Ransomware Report
You can check the latest ransomware information.
- title
- Abyss ransomware
- Registration date
- 2024-02-19
- views
- 3162
[Abyss ransomware]
[Virus/Malware Activity Report: Abyss Ransomware]
Due to a breach believed to be in the form of Abyss ransomware,
we would like to confirm the situation and provide a warning as follows.
Abyss ransomware
The ransomware in question is called Abyss and has a file name.extension. It appears that all files are being changed with Abyss.
How it works
file version
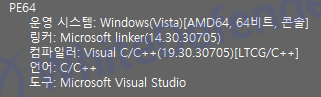
[Figure 1 Ransomware executable file compiler information]
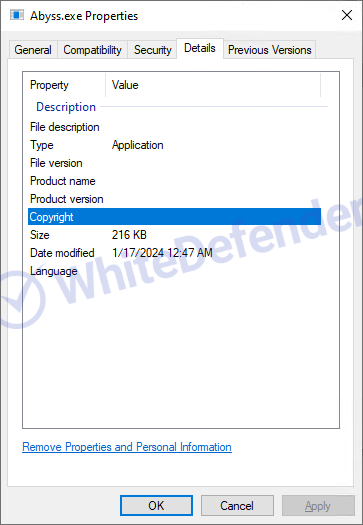
[Figure 2 File information in window properties]
Ransomware operation characteristics
-
Ransomware built and executed based on C++ checks the stop command and the name of the currently running process in data (DB and others)/backup/security-related services and forces them to terminate. Afterwards, execute the command to delete shadow copies/disable the Windows recovery function and error notification function and proceed with encryption. When encryption is complete, change the desktop image setting value in the registry.
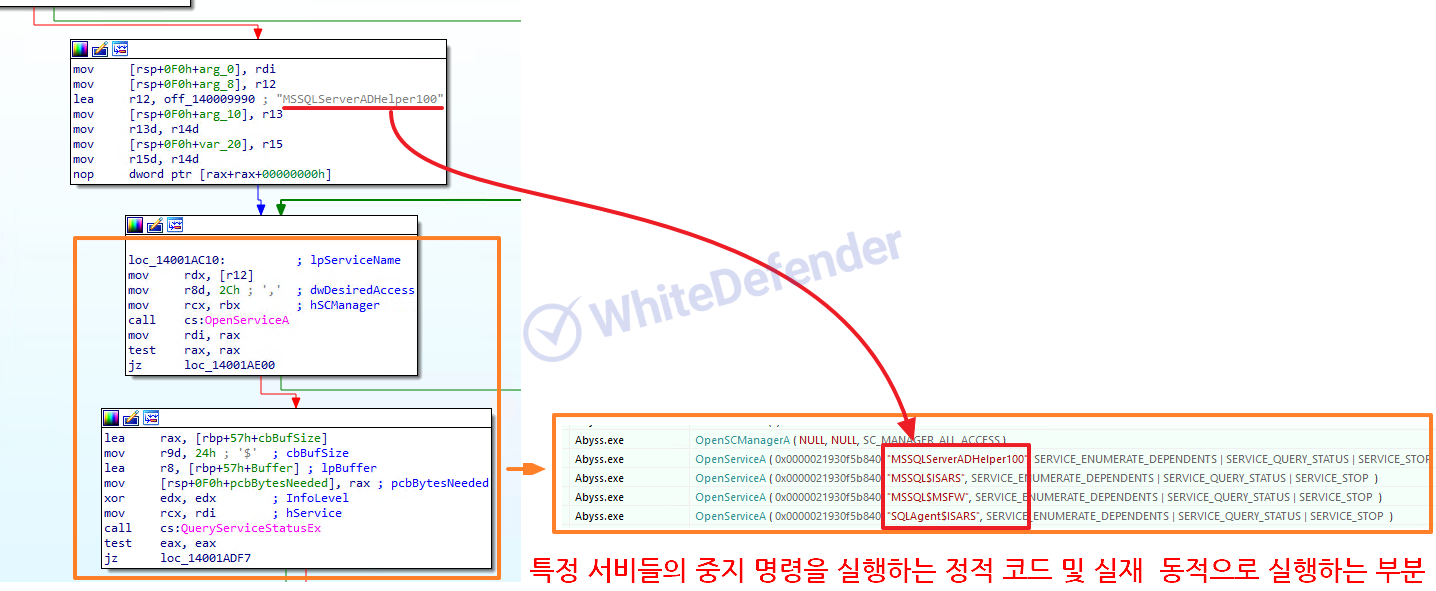
[Figure 3 Static and dynamic code for service stop command]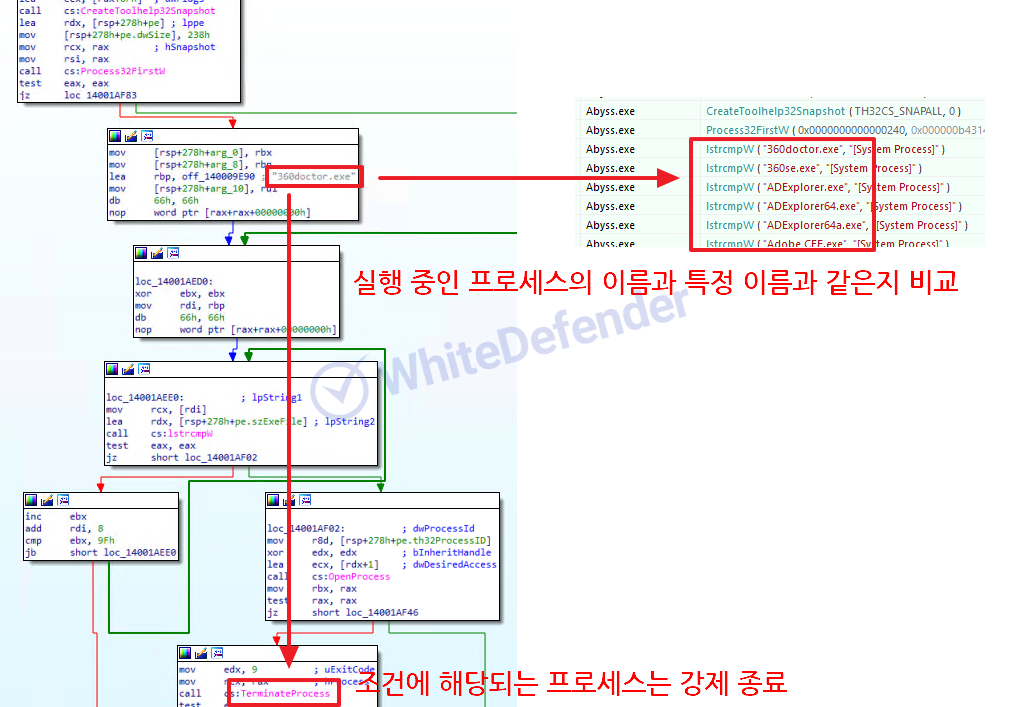
[Figure 4 Static and dynamic code for terminating a specific process]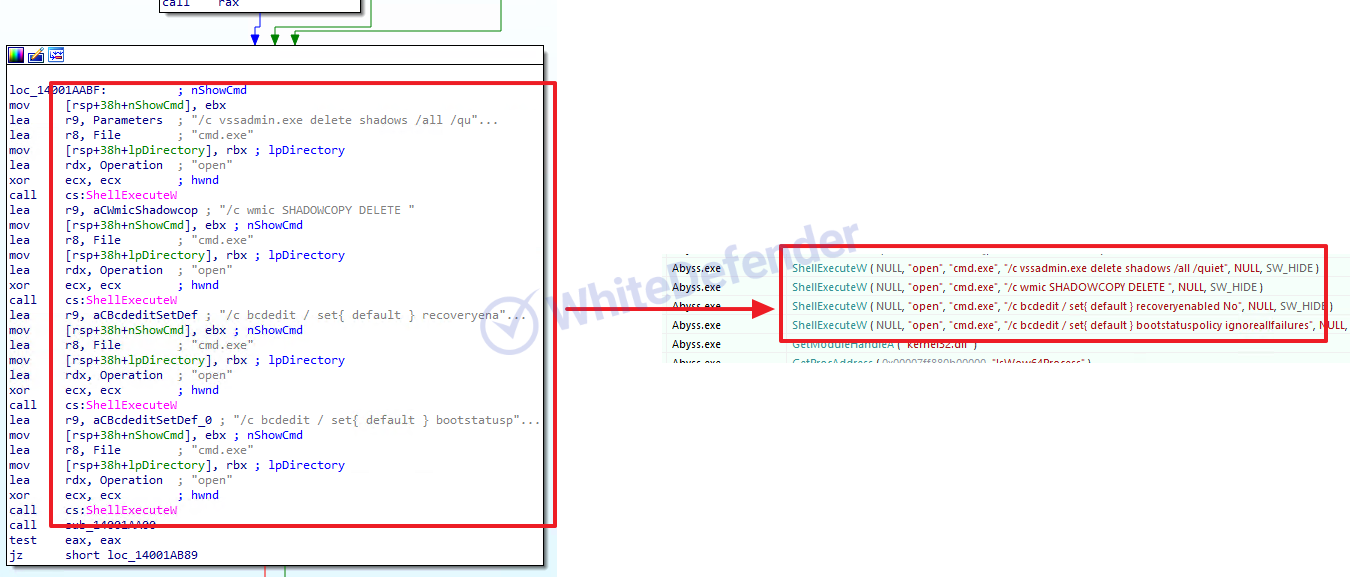
[Figure 5 Security-related release CMD command static and dynamic code]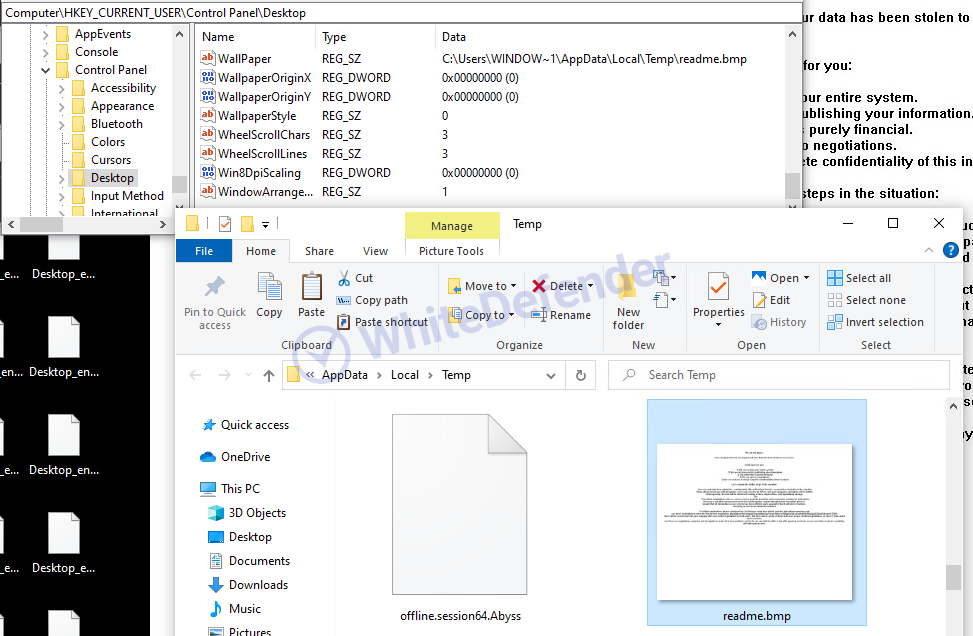
[Figure 6: Add desktop image value to registry after encryption]
Infection results
The information file is created as

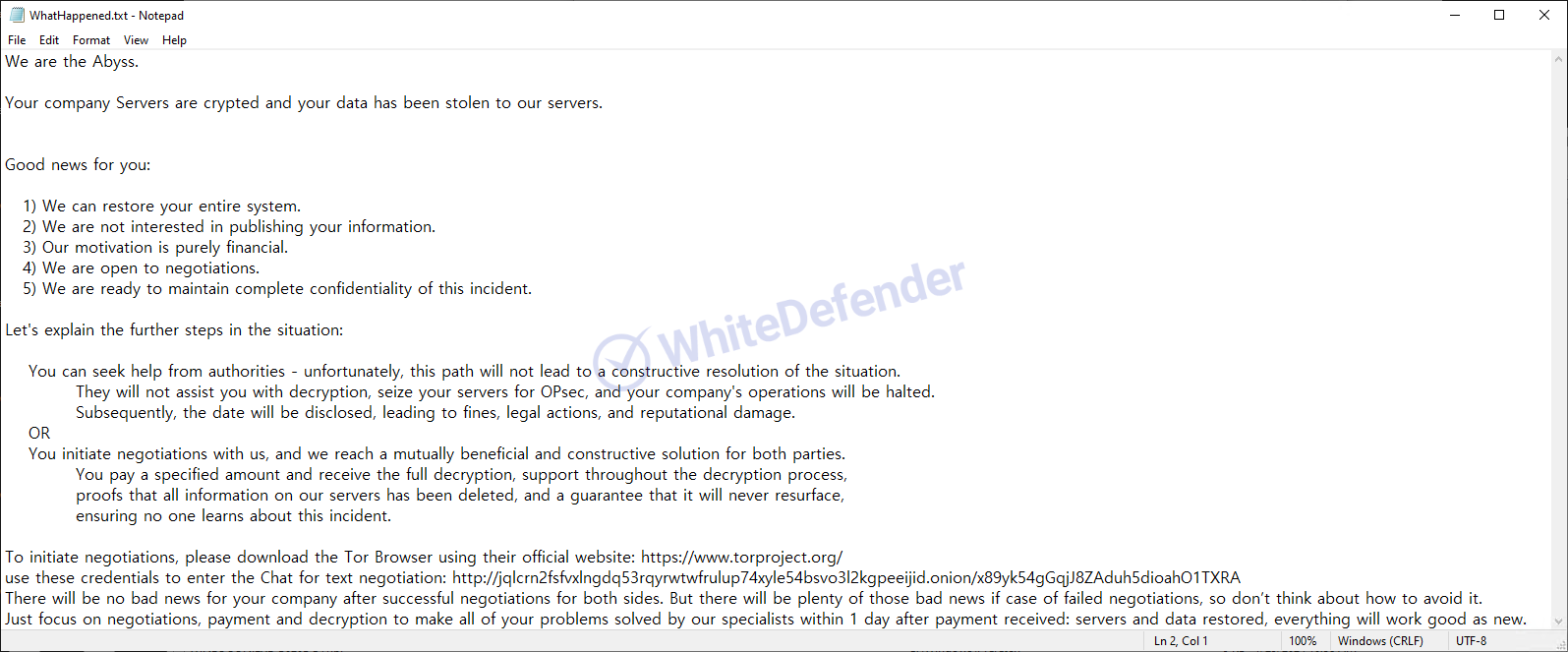
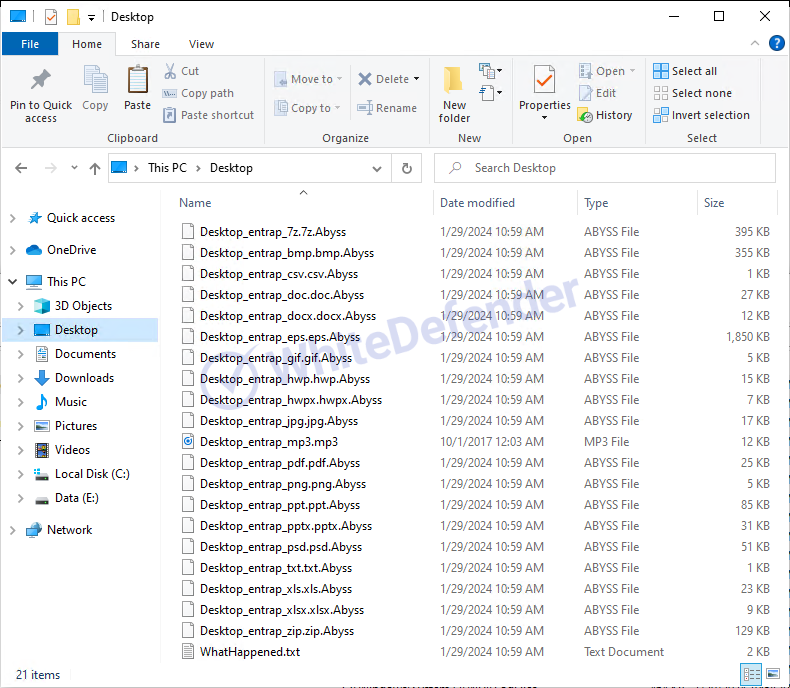
[Figure 7 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of WhiteDefender ransomware.
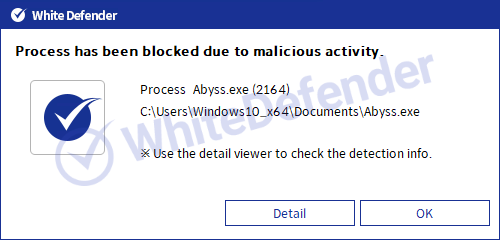
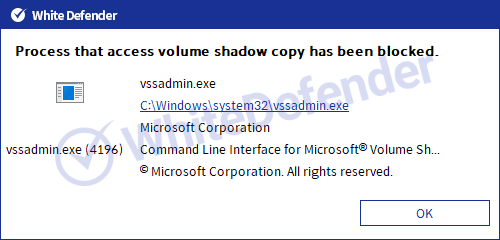
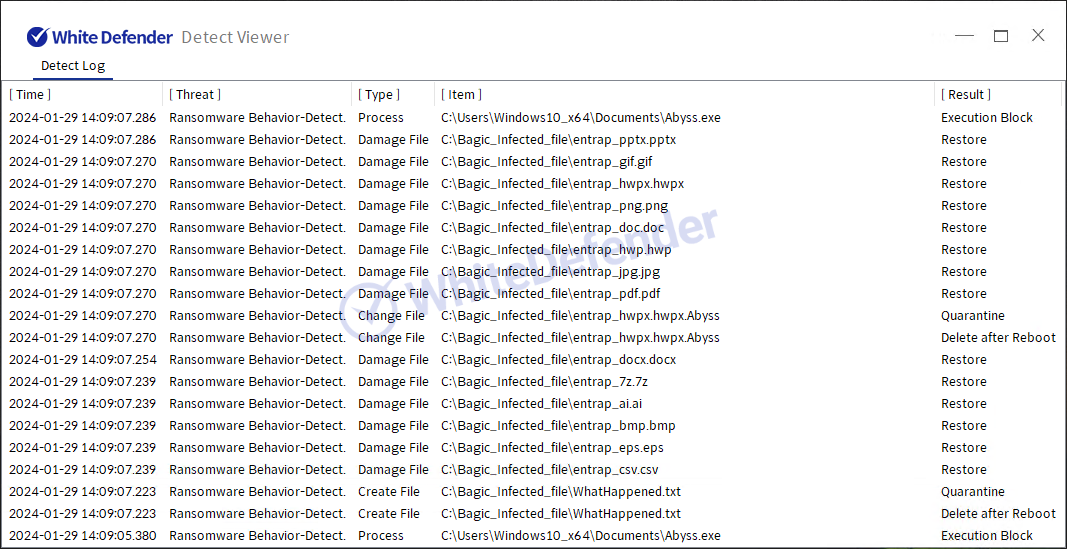
[Figure 12 Block message]
Go see the Abyss blocking video

- Previous post
- Chimera ransomware
- next post
- NewWave Ransomware

