Ransomware Report
You can check the latest ransomware information.
- title
- Seoul ransomware
- Registration date
- 2023-06-12
- views
- 8582
[ Seoul ransomware ]
[Virus/Malware Activity Report: Seoul Ransomware]
In response to a security breach believed to be in the form of Seoul ransomware,
we would like to confirm the situation and provide a warning as follows.
Seoul ransomware
The ransomware in question is called Seoul and appears to be changing the final file to a compressed file with the existing name, existing extension, and [unique ID].zip. It was created to attack companies based on the Delphi language and appears to be active recently.
How it works
file version
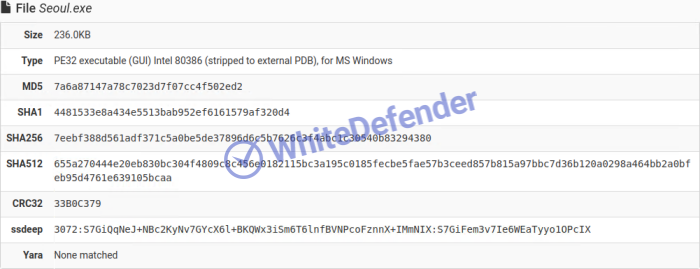
[Figure 1 File version]
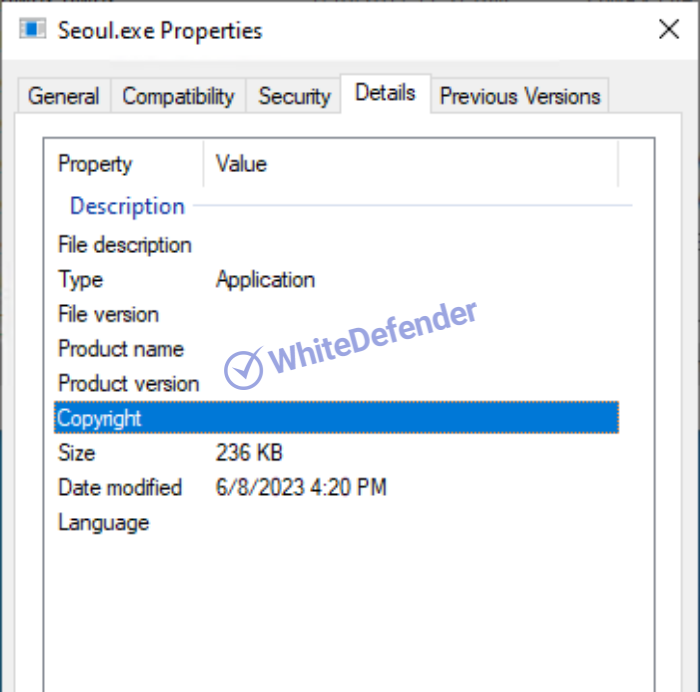
[Figure 2 File properties]
behavioral process
Re-execute and register startup program after changing execution location
Copy it from the initial execution location to the Recycle Bin of ProgramData on the root drive and rename it (randomly).
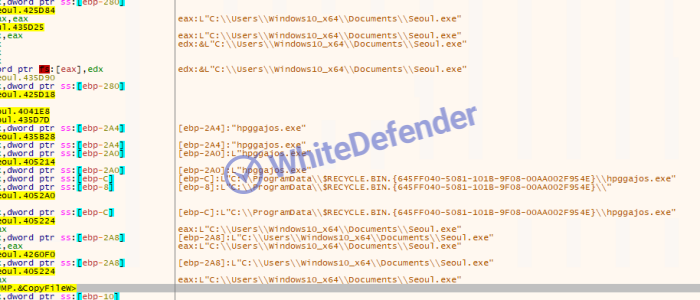
[Figure 3 Code copied from existing location to trash can and then re-executed]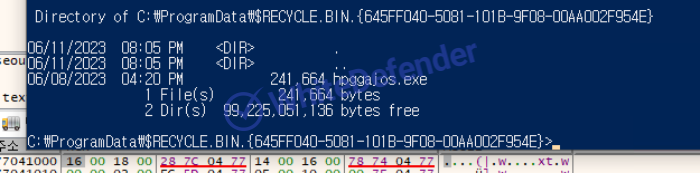
[Figure 4 Ransom file created internally when checked with CMD]Encrypted and organized into final ZIP format
All encrypted files are in zip format, and individual IDs are entered at the end of the files.
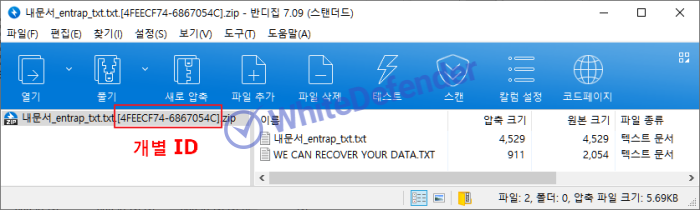
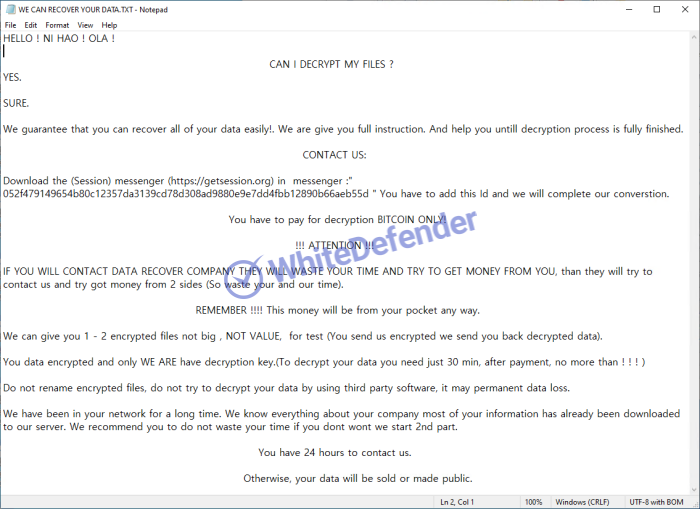
[Figure 5 Instruction notes and encrypted files inside the zip file]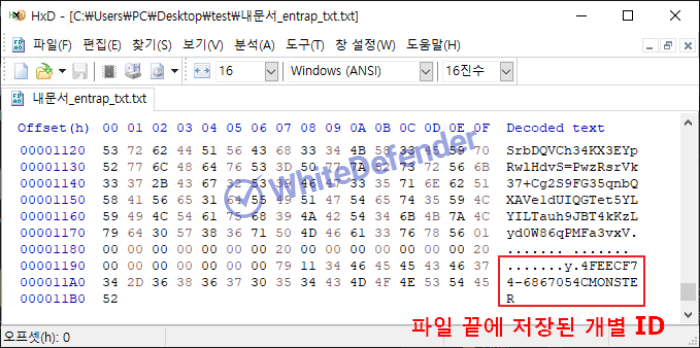
[Figure 6 Internal individual ID confirmed by HxD]
Infection results
When encryption is performed, the existing files and guidance notes are contained in a compressed form of <existing name.existing extension.[unique ID].zip>.
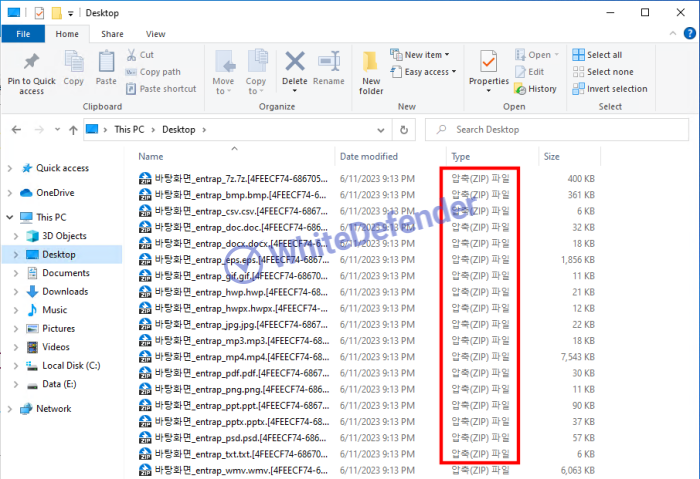
[Figure 7 Infection results]
White Defender compatible
It supports real-time automatic restoration of files that will be encrypted before the malicious actions and blocking of White Defender ransomware.
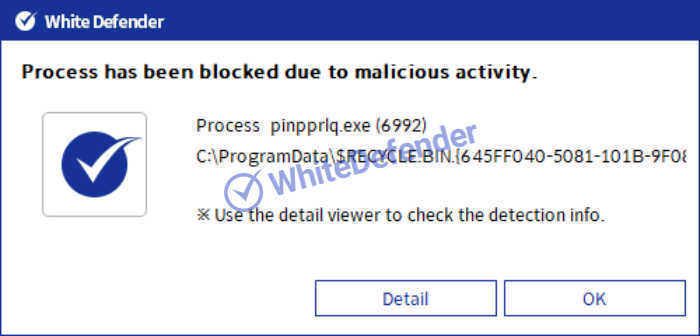
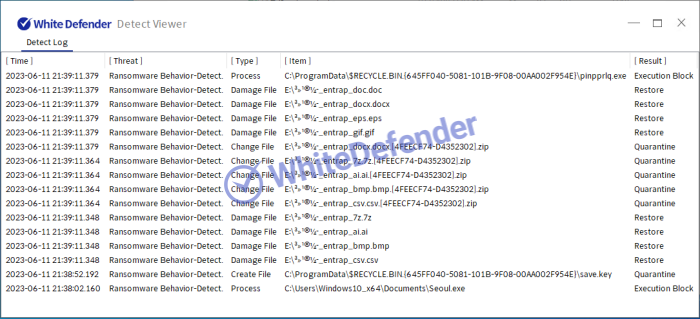
[Figure 8 Block message]
Go see the Seoul blocking video

- Previous post
- Nuke Ransomware
- next post
- Yashma ransomware

