Ransomware Report
You can check the latest ransomware information.
- title
- Proton Ransomware
- Registration date
- 2024-04-03
- views
- 470
[ Proton ransomware ]
[Virus/Malware Activity Report: Proton Ransomware]
Due to a breach believed to be in the form of Proton ransomware,
we would like to confirm the situation and provide a warning as follows.
Proton Ransomware
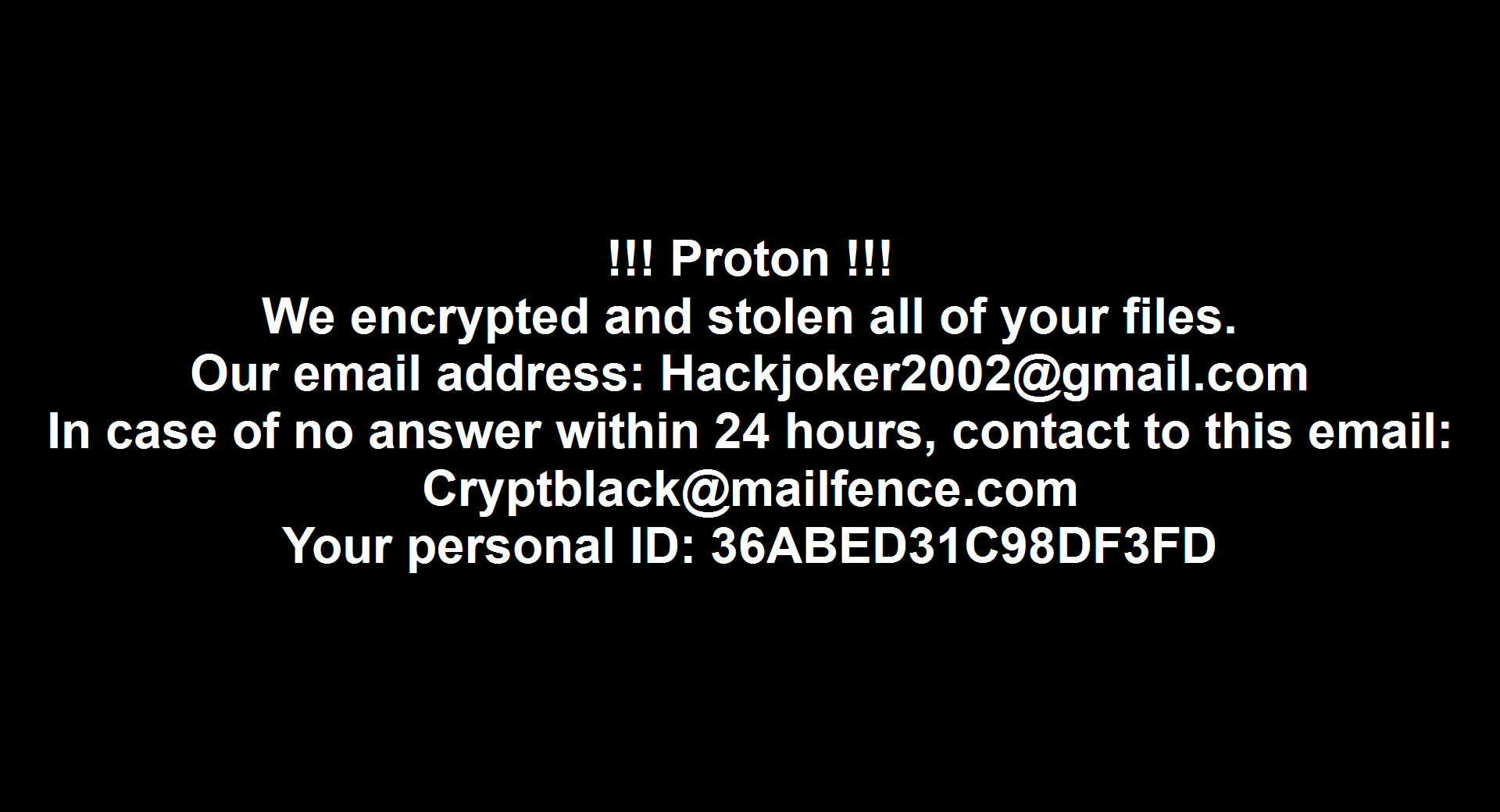
The ransomware in question is called Proton and has a file name.extension. [Hackjoker2002@gmail.com].It appears that all files are being changed by Proton.
How it works
file version

[Figure 1 Ransomware executable file compiler information]
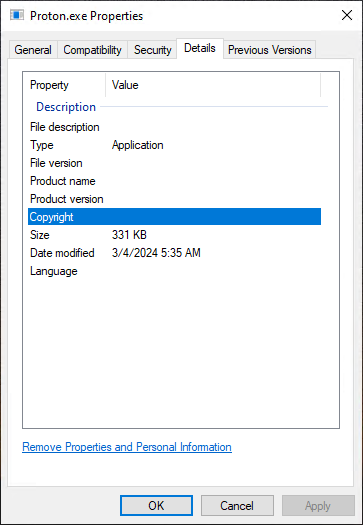
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
UPX compression is applied to the executable file based on C++. When running, it copies the ransomware's executable file to the startup program, creates a desktop image and ransomware icon in ProgramData, and encrypts all drivers after application. Because encryption is registered in the registry, an additional Windows message window related to ransomware is displayed when Windows boots.
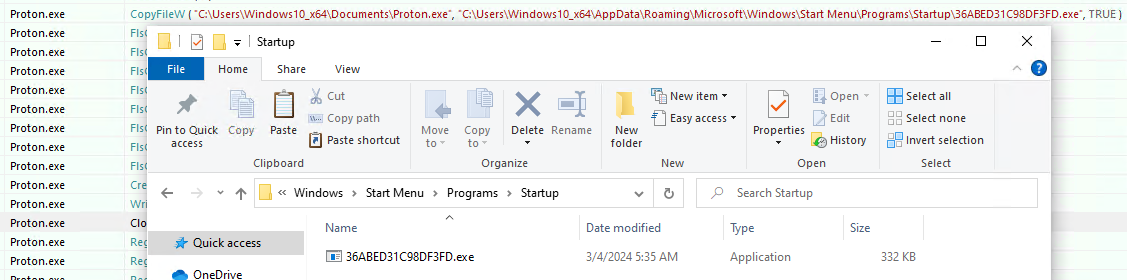
[Figure 3 Executable files and dynamic code copied to the startup program folder]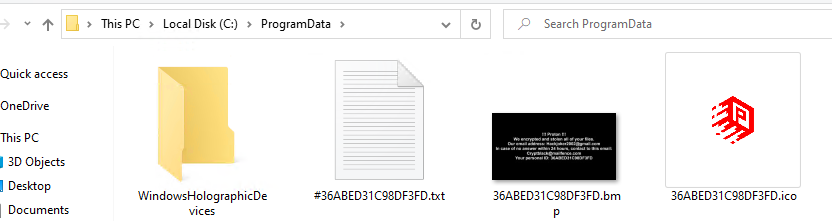
[Figure 4 Desktop note image and ransomware icon created in ProgramData]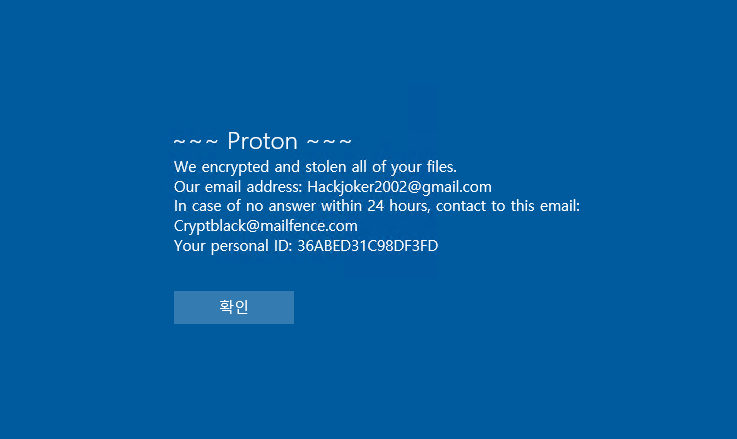
[Figure 5 Ransomware-related Windows messages displayed when Windows boots]
Infection results
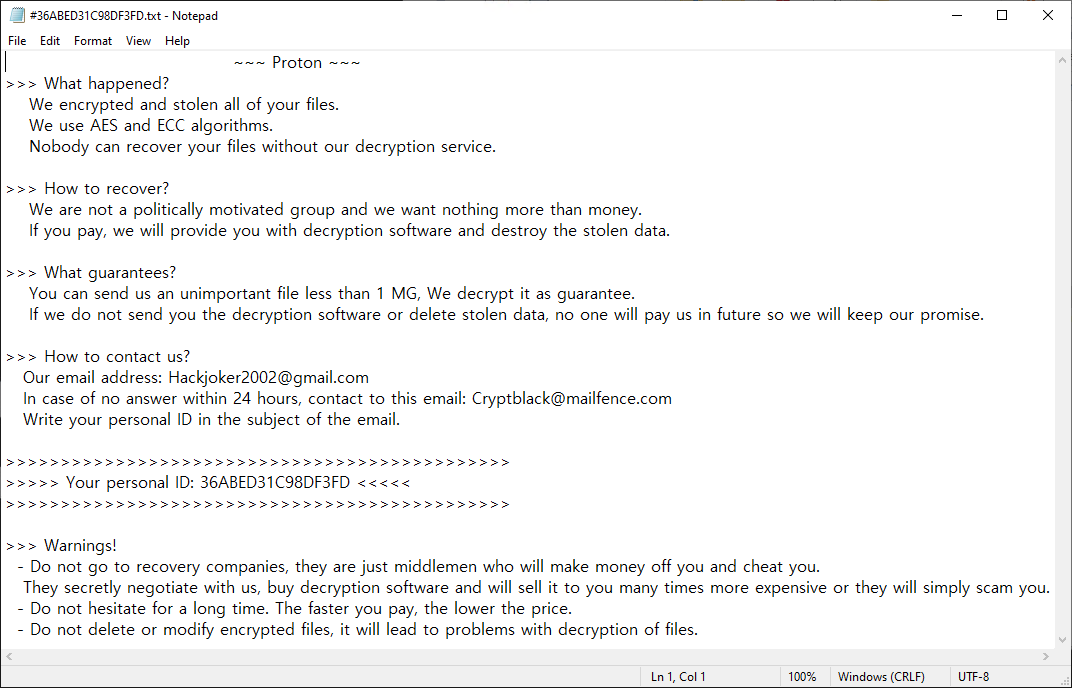
The information file is created as <#16-digit key.txt> in each path, and when encryption is performed, <file name.extension. Change the files to [Hackjoker2002@gmail.com].Proton>.
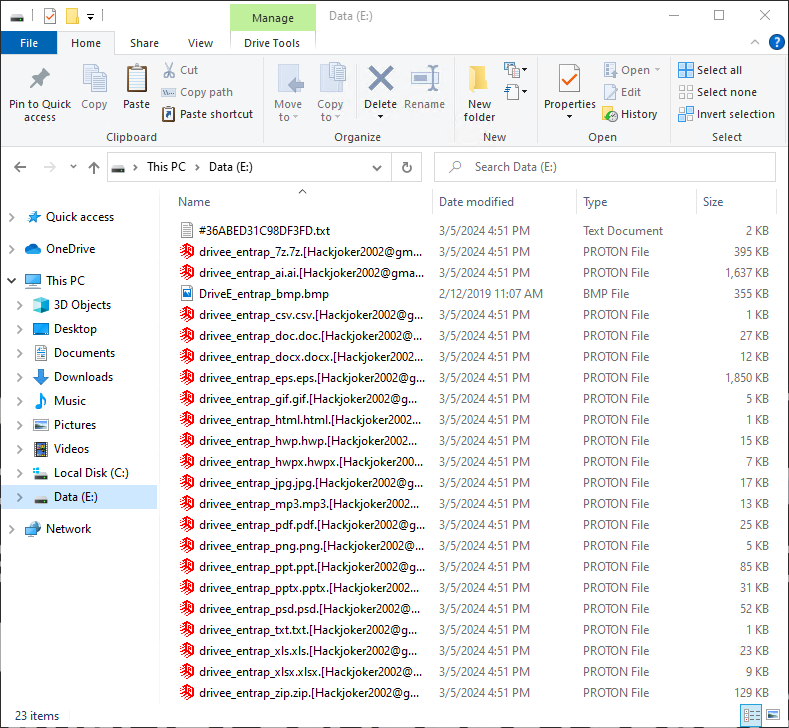
[Figure 5 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
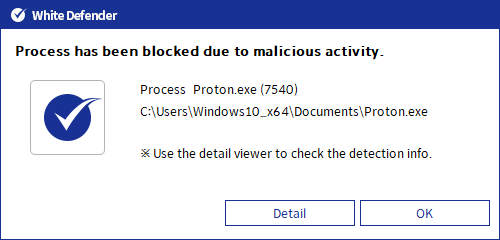
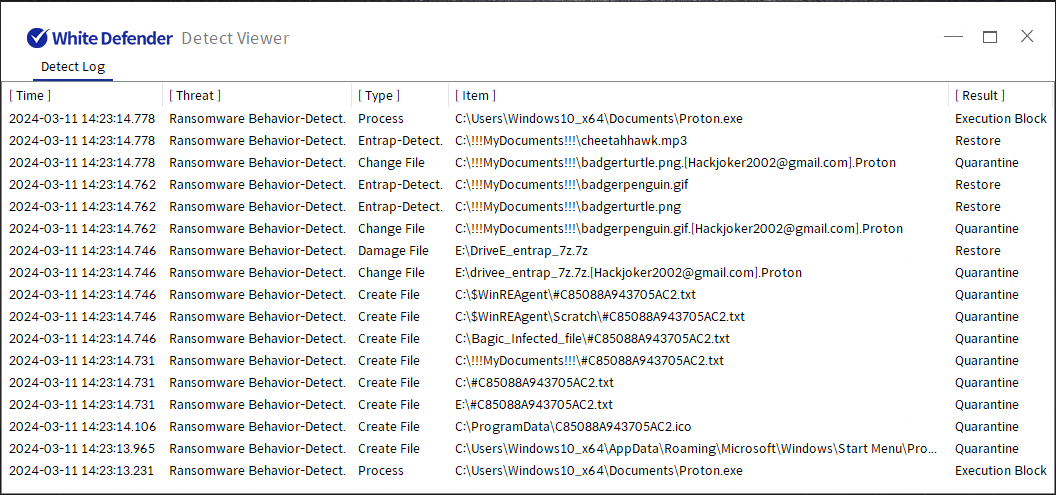
[Figure 6 Block message]
Go to the Proton blocking video

- Previous post
- Sepsis ransomware
- next post
- Slime ransomware

