Ransomware Report
You can check the latest ransomware information.
- title
- AllahuAkbar ransomware
- Registration date
- 2024-10-31
- views
- 98
[ AllahuAkbar ransomware ]
[ Virus/malicious code activity reported: AllahuAkbar ransomware ]
We are aware of a security breach that is believed to be AllahuAkbar ransomware.
We would like to provide the following information and warning regarding the situation.
AllahuAkbar ransomware
The ransomware is called AllahuAkbar and it appears to be changing all files to filename.extension.allahuakbar.
How it works
File version
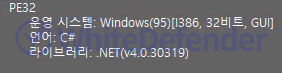
[Figure 1 Ransomware executable file compiler information]
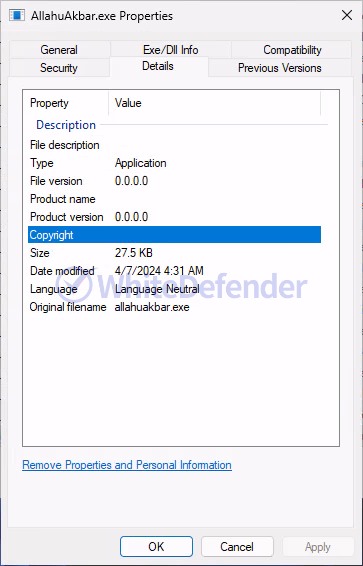
[Figure 2 File information in Windows properties]
Ransomware behavior characteristics
-
This is a C# .NET-based ransomware from the Chaos series. When executed, it is processed so that it does not work on an OS that uses a specific language, and creates a duplicate prevention string in the registry before encryption to prevent it from proceeding multiple times. When encryption is performed, shadow copies and backup catalogs are deleted and Windows recovery functions and error notification functions are disabled to make it difficult for users to recover. Additionally, by adding a registry value, the task manager is disabled and the ransomware executable file is registered in the startup program.
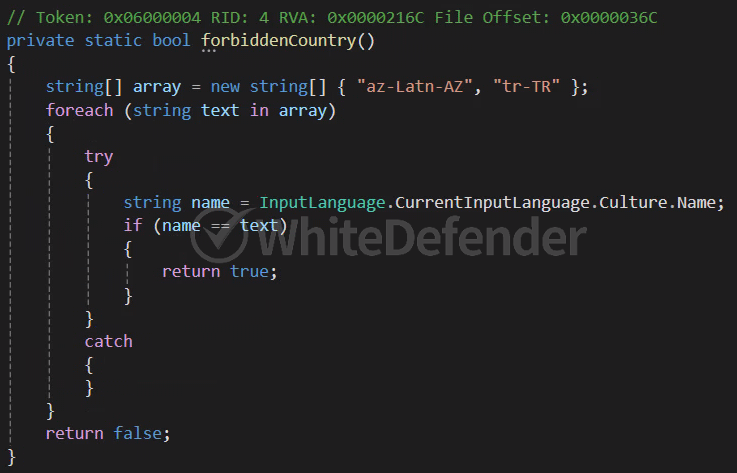
[Figure 3 Internal code to check whether a specific language is being used]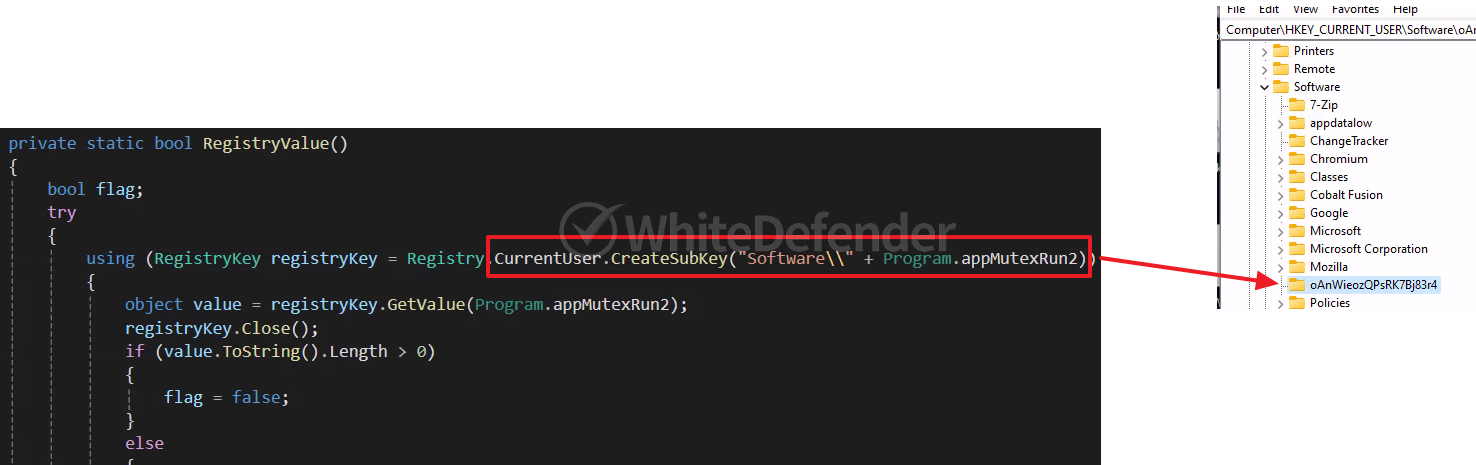
[Figure 4 Added registry values and internal code to prevent duplicate encryption execution]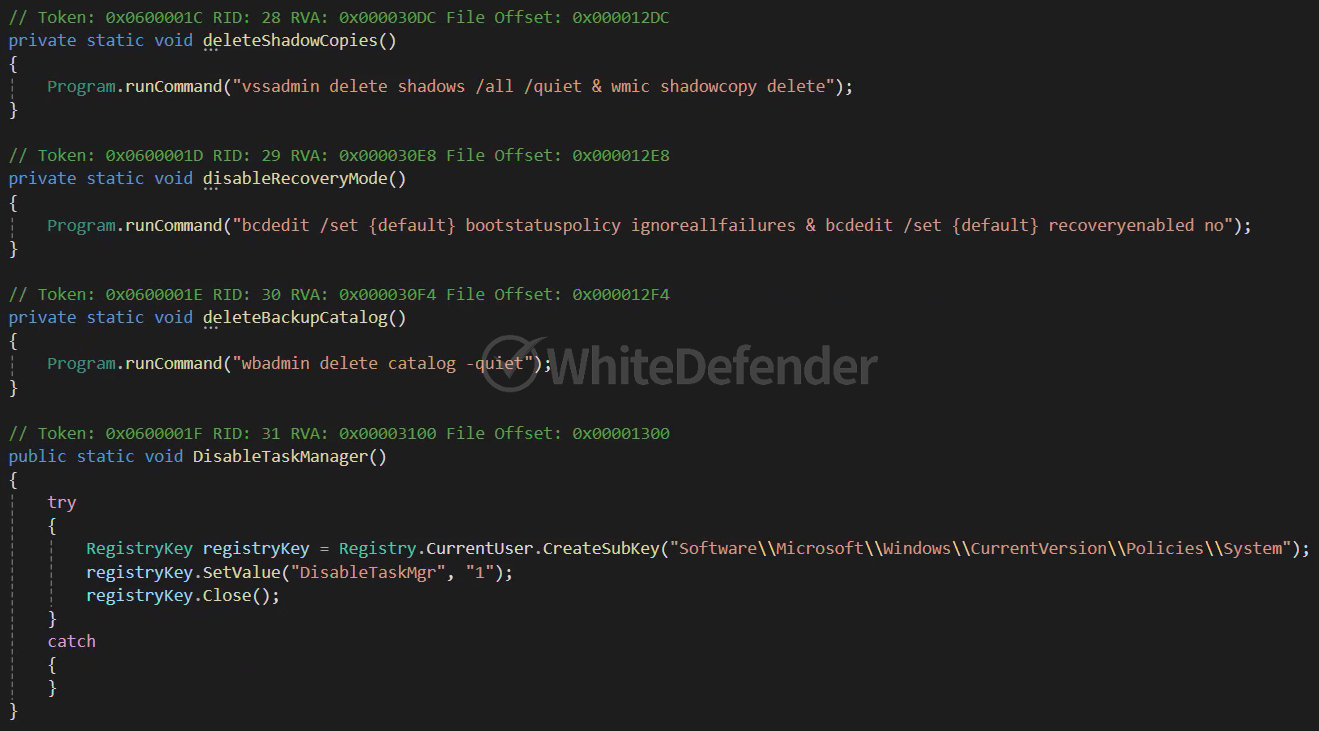
[Figure 5: Disabling various recovery-related functions and task manager]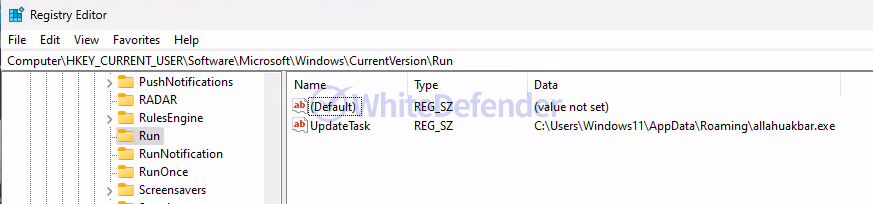
[Figure 6 Adding ransomware executable file to the registry location of startup programs]
Infection results
A guide file is created in each folder location with the name < how_to_decrypt.txt >, and each encrypted file is changed to < file name. extension.allahuakbar >. After encryption is complete, run the txt note.
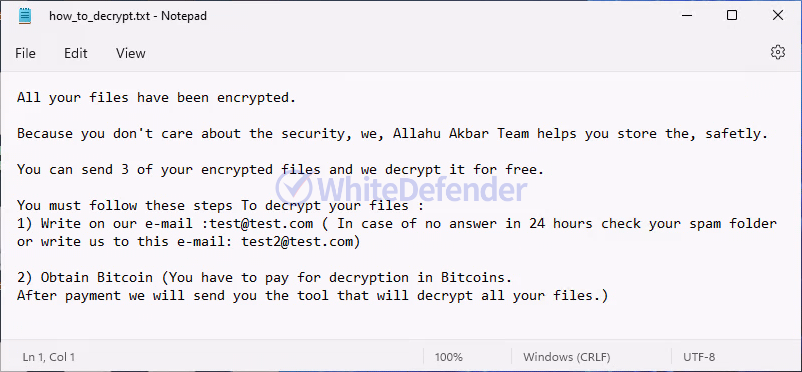
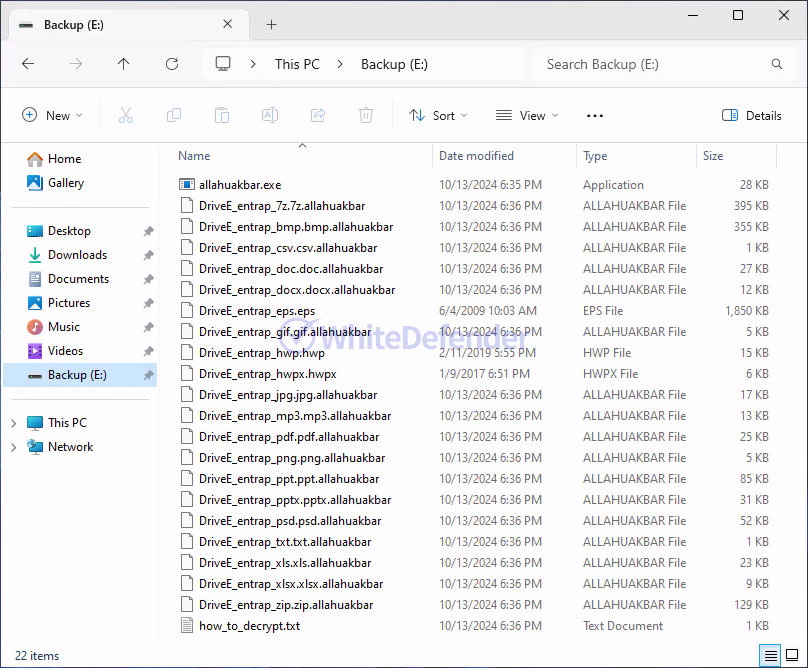
[Figure 7 Infection results]
White Defender Response
It also supports real-time automatic restoration of files that are encrypted before the malicious actions and blocking of WhiteDefender ransomware.
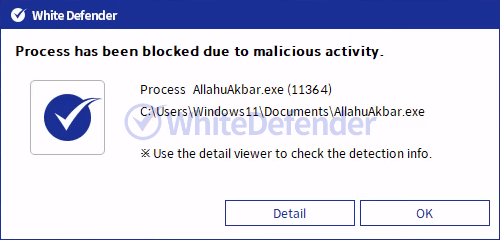
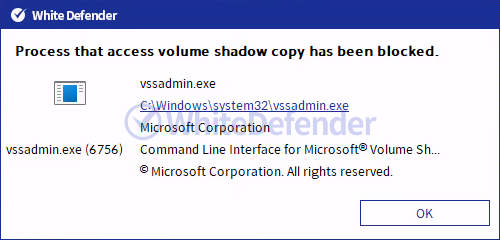
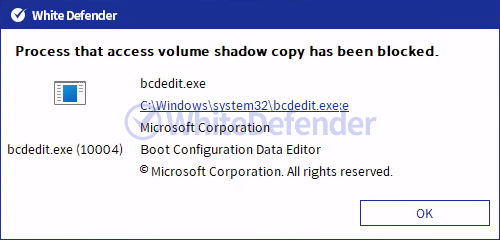
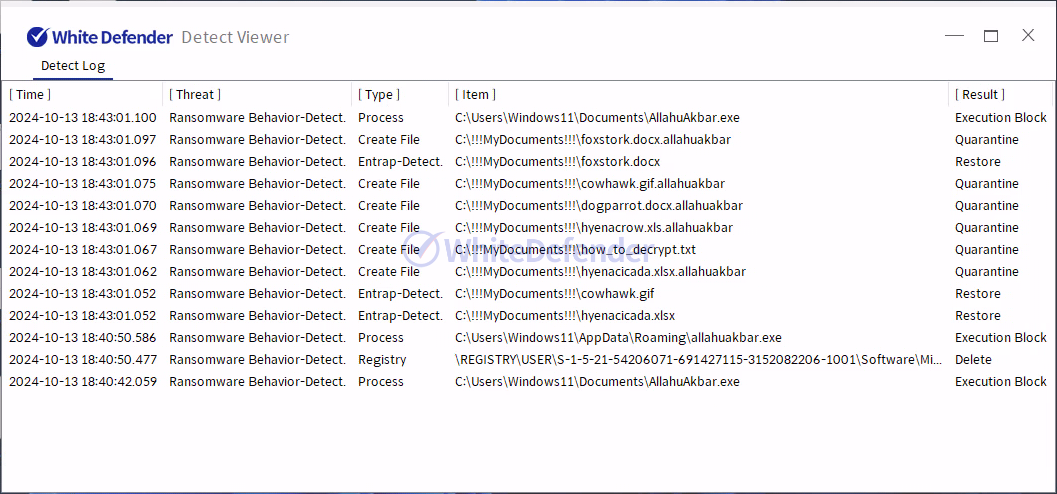
[Figure 8 Blocking Message]
Go watch AllahuAkbar blocking video

- Previous post
- No previous posts
- next post
- Elons ransomware

