extension, and individual 4 digits.
How it works
file version
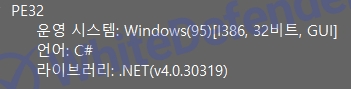
[Figure 1 Ransomware executable file compiler information]
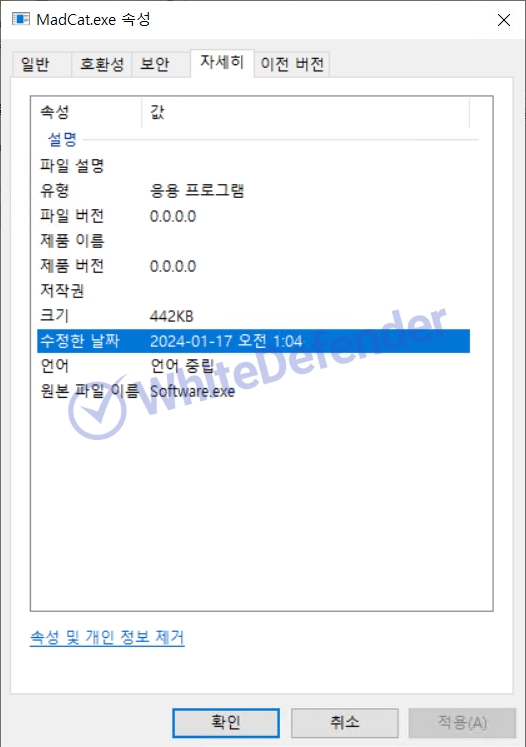
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
NET-based Chaos-based ransomware that deletes shadow copies and backup catalogs (servers) and disables Windows recovery and execution error notifications. Additionally, the execution of the task manager is prevented by adding a security policy to the Windows registry. The Chaos family usually executes the ransomware after copying it to the Roaming folder and creates a shortcut (url) file in the startup program folder.
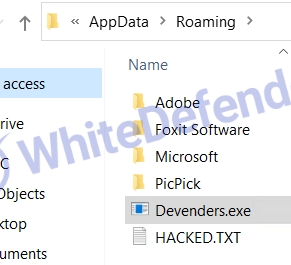
[Figure 3 Ransomware copied to Roaming folder]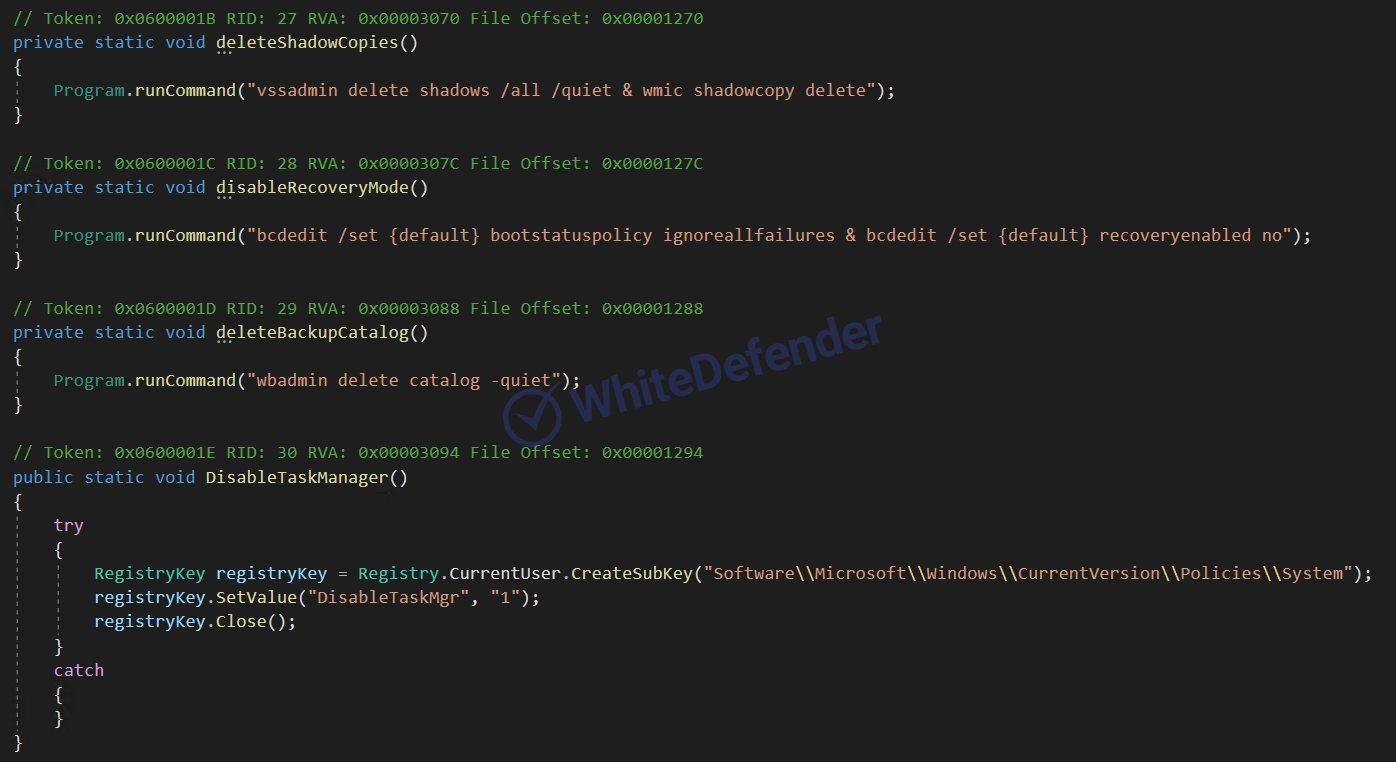
[Figure 4 Static code with several security-related settings]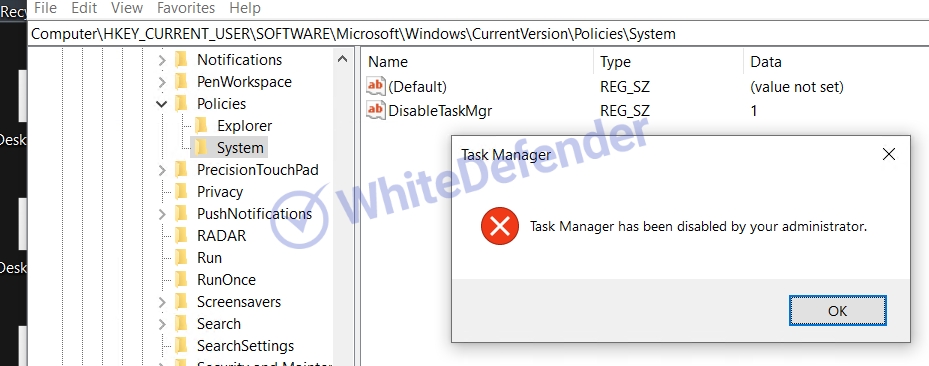
[Figure 5 Registry with task manager inactivation policy added and error when running]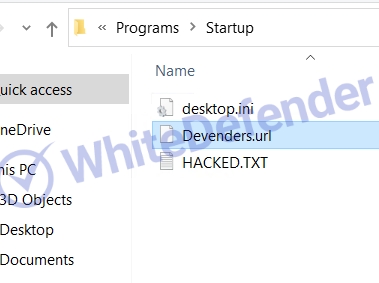
[Figure 6 Shortcut (URL) to ransomware added to startup program folder]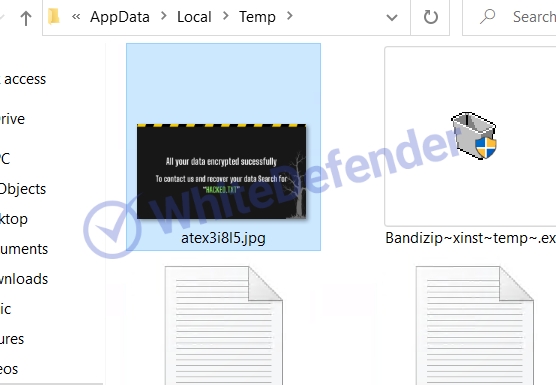
[Figure 7 Desktop image created in temporary folder]
Infection results
The information file is created as
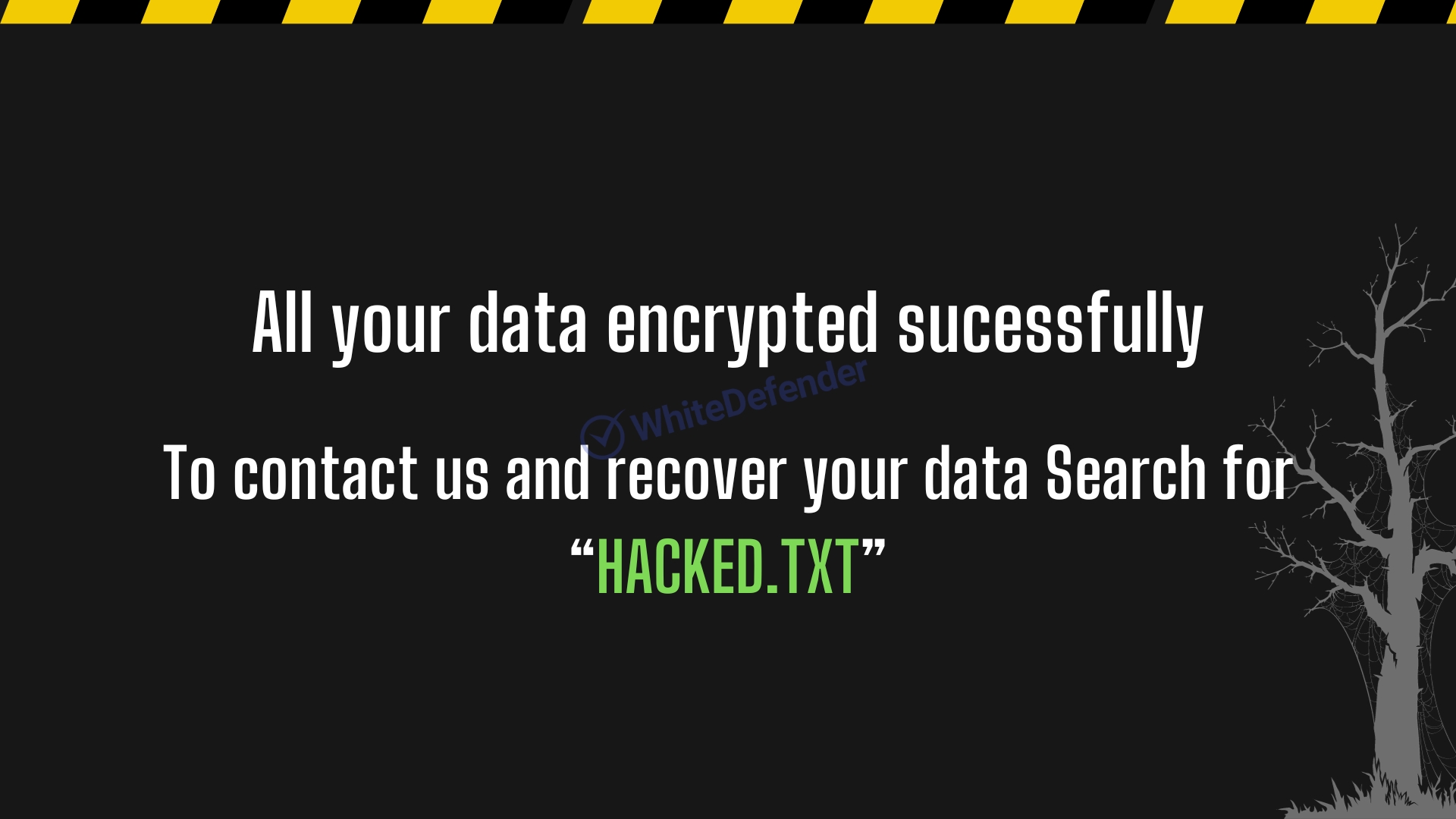
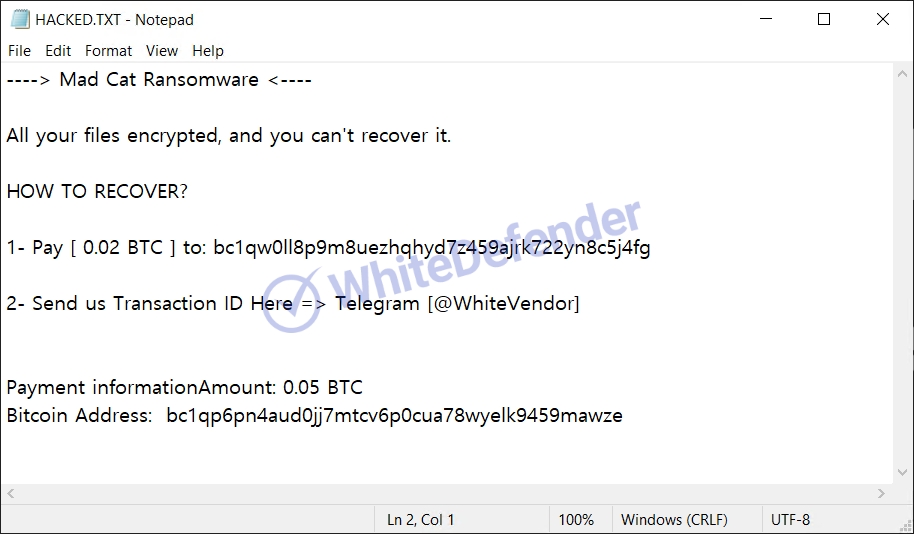
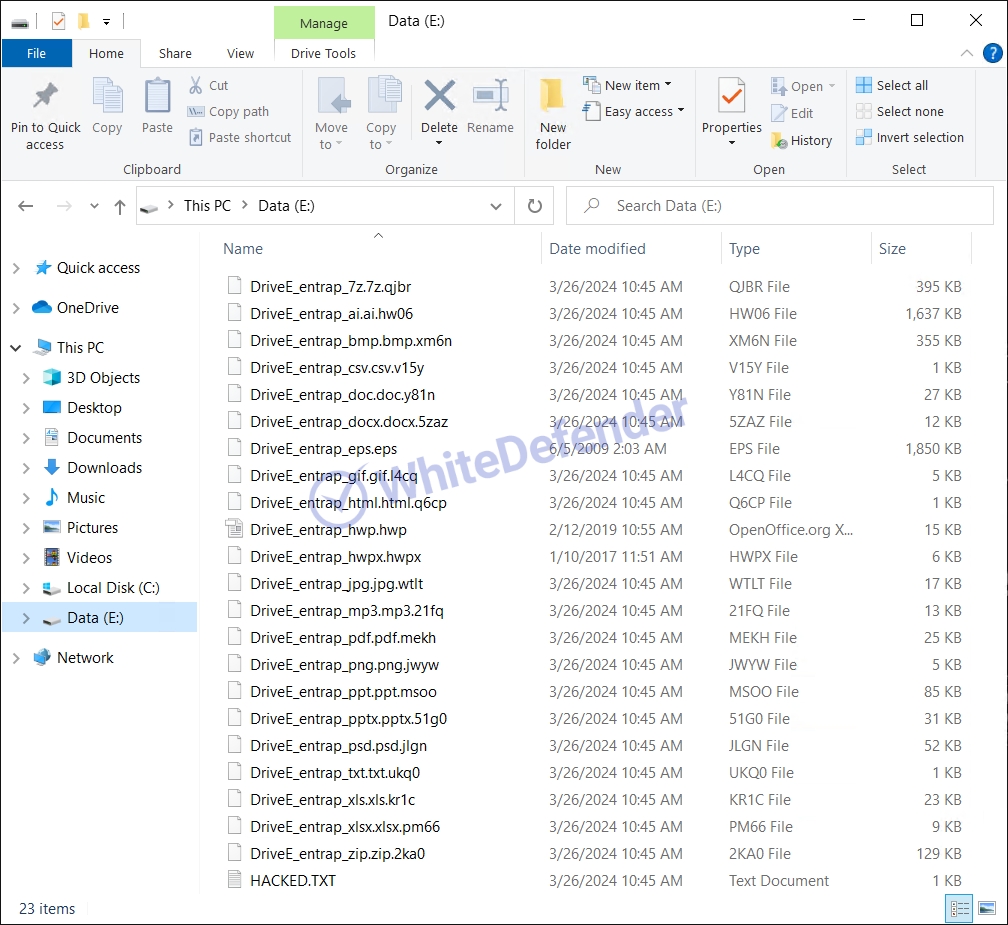
[Figure 8 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
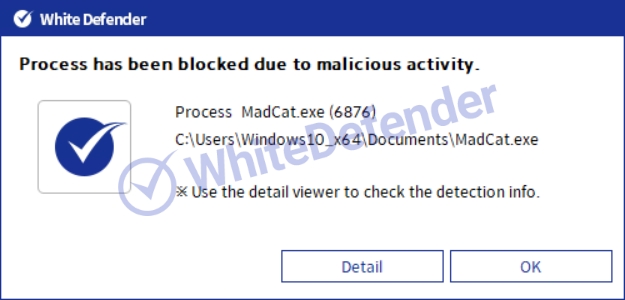
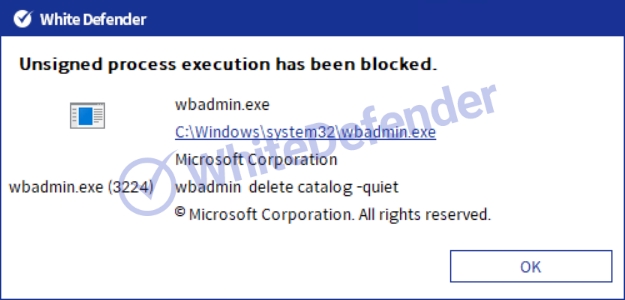
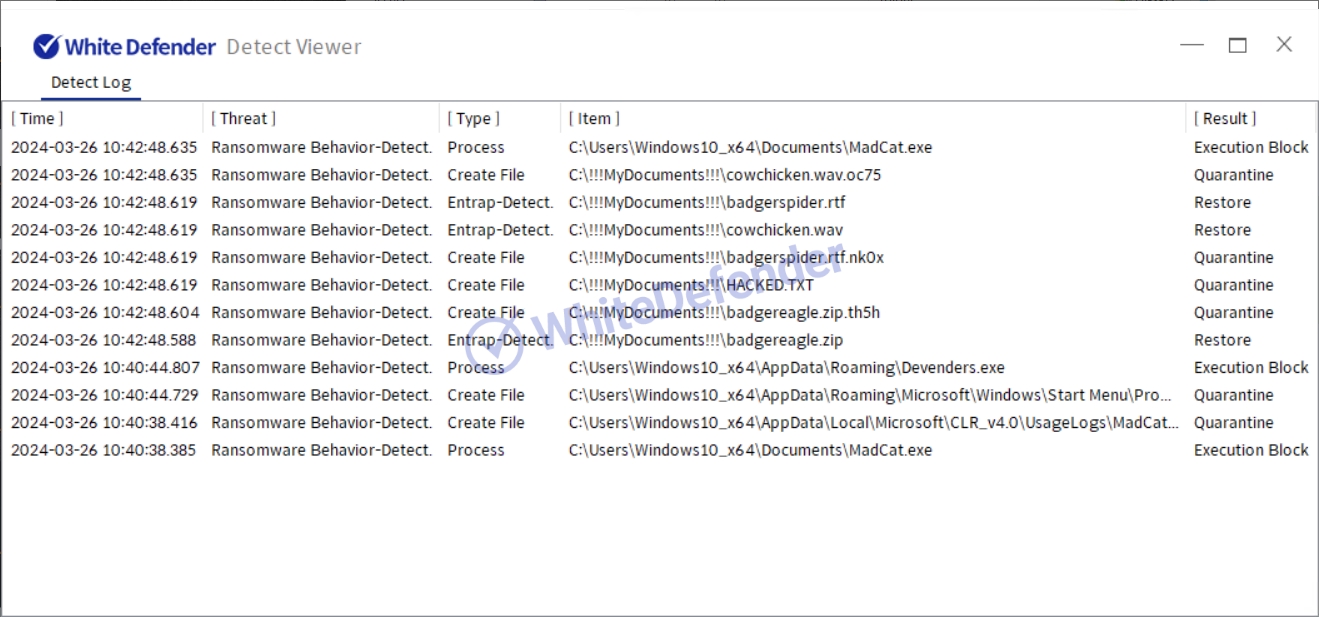
[Figure 9 Block message]
Watch the MadCat blocking video

- Previous post
- Jaff ransomware
- next post
- Sepsis ransomware

