Ransomware Report
You can check the latest ransomware information.
- title
- Chimera ransomware
- Registration date
- 2024-02-26
- views
- 4466
[Chimera ransomware]
[Virus/malware activity reported: Chimera ransomware]
Due to a breach believed to be in the form of Chimera ransomware,
we would like to confirm the situation and provide a warning as follows.
Chimera ransomware
The ransomware in question is called Chimera and appears to be changing all files with the file name and extension .crypt.
How it works
file version
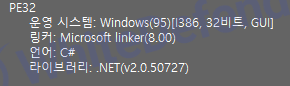
[Figure 1 Ransomware executable file compiler information]
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
Ransomware built and executed based on .NET changes the header of the currently running trusted process, executes it internally, and then encrypts the root driver. When encryption is complete, a note written in HTML is executed.
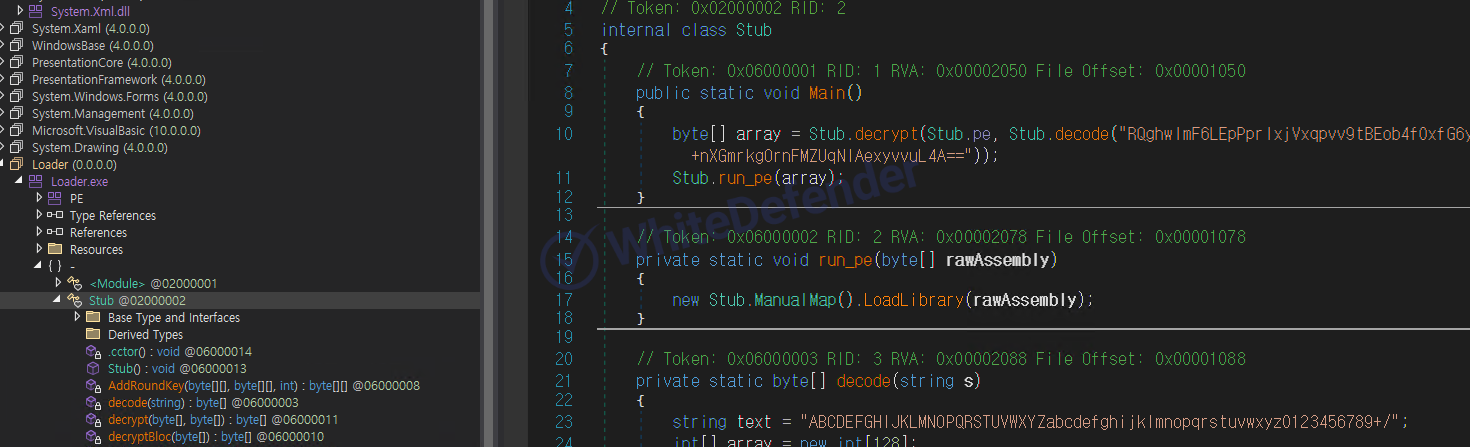
[Figure 3 Internal static code contents]
Infection results
The information file is created as < YOUR_FILES_ARE_ENCRYPTED.HTML > in each path, and when encryption is performed, the files are changed to <file name.extension.crypt>.
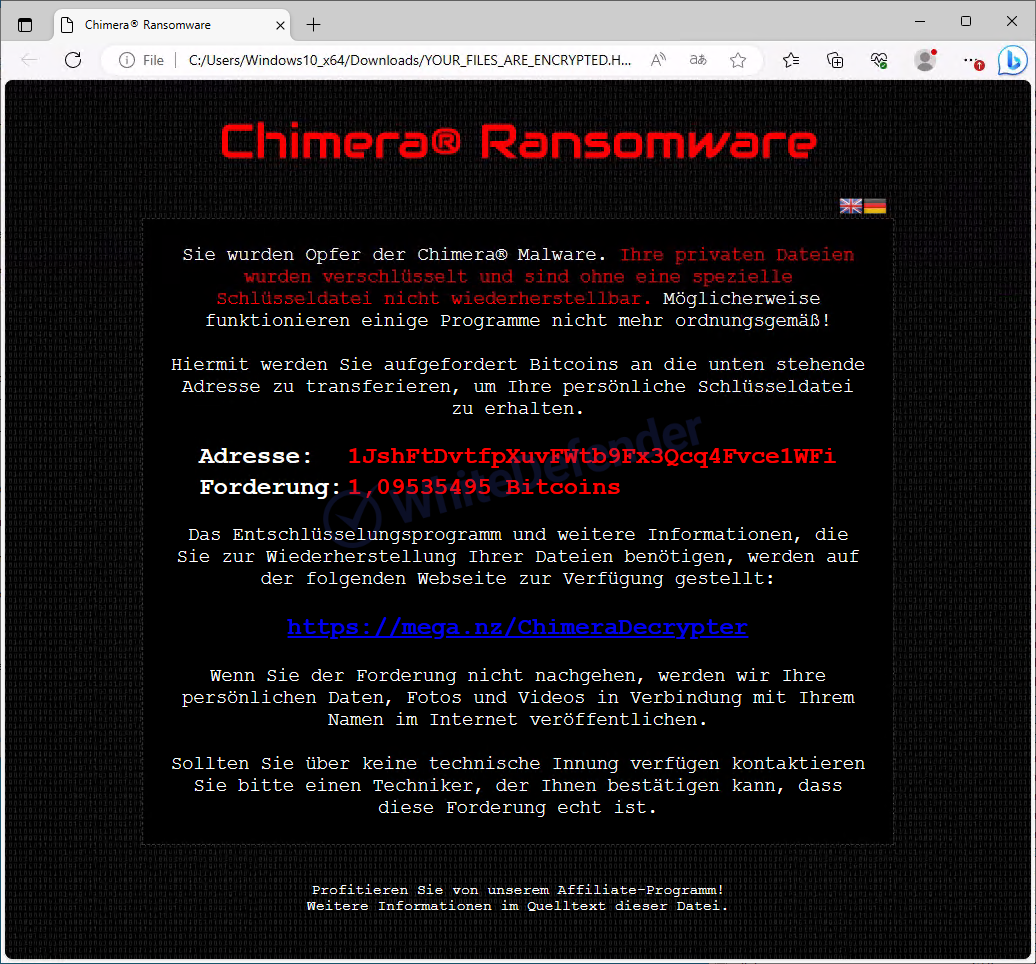
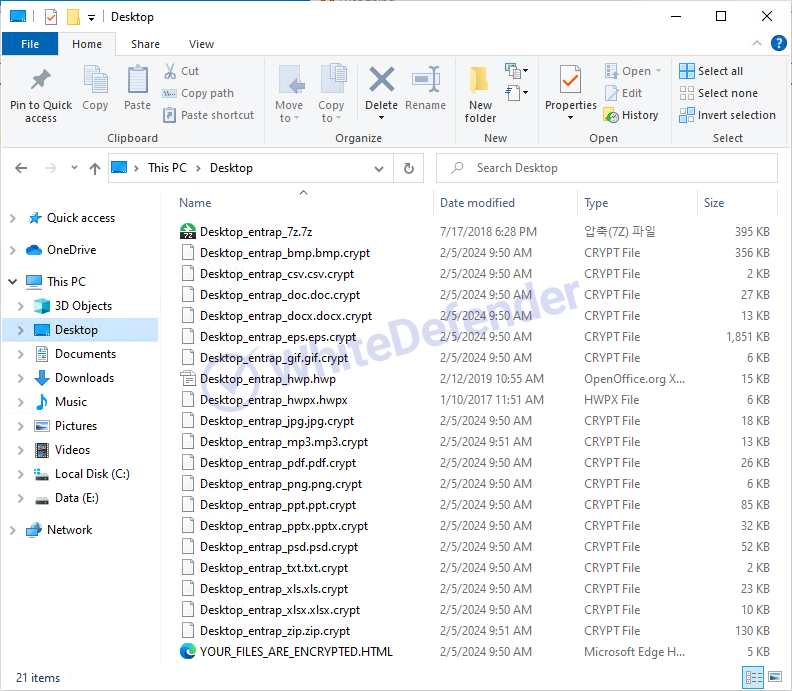
[Figure 4 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of WhiteDefender ransomware.
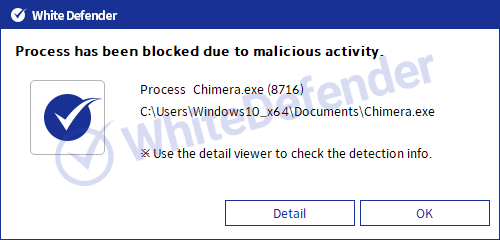
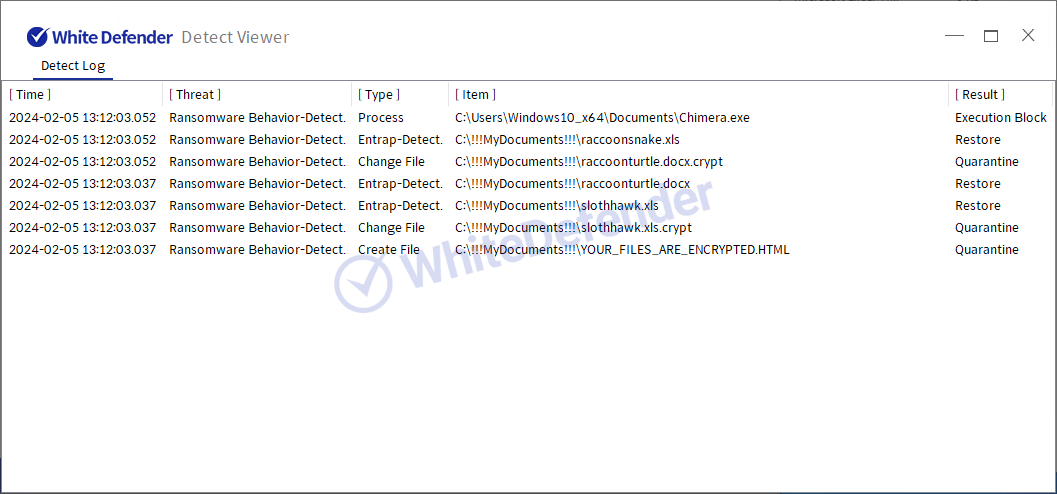
[Figure 5 Block message]
Watch the Chimera blocking video

- Previous post
- Alcatraz ransomware
- next post
- Abyss ransomware

