Ransomware Report
You can check the latest ransomware information.
- title
- Sepsis ransomware
- Registration date
- 2024-04-08
- views
- 3802
[ Sepsis ransomware ]
[Virus/malware activity reported: Sepsis ransomware]
Due to a breach believed to be in the form of Sepsis ransomware,
we would like to confirm the situation and provide a warning as follows.
Sepsis ransomware
The ransomware is called Sepsis and appears to be changing all files with the file name and extension [Sepsis@protonmail.com].SEPSIS.
How it works
file version
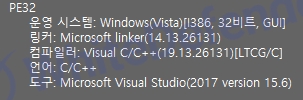
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
Ransomware executed based on C++ re-executes the executable file under the name svchost.exe in the Windows folder and registers it with Winlogon, which runs automatically when logging into Windows, so that it runs automatically even when rebooting. Encryption is performed after deleting shadow copies, restoring Windows, and disabling executable file error notifications, making it difficult to recover user data after completion.
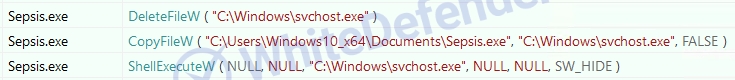
[Figure 3 Dynamic code content that copies the ransomware executable file from the initial execution location to the Windows folder and re-executes it]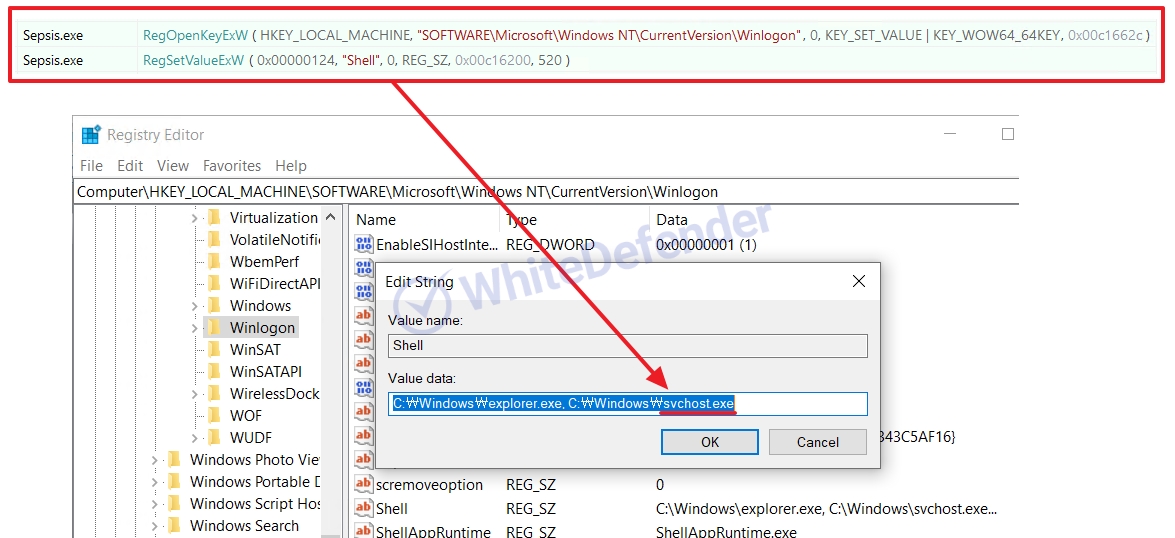
[Figure 4 Registry modification part and applied registry value during dynamic execution]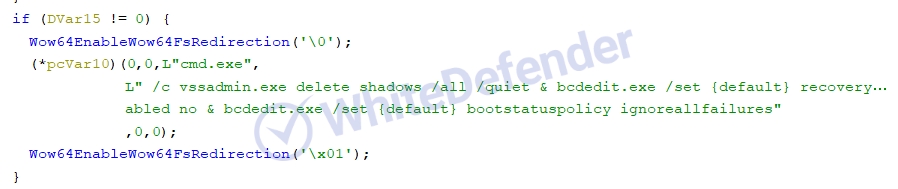
[Figure 5 Internal static code that deletes shadow copies and disables Windows restoration and execution error notification functions]
Infection results
The information file is
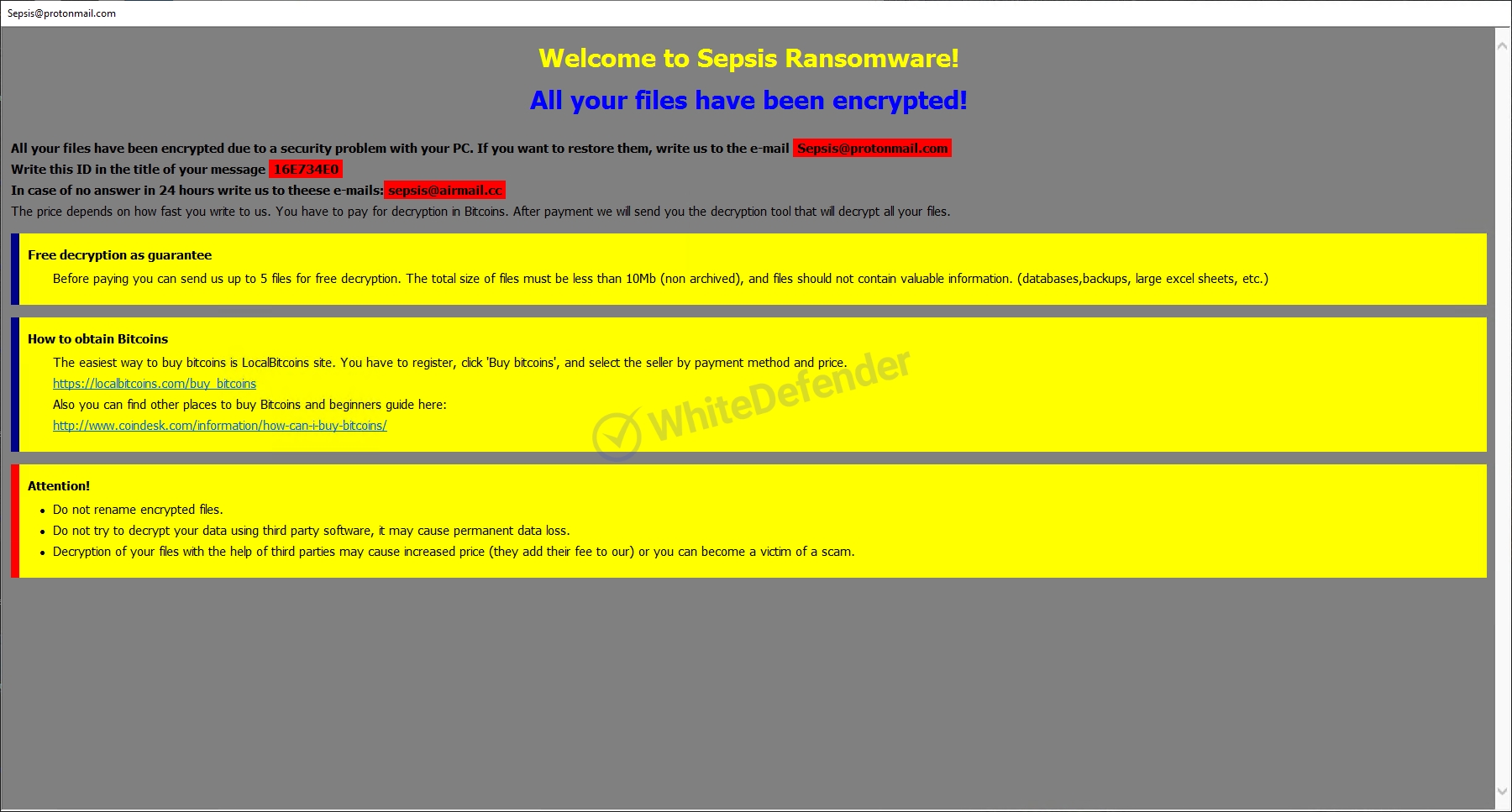
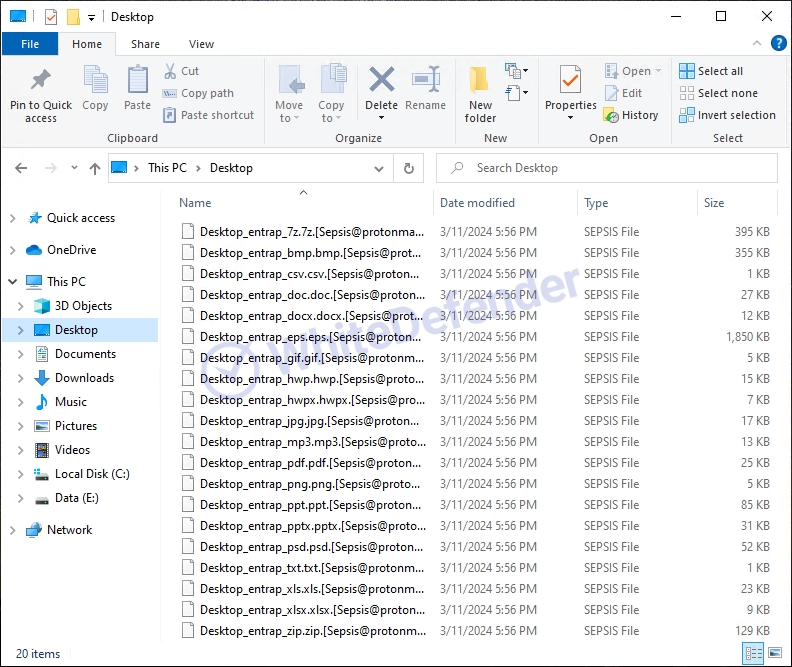
[Figure 5 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
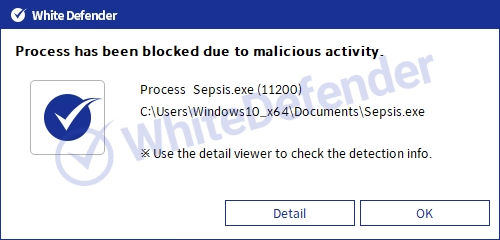
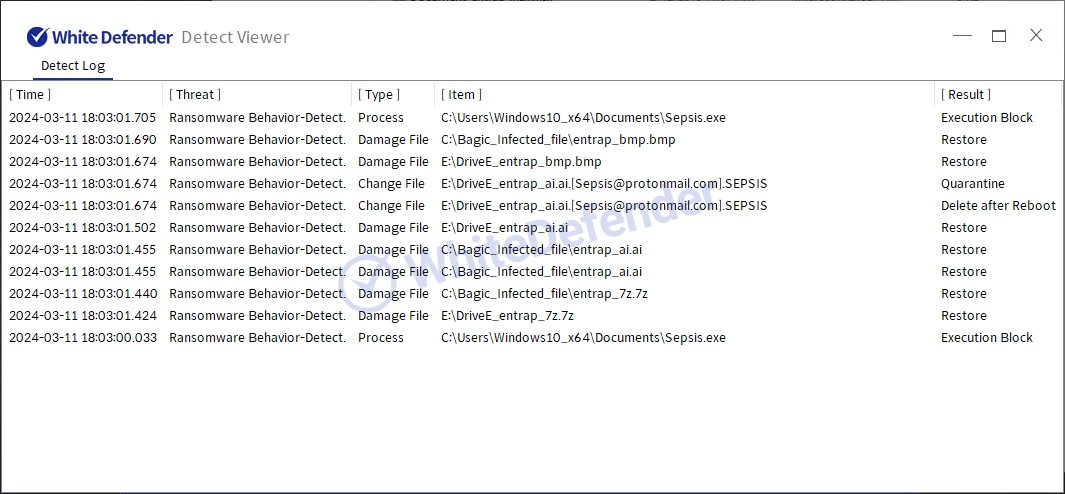
[Figure 6 Block message]
Watch the Sepsis blocking video

- Previous post
- MadCat Ransomware
- next post
- Proton Ransomware

